July 10, 2025
 by Soundarya Jayaraman / July 10, 2025
by Soundarya Jayaraman / July 10, 2025

Ever feel like every MDR provider is promising “round-the-clock protection” but no one tells you what that actually looks like at 2 a.m. during a live ransomware incident?
Same. I’ve spent the last two years researching and writing about cybersecurity, covering everything from zero trust to threat intelligence, and I’ve had countless conversations with security leads, analysts, and IT teams stuck in alert fatigue.
One thing they all want? A partner, not just a product. So I decided to cut through the buzzwords and evaluate 15+ vendors to identify the top MDR providers who actually deliver when it matters most. Not just fast SLAs and shiny dashboards, but hands-on help when you’re short-staffed, and proactive threat hunting when your in-house team’s swamped.
If you're in the market for MDR, chances are you already know the stakes. Whether you're battling resource constraints, dealing with executive pressure to prove ROI, or just trying to avoid becoming the next breach headline, this guide is for you.
I’ve broken down what truly sets the best MDR services apart, from service quality and analyst access to how they handle escalation, onboarding, and integration with your existing stack.
Let’s get into the top MDR providers that earned my confidence, impressed many G2 users, and might just win your team’s trust too.
| MDR service provider | Best for | Standout feature | Pricing |
| Huntress Managed EDR | Small businesses with limited IT staff | 24/7 SOC with fast detection, guided remediation | Custom pricing |
| Sophos MDR | Mid-market and enterprise seeking layered protection | 24/7 SOC with fast detection, guided remediation, | Custom pricing |
| Arctic Wolf | Organizations needing concierge-style support | Named concierge security team (CST) with proactive guidance | MDR Basic Monitor (up to 100 users with MDR) costs $44,000 per year, according to AWS Marketplace data |
| ThreatDown | SMBs and MSPs seeking automation + SOC | Transparent pricing bundles and ransomware rollback built into core plans | Starts at $ 345 per year for 5 devices |
| Blackpoint Cyber | MSPs and SMBs needing quick, aggressive response | Direct call-in support and live containment actions without extra approval steps | Custom pricing |
| Red Canary | Security-mature teams that want deep visibility | Flexible telemetry collection from existing EDR tools plus clear analyst context on every alert | Starts at $120 per endpoint/year (User accounts $100/year, cloud resources $250/year, network $20/year), according to AWS marketplace data. |
*These MDR providers are top-rated in their category, according to G2 Grid Reports.
Outsourcing security isn’t new. I’ve seen companies rely on managed security service providers (MSSPs) since the late ’90s. But MDR is a different breed. Unlike traditional MSSPs that mostly forward logs and alerts, MDR actually helps you figure out what’s happening and what to do next. It combines technology with real human analysts who detect, investigate, and respond to threats in real time.
For lean, overworked security teams, that shift from passive monitoring to hands-on response is defining, and I’ve come to really appreciate it more given the nature of security incidents these days. 88% of ransomware attacks occur outside normal business hours, and nearly 4.75 million cybersecurity staff are needed to fill the workforce gap today.
What surprised me most as I compared MDR providers is how similar they sound, until you look closer. “24/7 SOC,” “threat hunting,” “real-time response” — it’s all on the website. But what actually separates the great from the good is the experience: how fast they act, how well they understand your environment, and how often you’re left guessing.
The best managed detection and response software don’t just integrate with your stack. They integrate with your team. And that makes all the difference.
I started with G2’s Grid Reports, my go-to source for real, unbiased user feedback, to build a shortlist of best MDR services. I looked at a mix of well-established leaders and emerging players with strong ratings.
Since MDR is a high-touch, always-on service, most providers offer demos but not free trials. So I focused on researching each product’s technical capabilities, from supported integrations to response playbooks, and dug deep into user reviews to understand what real users say about their everyday experience and outcomes.
When I couldn’t try or demo a platform firsthand, I consulted cybersecurity professionals with direct experience and cross-referenced their insights with G2 feedback.
To add context, I used AI tools to analyze hundreds of G2 reviews. It helped me spot consistent strengths like fast response and analyst support, and red flags like alert fatigue or poor integrations.
The screenshots featured in this article are a mix of visuals taken from G2 vendor pages and publicly available product materials.
Once I narrowed down the top MDR vendors, I focused on the technical capabilities, operational strengths, and hands-on value that make a provider stand out. Here are the key criteria I used to evaluate them:
The list below contains genuine user reviews from the platform software category. To be included in this category, a solution must:
*This data was pulled from G2 in 2025. Some reviews may have been edited for clarity.
Huntress Manager EDR quickly made its way to the top of my list of MDR service providers, and it wasn’t hard to see why. From the moment I looked at it, it was clear this wasn’t just another EDR tool with MDR slapped on.
One of the first things I noticed? Deploying Huntress is refreshingly simple. Whether you’re installing it via a script or using your RMM, it’s quick, efficient, and doesn’t leave you guessing. No bloated onboarding process. Just a lightweight agent that gets to work almost immediately without hogging system resources. In fact, Huntress EDR is often regarded as some of the best MDR software for small business security.
G2 Data also says the same thing. The platform consistently scores well above average for ease of use (96%) and ease of setup (97%), making it one of the most user-friendly MDR software options out there, especially for small or mid-sized businesses. And for security teams that are lean or stretched thin, that simplicity means a faster path to protection.
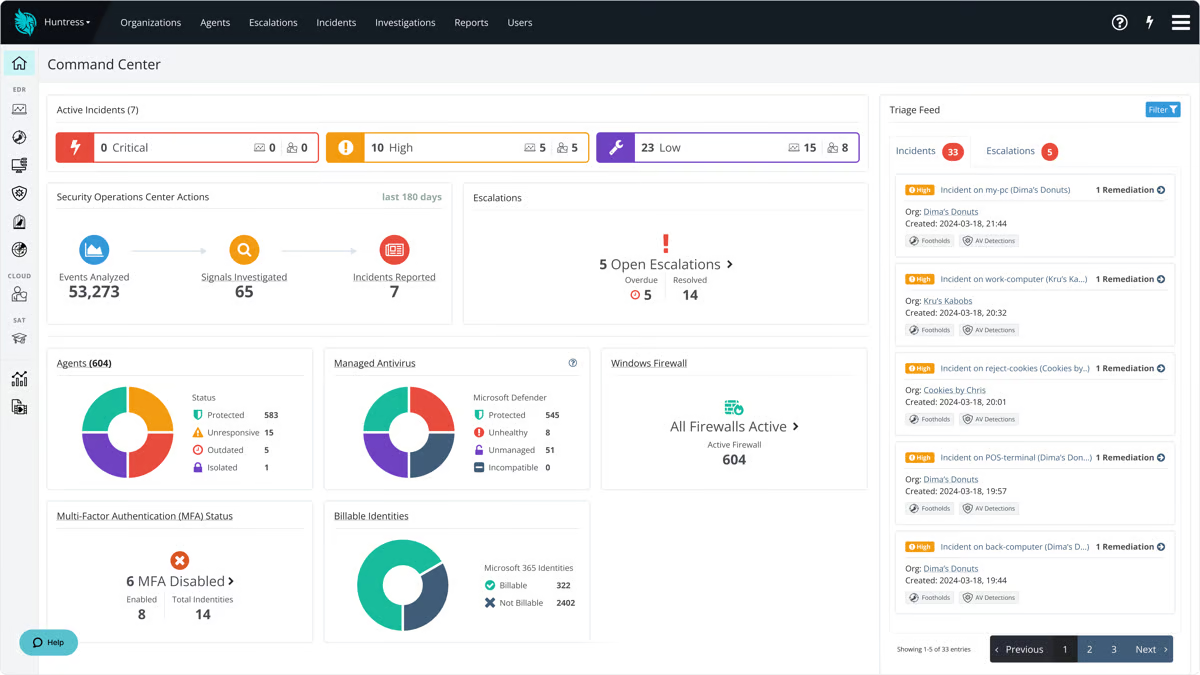
Where Huntress shines for me is the fully staffed 24/7 Security Operations Center (SOC) that actually watches your back. This isn’t some “set it and forget it” software. If something’s off, real analysts review it, investigate it, and send actionable reports.
The praise from users is also loud and consistent: nearly every review mentioned how responsive the team is and how effective the platform is at real-time threat detection. In fact, users rated its 24/7 support, proactive threat hunting, and rapid response time at 96% and above, which isn’t just impressive; it’s one of the category-leading scores.
Another standout I saw? Ransomware canaries. This is probably one of my favorite features. Basically, Huntress plants decoy files across your environment. If ransomware starts encrypting them, it triggers an instant alert. No more waiting until half your network is locked down. It's clever and simple, and it works.
That said, a couple of things stood out in user feedback. First, if your organization is heavy on Macs, you’ll want to plan ahead. MacOS deployment with Huntress tends to be more hands-on than Windows, especially when it comes to permissions and configuration. Still, I liked that Huntress is upfront about this and provides clear documentation to guide teams through the process, something users consistently called out in a positive light.
There were also a few lighter mentions across G2 reviews, such as occasional noisy alerts during busy periods or a desire for more customization in reporting. Generally, these didn’t come up often and were noted as minor improvements that were needed.
Would I recommend it? Absolutely. If you’re an IT lead at a small business, an MSP juggling multiple clients, or even a startup with limited internal security resources, Huntress delivers.
"As a small MSP, it is comforting knowing that I have Huntress Labs Managed MDR installed and protecting my clients' computers. Their support is as good as any I've seen. Most importantly, knowing if something should happen, I have their highly experienced SOC at the ready to assist in remediating the issue.
Unlike some other products I tested, Huntress is excellent about keeping a low profile and controlling the amount of noise. It was surprisingly easy to implement. I also very much like their dashboard, which makes it easy to monitor the security health of my clients' computers. I'm happy with my decision to go with Huntress MDR and have recently begun rolling out their ITDR module to my customers."
- Huntress Managed EDR Review, Richard G.
"Huntress was a little slow on getting MAC compatibility working, they were upfront about it and had a realistic timetable, but it still took a bit."
- Huntress Managed EDR Review, Jacob S.
MDR tools often work best when paired with a strong endpoint detection and response (EDR) foundation. Explore our in-depth guide to the best EDR software to compare vendors, see reviews, and understand how EDR fits into a layered security strategy.
Sophos MDR is one of those names you hear over and over, whether you’re talking to a lean IT team at a midsize business or a security consultant cleaning up after an incident. So I wanted to see for myself whether the reputation matched the reality.
What stood out to me pretty quickly was how Sophos approaches managed detection and response less like a bolt-on service and more like an evolution of their entire platform.
If you’re already using Intercept X, Sophos Firewall, or their cloud security tools, Sophos MDR integrates almost seamlessly. You get a single, unified view in Sophos Central instead of juggling multiple consoles or fragmented alerts.

Even if you rely on third-party data sources like Microsoft 365 or AWS, the MDR team can still monitor and respond effectively; it just takes a bit more setup to connect everything. Either way, the experience is designed to feel cohesive, not like an add-on pasted over your environment.
That tracks with what users say. The satisfaction rating of Sophos MDR stands at 94–95% for ease of setup, ease of use, and ease of admin.
Sophos gives you a clear choice in how incidents are handled by its MDR Ops team, which I think is one of its strengths. You can pick Collaborate mode, where the MDR team investigates threats and keeps you in control of any containment actions, or Authorize mode, where they proactively neutralize threats and loop you in afterward. It’s a practical model that feels more flexible than what you get with many MDR providers, where you either have to do everything yourself or hand over full control by default.
I also noticed Sophos consistently gets strong marks for 24/7 support, proactive threat hunting, and rapid response time, with satisfaction ratings above 95%.
I found the weekly and monthly reports valuable. They give you a clear snapshot of threat activity, response actions, and overall health across your environment, so you’re not left wondering what’s happening behind the scenes.
However, quite a few G2 reviewers mentioned that report customization feels a little limited, especially if you need granular or compliance-specific details beyond the defaults.
Also, I did see a few comments about alert tuning and false positives. To combat this issue, some teams mentioned spending extra time reviewing detections to be sure they were actionable. To be fair, false positives are pretty common across most MDR solutions, so I wouldn’t consider them unique to Sophos.
Overall, if you’re searching for an MDR service provider that balances robust coverage with options to stay hands-on (or let them take over when needed), Sophos MDR makes a strong case. I’d recommend it to midsize and enterprise security teams, especially in industries where compliance and fast escalation matter.
"Since implementing Sophos MDR, we have experienced a significant improvement in our security posture. Sophos MDR actively monitors our network and login activity, and they have alerted us to suspicious behavior on our Entra account within just one to two hours of compromise. Moreover, they provide clear, step-by-step remediation guidance, which has been invaluable. For our on-premises infrastructure, we’ve configured the system to allow Sophos to autonomously address any issues they detect."
- Sophos MDR Review, Stephen S.
"While Sophos MDR is overall a strong solution, there are a few areas for improvement. Sometimes the alerts can be a bit too frequent or not fully prioritized, which can lead to alert fatigue. Additionally, the response time from the MDR team, while usually fast, can occasionally be slower during non-critical issues. Pricing might also be a concern for smaller organizations, as the service can become costly depending on the number of devices or endpoints."
- Sophos MDR Review, Alan L
If you’re exploring ways to strengthen your security without building an entire SOC from scratch, Arctic Wolf’s Managed Detection and Response (MDR) is worth a look. I’ve spent some time digging into how the MDR service provider works, and here’s what stood out to me.
When you sign up, you’re paired with what they call a concierge security team (CST), basically, a group of security pros who become an extension of your IT staff, similar to what Huntress and Sophos MDR provide. They help you install their sensors, agents, and cloud connectors to monitor your cloud environment.
From what I’ve read, that concierge approach isn’t just a marketing term. In G2 reviews, users consistently rated Arctic Wolf highly for 24/7 support, proactive report alerts, and rapid response time, with satisfaction scores in the 95–98% range.

Several teams mentioned that having a predictable point of contact made it much easier to stay ahead of issues, especially in industries like healthcare, finance, and manufacturing, where compliance requirements and incident timelines can get complicated quickly.
The ease of setup and ease of administration were also a bright spot, with ratings that hovered around 92%, which is impressive given that MDR deployments usually come with plenty of moving parts. Many G2 users described the onboarding process as structured and thorough, and said the day-to-day experience didn’t require constant oversight once everything was in place.
One of the other things I kept coming across in reviews was how strong the visibility is across your environment once Arctic Wolf is fully set up. From everything I’ve read, the platform seems to give teams a level of clarity they didn’t have before.
Whether it’s spotting trends in endpoint behavior, correlating logs from different tools, or just knowing where to focus first when something looks off, a lot of users said it made them feel more confident about what was happening across their network. For smaller teams that want to know exactly where they stand in terms of security, that kind of visibility can be a huge advantage.
Of course, there are a few trade-offs to be aware of. One theme I noticed in reviews is that Arctic Wolf isn’t cheap, especially for smaller organizations or public sector teams watching their budgets closely. Many users said the value was worth it, but the price can be a hurdle.
Another thing that came up was the portal and dashboards, which some teams felt could be more user-friendly or flexible. A few reviewers mentioned that navigating all the data takes some getting used to and that they’d like more customization options to sort and prioritize what matters most.
That said, if you are looking for an MDR solution that delivers strong support and a high-touch experience, Arctic Wolf is easy to recommend. It's consistently recognized among the leading MDR services for financial services firms, healthcare, and other regulated industries that need predictable support and strong visibility.
"Arctic Wolf's ability to gain broad visibility in my environment helps me with the awareness that I may not have had otherwise. Also, I love the Concierge Security Team working with me, reviewing my environment to help find and close gaps."
- Arctic Wolf Review, Joe M.
"The only real downside is cost. However, they are not far off from other vendors in this area."
- Arctic Wolf Review, Matthew K.
MDR services strengthen threat detection, while penetration testing tools help identify vulnerabilities before attackers do.
I’ve known Malwarebytes for quite some time, but I wanted to see how ThreatDown, offered by the company, holds up when you look past the brand name and focus on what users actually experience day to day.
The thing I appreciate is how upfront ThreatDown is about pricing. Honestly, the pricing part alone is a huge plus for me. So many MDR vendors make you jump through hoops just to figure out what you’ll pay, but ThreatDown lays it all out clearly. For teams that don’t have time to negotiate back and forth, that level of transparency around packages is refreshing.
I spent some time looking into what you actually get in each plan. Even the Advanced bundle includes some solid capabilities like ransomware rollback, EDR, patch management, firewall management, and managed threat hunting, which is a lot more than basic antivirus. If you step up to the Elite plan, you get 24/7 managed threat detection, hunting, investigation, and remediation, which feels closer to a true around-the-clock SOC experience.
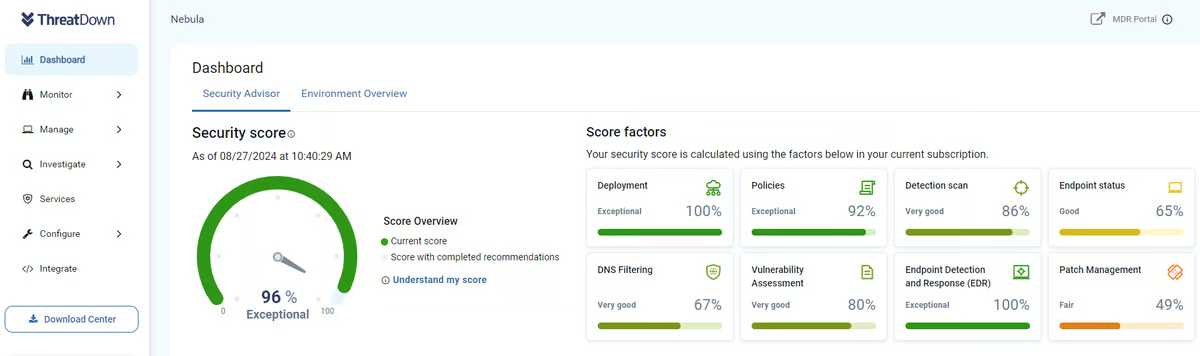
ThreatDown delivers the core capabilities you’d expect from the MDR: continuous monitoring, proactive threat hunting, and incident response support. But what seems to resonate most with customers and honestly stood out to me as I read through reviews is how the service makes the advanced threat detection approachable.
Instead of forcing your team to become experts in managing detection rules or correlating logs, ThreatDown’s analysts do the heavy lifting behind the scenes. They collect and analyze telemetry across your environment, identify suspicious behaviors, and escalate confirmed threats with clear, actionable guidance. I came across multiple examples where users said this approach cut down on alert fatigue and helped them focus on real issues instead of spending hours sorting through noise.
Features like rapid response time (93% satisfaction), proactive report alerts (91%), and automated investigation (91%) were all among the highest-rated areas on G2. Even its automated remediation capabilities are rated 90%, showing that customers consistently find value in ThreatDown’s ability to quickly neutralize threats without constant manual intervention.
And if you need to tailor your reporting, 86% of users reported being satisfied with the platform’s customizable reports, according to G2 Data.
That said, there were a couple of drawbacks worth noting. Some users described inconsistent customer support, saying their experience depended a lot on which engineer handled their case, which could be challenging during time-sensitive incidents. I also saw feedback about communication gaps, like not always getting clear updates when new features were introduced or when the rebrand happened.
On the whole, though, most teams still rated ThreatDown highly for day-to-day reliability and felt it delivered strong protection without overwhelming complexity.
If you’re looking for an MDR solution that prioritizes speed, simplicity, and a clear path to operational security, ThreatDown is worth considering.
I’d especially recommend it for IT teams in mid-sized organizations, manufacturing, government, or education, where you need strong coverage without a steep learning curve. For many teams, it’s a user-friendly and adaptable MDR tool for businesses that want strong protection without the complexity of enterprise platforms.
"ThreatDown is very user-friendly with an intuitive interface that makes threat detection and response straightforward. The tool provides quick insights into security threats, simplifying my workflow significantly. Your paying for a quality product."
- ThreatDown Review, Carlos P.
"Support from the vendor is rarely required, but if you ever need it, be patient. First-level support personnel are very friendly and willing to help, but they have limited knowledge. Second-level support personnel are great and capable of solving any problems, but they take a long time to respond."
- ThreatDown Review, Yuri K.
Blackpoint Cyber kept coming up as a standout, especially for IT and security-focused companies that need proactive coverage without a lot of extra complexity. From everything I’ve read, it has built a strong reputation not just for managed detection, but for combining that with fast, hands-on threat hunting.
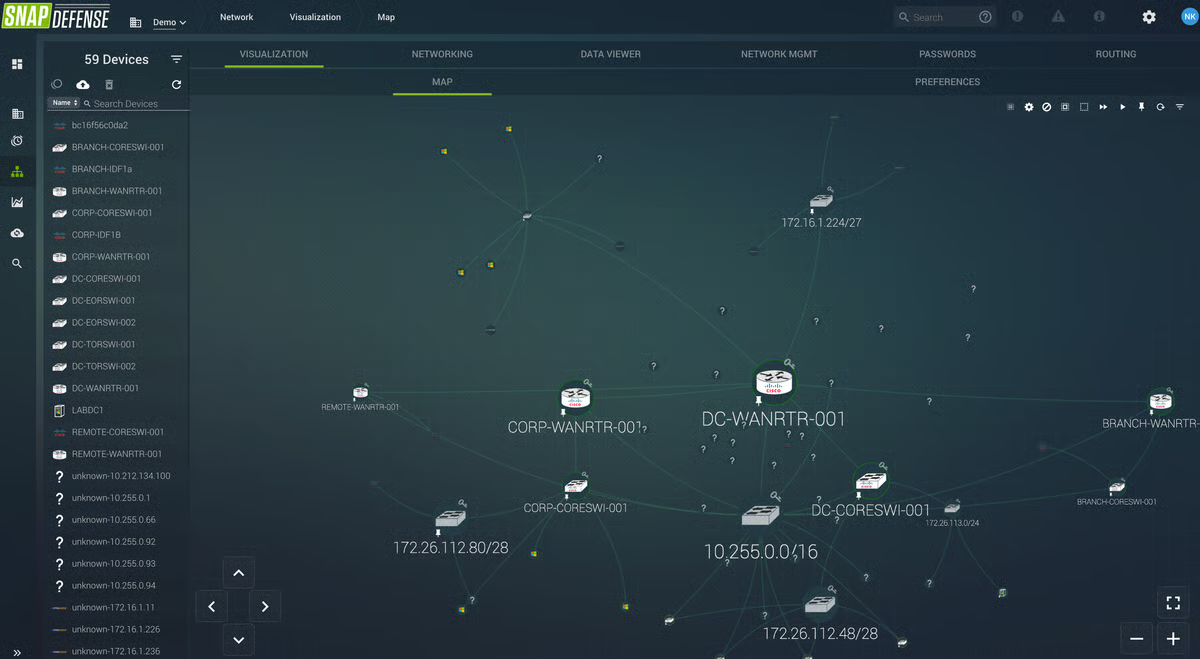
I was struck by how unapologetically focused Blackpoint is on stopping threats fast, not just detecting them. In a lot of MDR offerings, you see vendors highlight visibility and alerting as the main selling points. Blackpoint certainly does that, but what makes it stand out is how much emphasis it puts on live response and containment baked right into the service.
One thing I found especially notable is that you can call in directly if something urgent happens, instead of relying only on tickets or email updates. While plenty of other MDR providers offer containment and remediation, Blackpoint’s approach feels a bit more personal and immediate. You can actually talk to someone in real-time while they kill malicious processes or remove persistence, which can make a big difference when every minute counts.
At the core of Blackpoint’s approach is its proprietary live network map — a real-time visualization of all the hosts and user sessions in your environment, showing exactly how devices and accounts are connected. That level of visibility pairs well with their focus on hands-on response.
Another strong point is how Blackpoint handles 24/7 monitoring without burdening customers with excessive configuration. From what I’ve gathered, most of the detection logic and workflows are prebuilt and tuned by their team, so even smaller security teams can deploy them without spending weeks setting up custom detection rules. And the G2 Data backs this up. The satisfaction ratings for ease of use and setup hover around 94–96%.
I also noticed the platform is especially popular with companies in IT services and network security, which makes sense given how much focus Blackpoint puts on real-time containment and keeping friction low.
Overall, most users seemed genuinely happy with how Blackpoint delivers on speed and proactive protection, and many reviews praised how hands-off the day-to-day management feels. That said, there were a few limitations that were shared by users on G2.
I came across feedback about pricing, with some reviewers saying it can feel expensive for smaller firms or budget-conscious organizations. Even so, most people agreed that the combination of live response and strong support made it worth the investment, especially if you value a solution that takes real action when something goes wrong.
I also came across some feedback noting that the web portal has room for improvement, with a few users mentioning that the experience could be smoother. But these were far and few in between, and some also noted that recent updates have made it better.
From everything I've seen, Blackpoint Cyber is worth serious consideration if you value real-time containment, operational simplicity, and a response-oriented mindset.
Along with Huntress, and Sophos MDR, Blackpoint Cyber has earned a reputation as one of the most reliable MDR software solutions for IT companies. So, I’d definitely recommend Blackpoint to IT service providers, MSPs, or any mid-sized business.
"Blackpoint is great with identifying suspicious activity and making good decisions on locking something down to prevent compromises. They have been very quick with their detections, and it is always a human who reaches out to make sure we acknowledge the issue and take over with the next steps.
The incident response reports are great and very similar to the ones my team makes, which really cuts down on duplicated efforts. We were able to deploy Blackpoint quickly and easily. Blackpoint has an integration with our PSA, allowing us to automatically keep license counts in sync with our agreements. We use Blackpoint now exclusively because they have quickly built trust with our team."
- Blackpoint Cyber Review, Justin H.
"BlackPoint Cyber offers strong solutions, but some may find the services costly, complex for smaller teams, and occasionally challenging to integrate or scale effectively."
- Blackpoint Cyber Review, May Anne Y.
I’ll be honest — Red Canary was a bit of a new discovery for me, and after looking into it, I’m glad I didn’t overlook it just because it doesn’t have the biggest brand footprint.
Underneath the name (which sounds more like a code name than a security company) is an MDR platform that consistently gets praise for proactive detection, clear guidance, and a genuinely helpful support team.
Something that impressed me is how Red Canary emphasizes context and clarity over volume, making it easier to see how each detection impacts your environment. In the G2 reviews I read, users often mentioned that analysts don’t just say, “Here’s a detection”—they also explain why it matters and walk you through what to do about it.
That blend of detection, investigation, and education feels like a big part of why teams trust the service, especially in industries like financial services and manufacturing, where response time and clarity are critical.

Another detail that makes Red Canary stand out is how it manages endpoint telemetry collection. Rather than relying only on its own lightweight agent, Red Canary can also leverage telemetry from tools you already have in place. For example, integrating with Microsoft Defender or other EDR solutions.
From everything I’ve gathered, that flexibility can save you a lot of time if you’re not interested in replacing your entire stack just to get MDR coverage.
That being said, I did notice some areas where users felt there was room for improvement. Some teams mentioned delays in alerts or getting more notifications than they expected, which could make it harder to zero in on the highest-priority issues.
Others said they’d like to see more integrations beyond what’s currently available, especially to connect Red Canary more deeply with their broader security stack. To be fair, Red Canary has shared that expanding integrations is on their roadmap, and most reviewers still felt the service delivered a lot of value overall.
So, from everything I’ve seen, it’s a solid fit for mid-sized companies and security-focused teams that want enterprise-grade detection without a lot of extra baggage.
Please note that Red Canary was recently acquired by Zscaler.
"Implementation, ease of use, and customer support are 3 of the main things that Red Canary goes above and beyond with. In the tech industry, we've all experienced very unhelpful support, and when it comes to our security posture, it allows us to "set and forget" a lot of the triggers that we see on a daily basis. Their team has been instrumental in steering us towards success, whether it's monthly meetings, actual malicious triggers, or just to chat about upcoming security changes."
- Red Canary Review, Andrew S.
"There is some lag between the alert in MDE and when RC responds."
- Red Canary Review, John C.
Explore the best antivirus software you can pair with your EDR and MDR for complete protection.
Now, there are a few more options, as mentioned below, that didn't make it to this list but are still worth considering, in my opinion:
Got more questions? G2 has the answers!
The best-reviewed managed detection and response software vendors, based on G2 Data, include:
The best choice depends on your environment, budget, and existing tools.
When comparing MDR providers, consider these key criteria:
Deployment timelines can vary:
Most MDR service providers offer onboarding assistance to accelerate the process, including sensor deployment, playbook configuration, and alert tuning.
MDR pricing often bundles:
Additional costs can include:
Always ask for a detailed proposal to understand what’s covered and what’s extra.
Yes. Many MDR services are designed to integrate with popular EDR and SIEM solutions, such as CrowdStrike, SentinelOne, Microsoft Defender for Endpoint, Splunk, and IBM QRadar.
If you already have these tools deployed, MDR providers can often leverage them instead of replacing them, reducing costs and deployment time.
MDR is a managed service. Security experts monitor, detect, and respond on your behalf. XDR is a technology platform, a unified toolset aggregating telemetry across endpoints, cloud, identity, and network to improve detection.
Some MDR providers deliver services on top of their own XDR platforms, combining automation with human expertise. If you lack in-house staff to monitor XDR, MDR is often the better fit.
Startups should strongly consider MDR if they handle customer or financial data, have compliance requirements, lack in-house security expertise, or are growing beyond 25–50 employees. MDR provides 24/7 monitoring and expert response without the need for a full security team.
If you’re a very small team with no sensitive data and strong security practices (like MFA and endpoint protection), you may be fine delaying MDR until you scale.
Some of the best MDR services for startups are CrowdStrike Falcon Complete, SentinelOne Vigilance Respond, Arctic Wolf MDR, Sophos MDR, Red Canary, and Huntress MDR.
Before choosing a provider, ask:
After researching dozens of MDR providers, studying user reviews, and comparing capabilities, I’ve come to see that the “best” solution isn’t always the one with the most sophisticated tools. It’s the one that aligns with your company’s scale, security maturity, and resources.
No matter your size or industry, the options covered here reflect expert-recommended MDR software for your company, selected based on real-world feedback and proven performance
But ultimately, MDR isn’t just about outsourcing security tasks. It’s about building a partnership with experts who can help you shift from a reactive mindset to a more proactive, resilient approach.
Even if you’re starting with limited resources, the right provider can meet you where you are and guide you forward step by step. Investing time upfront to talk to references, compare real-world experiences, and match each vendor’s strengths to your environment can turn MDR into a genuine strategic advantage rather than just another line item on your budget.
Still on the hunt? Explore our categories of system security tools to find the best fit for your security needs.
Soundarya Jayaraman is a Senior SEO Content Specialist at G2, bringing 4 years of B2B SaaS expertise to help buyers make informed software decisions. Specializing in AI technologies and enterprise software solutions, her work includes comprehensive product reviews, competitive analyses, and industry trends. Outside of work, you'll find her painting or reading.
If there’s one thing I’ve learned from researching cybersecurity tools, it’s this: every...
 by Soundarya Jayaraman
by Soundarya Jayaraman
Some years back, I witnessed a magnanimous security breach of a trademarked company website in...
.png) by Shreya Mattoo
by Shreya Mattoo
After three years of writing about cybersecurity, I’ve seen IT admins and business owners...
 by Soundarya Jayaraman
by Soundarya Jayaraman
If there’s one thing I’ve learned from researching cybersecurity tools, it’s this: every...
 by Soundarya Jayaraman
by Soundarya Jayaraman
Some years back, I witnessed a magnanimous security breach of a trademarked company website in...
.png) by Shreya Mattoo
by Shreya Mattoo


