Recently, I couldn’t log into a critical system at work, and after what felt like a hundred failed attempts, I turned to the IT team for help. Don’t we all, right?
They mentioned they’d been using one of the best identity verification software to manage access and couldn’t stop raving about how it made security easier and more reliable.
Naturally, I thought, "What’s all this hype about?" Why was it so crucial that I couldn’t just log in after a few tries? And why was I being asked to authenticate myself every single time?
Curious (and a little frustrated), I decided to dig deeper myself. So, I Googled it, because, let’s face it, we go there for everything (we even use GPT now, apparently!). But I was bombarded with conflicting information that left me even more confused.
That’s when I turned to G2 reviews to get a clearer picture of what these tools were actually offering. If you’re in IT or security, you know that identity verification software does far more than just secure logins. It helps prevent fraud, streamlines onboarding, and strengthens overall security protocols.
Based on real user reviews, I’m sharing my findings to help you cut through the noise and find the right identity verification software for your organization.
7 best identity verification software: My picks for 2025
-
Incode: Best for fast, seamless biometric identity verification
Known for high-speed biometric checks and a smooth user experience. (pricing available on request)
-
Sumsub: Best for compliance and fraud prevention
Specializes in automated compliance checks and fraud prevention across industries. ($1.35 per verification)
-
iDenfy: Best for AI-powered accuracy and speed
Delivers AI-driven identity verification with a strong focus on precision and efficiency. (pricing available on request)
-
Mastercard Identity Review 360: Best for secure digital payments
Integrates advanced fraud detection and security features to strengthen digital payment systems. (pricing available on request)
-
Onfido: Best for remote document and biometric verification
Offers secure identity checks with both document and biometric verification. (free trial available, pricing for the advanced plan on request)
-
SheerID: Best for verifying targeted consumer groups
Tailor verification for groups such as students, military personnel, and first responders. (pricing available on request)
-
Ondato: Best for customizable, compliance-focused workflows
Provides flexible identity verification built for regulatory compliance and easy business integration. (approximately $0.93 per verification)
* These identity verification tools are top-rated in their category, according to G2's Spring 2025 Grid Report. I’ve also added their pricing to make comparisons easier for you.
My top 7 identity verification software recommendations for 2025
The stakes keep rising. The digital ID verification checks are forecast to reach 86 billion in 2025, and why wouldn't they, when the average identity fraud rate across verifications was 2.5% in 2024.
The best identity verification software simplifies the process of securely authenticating users while reducing fraud and enhancing security. With features like biometric authentication, real-time identity checks, and fraud detection, these tools help businesses proactively prevent unauthorized access, ensuring a seamless and secure experience for both businesses and users.
How did I find and evaluate the best identity verification software?
By analyzing G2 reviews and G2’s Grid Reports, I thoroughly understood each identity verification tool's features, ease of use, and overall value. I relied on verified reviews from IT professionals with hands-on experience to confirm my findings.
I also leveraged AI to identify patterns in user feedback, ensuring I captured a diverse range of perspectives on the software’s effectiveness in preventing fraud, streamlining authentication processes, and enhancing security. The visuals in this article may include a mix of screenshots from G2 reviews and vendor-provided images.
By combining insights from G2 with expert feedback, I’ve compiled a list of the best identity verification software to help you choose the right solution for your organization’s needs.
What makes identity verification software worth it: My opinion
When evaluating the leading identity authentication software solutions, I focus on several key features to determine their effectiveness for IT and security teams:
- User authentication efficiency: A good identity verification tool should streamline the login and authentication process, minimizing friction for legitimate users while maintaining high security. I assess how quickly and seamlessly the software can authenticate users via various methods like biometrics, two-factor authentication (2FA), or device recognition. The system should be fast and intuitive, reducing the number of steps without compromising security.
- Fraud prevention and detection: Identity verification software aims to prevent identity theft. I evaluate how the software uses advanced algorithms, AI, or machine learning models to detect fraudulent activities in real time. To verify authenticity, does it cross-check multiple data points like government IDs, social media profiles, and email addresses? I also assess whether the system provides adaptive measures, such as challenging users with extra layers of authentication if it detects suspicious activity.
- Compliance and regulatory standards: A reliable identity verification solution should comply with industry standards and regulations such as GDPR, CCPA, and KYC/AML requirements. I check whether the software provides built-in compliance features, ensuring businesses stay aligned with data privacy laws and regulatory obligations. The ability to generate audit logs and reports for legal and audit purposes is another feature I consider crucial.
- Ease of integration: The best identity verification software should seamlessly integrate with your existing systems, such as customer databases, CRM platforms, or mobile apps. I test how easily the tool connects with other applications via APIs or pre-built integrations. A smooth, low-code implementation process ensures minimal disruption to business operations.
- Scalability and flexibility: As businesses grow, their identity verification needs can evolve. I evaluate how well the software scales to accommodate increased users or data while maintaining performance. Additionally, I assess the customization options available, like adjusting the authentication method for different user groups or integrating region-specific security requirements.
- Real-time updates and monitoring: Identity verification tools should offer real-time monitoring of user data and authentication events. I check whether the system provides dashboards that display live metrics and alert administrators to potential issues. The ability to track user verification status and gain insights into fraud patterns can help businesses act swiftly and efficiently.
- Offer multiple identity and credential verification methods
- Verify documents, such as ID cards
- Perform analysis on the data provided by the user to determine risk
This data was pulled from G2 in 2025. Some reviews have been edited for clarity.
1. Incode: Best for fast, seamless biometric identity verification
Based on my review of G2 user feedback, customer support consistently stands out as one of Incode’s strongest assets. I’ve come across multiple reviews where users describe the customer success team not just as responsive, but as proactive strategic partners. Many reviewers highlight the value of thoughtful, scenario-specific advice during both onboarding and later stages, like user flow modifications.
One detail I see frequently mentioned is how Incode's team helps customers understand the downstream impact of changes, enabling more efficient onboarding without compromising security. That level of consultative support is rare, and users clearly appreciate it.
Users often praise the tool’s real-world performance in age verification, estimation, and liveness detection. Several G2 reviewers recommend it for mobile app identity checks, noting its fast and accurate results even in low-light settings, with screen glare, or on budget smartphones.
Users often speak highly of the tool’s performance under real-world conditions about age verification. In fact, according to G2 Data, 100% of G2 users who mentioned online age verification highlighted this feature positively across reviews.
From what I’ve seen, G2 reviewers find this consistency to be a major advantage, especially for companies operating in less-than-ideal environments. The reliability of these features gives users confidence in their day-to-day operations.
According to many users, Incode’s proprietary biometric technology is a standout capability. Unlike vendors that rely on white-labeled solutions, Incode has built its models in-house, and G2 reviewers seem to value that.
I frequently see mentions of this, allowing users to connect directly with engineers when customizations are needed. The combination of innovation and technical access appears to be a winning formula for teams looking for flexibility and strong performance in biometric identity verification.
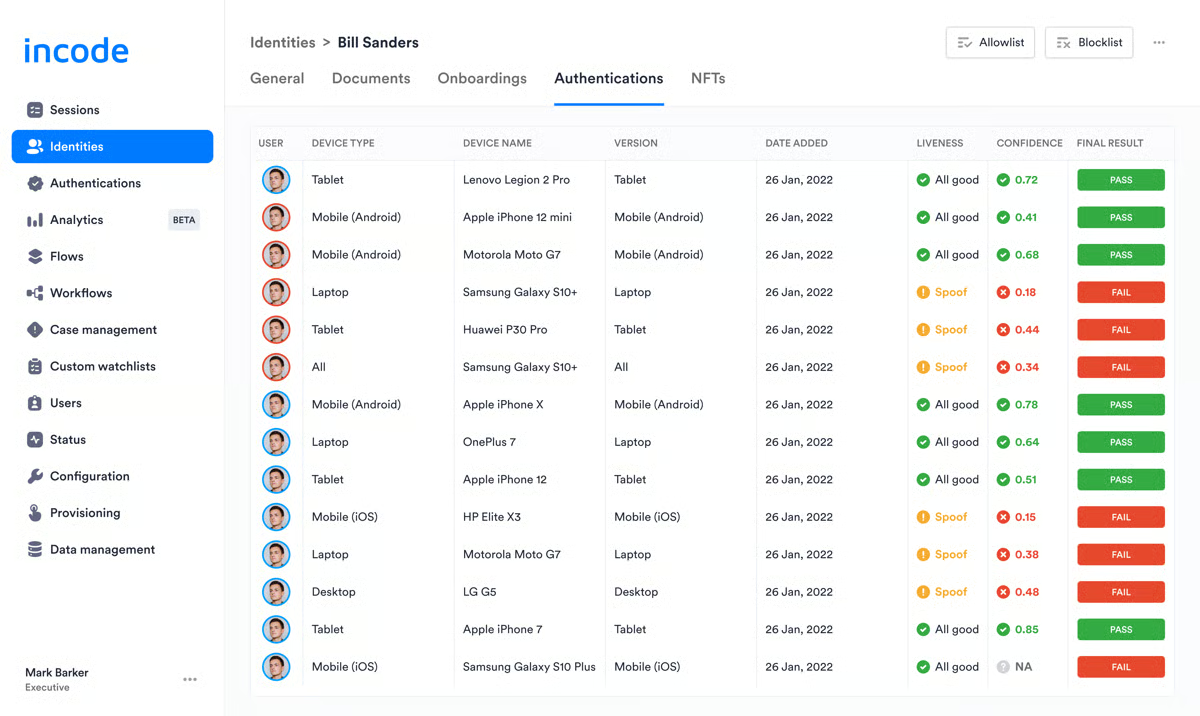
Looking at the broader review trends, I can see recurring themes in areas where users face challenges. One common concern is that identity verification introduces friction into the user experience. While several users acknowledge that Incode tries to minimize this, they also note that any added steps, however streamlined, can still slow down the process or increase drop-off rates. This added friction is something to keep in mind for teams with a high focus on user experience and speed.
I’ve also noticed G2 reviewers mentioning a steep learning curve for internal support teams. Alerts for suspicious activity are sometimes unclear, and users have expressed the need for better guidance on which actions require immediate attention. While teams eventually adapt by updating internal protocols, it’s not described as a plug-and-play experience. From what I’ve read, this adds time to onboarding and initial setup for support staff.
Finally, pricing is another area where feedback tends to be mixed. Multiple reviewers mention struggles with volume-based pricing, especially for smaller teams or newer deployments. I’ve seen calls for more flexible or entry-level pricing tiers to better accommodate startups or companies in early growth stages. The current model favors larger enterprises, leaving smaller teams to navigate higher-than-expected costs.
What I like about Incode:
- I’ve seen G2 users consistently praise the customer support team for being proactive and offering tailored onboarding help.
- I’ve read reviews where users highlight how well the tool performs for age verification, even in poor lighting or on low-end devices.
What G2 users like about Incode:
"Incode has provided a fully white-labeled solution for onboarding end users for some of my biggest clients. The technology is excellent, with one of the industry's lowest rates of false negatives, even outperforming companies that manually verify user identities. Incode has been an easy choice for us with no human error, a hands-on implementation team, and the best fraud prevention metrics!"
- Incode Review, Mario M.
What I dislike about Incode:
- I’ve noticed users pointing out that identity verification steps still add friction and may slow down user flow.
- I’ve encountered feedback where teams struggle with the alert system and mention a learning curve for internal support.
What G2 users dislike about Incode:
"The learning curve for our support team was a bit steep. Understanding the nuances of alerts for unusual activity took some time, and we had to adjust our response procedures as a result."
- Incode Review, Verified User in Retail
2. Sumsub: Best for compliance and fraud prevention
Based on the feedback I’ve gathered from G2 users, Sumsub’s user interface is frequently highlighted as a major strength. Many reviewers describe the platform as efficient, intuitive, and thoughtfully designed.
I’ve seen repeated mentions of how easy it is for teams to navigate the system without much training, even with the complexities involved in identity verification. The clean layout and logical workflows appear to significantly reduce the learning curve and help users save time during implementation and daily use.
From what I’ve read, seamless integration with existing systems is another widely appreciated element. Users often point out that they didn’t need to rework their internal processes to get started with Sumsub. According to G2 Data, 92% of G2 users specifically praise its integrations and SDKs, which support websites, mobile apps, POS solutions, and kiosks.
The API documentation is frequently praised for being clear and developer-friendly, and I’ve noticed a consistent theme around fast, smooth technical setups. G2 reviewers emphasize how this ease of integration helped them accelerate user onboarding and optimize verification processes.
According to G2 reviews, one standout capability is Sumsub’s frequent updates and product evolution. Users seem to really value the company’s commitment to rolling out new features and maintaining regulatory alignment. I’ve come across multiple reviews mentioning how these updates help companies stay ahead in compliance and security without switching platforms. For many, the platform’s agility and forward-thinking roadmap provide long-term confidence.
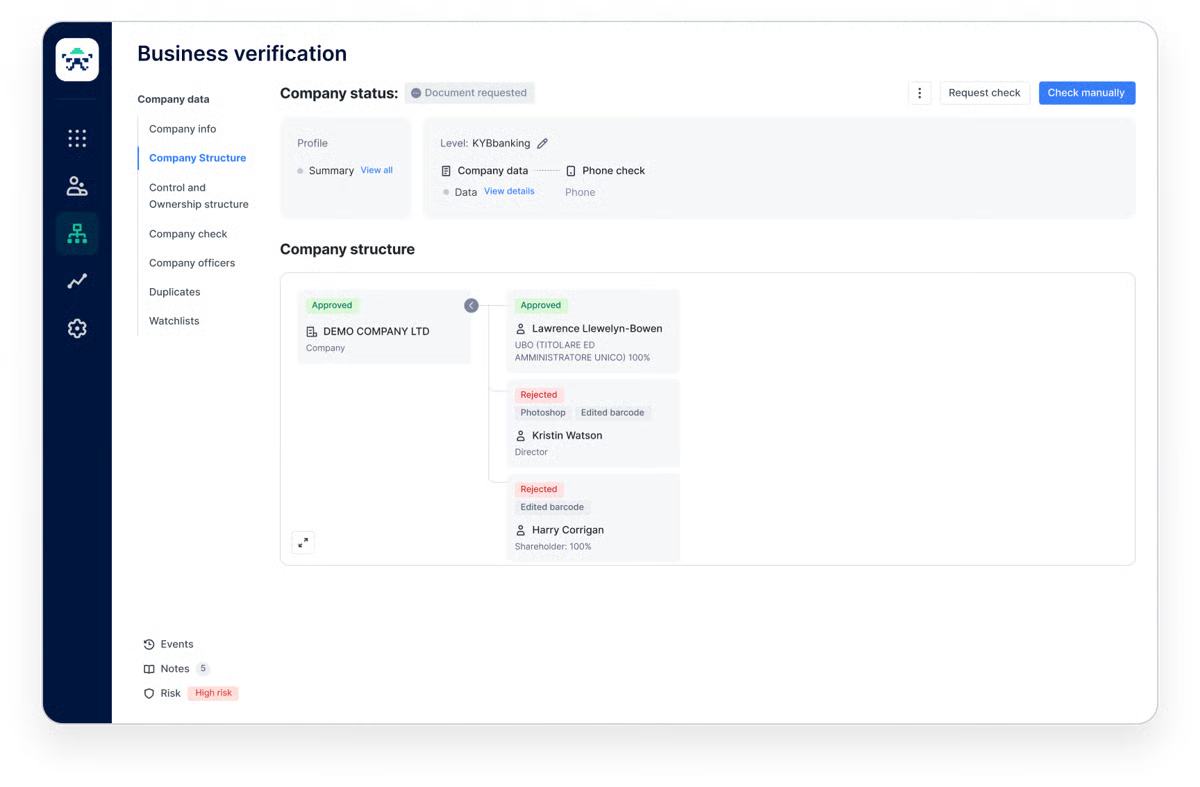
That said, looking at the broader review trends, I’ve noticed some users express frustration with delays during peak usage periods. While not a constant issue, it does show up in reviews as something that affects the overall onboarding experience.
These delays, though occasional, can disrupt the user journey and create operational slowdowns. Reviewers often suggest improvements in scalability to better handle verification volume during high-traffic times.
Another area where G2 users see room for improvement is documentation and learning resources. Multiple reviewers have mentioned struggles with onboarding newer or less technical team members.
While the platform itself is user-friendly, having more detailed tutorials, especially tailored to specific use cases, could ease the transition for new users. This seems to be a common request among teams aiming for faster internal adoption.
What I like about Sumsub:
- I’ve seen G2 reviewers frequently highlight Sumsub’s user interface for being intuitive and easy to navigate, even for teams with minimal training.
- I’ve noticed multiple reviews praising the seamless integration process, with users emphasizing how quickly they could set up and optimize workflows using the clear API documentation.
What G2 users like about Sumsub:
"The self-service nature and excellent documentation of SumSub’s services make it easy to integrate quickly and expand usage in more advanced ways over time. Their customer support is always available, providing swift and accurate responses to our inquiries."
- Sumsub Review, Alaa S.
What I dislike about Sumsub:
- I’ve come across feedback mentioning occasional delays during peak periods, which can slow down onboarding and disrupt operations.
- I’ve noticed users requesting more detailed documentation and tutorials, especially to help onboard less technical team members more efficiently.
What G2 users dislike about Sumsub:
"SumSub's advanced features can present a steep learning curve at first, and its pricing may be too high for smaller businesses or startups with limited budgets."
- Sumsub Review, Marius N.
3. iDenfy: Best for AI-powered accuracy and speed
From what I’ve seen in G2 reviews, iDenfy’s API documentation is often praised for being clear, thorough, and well-structured. Many users mention how this ease of integration helped their development teams implement the system quickly and without the need for external support. This is a recurring theme in feedback, where reviewers express satisfaction with how seamlessly the platform integrates into their existing systems, saving both time and resources.
A commonly appreciated element in user feedback is iDenfy’s pricing model. Several G2 reviewers highlight the cost-effectiveness of paying only for approved verifications. This structure allowed them to conduct thorough vetting without the concern of accruing unnecessary fees. Many users feel that this model gives them greater control over their budgets while ensuring they maintain a strong security layer, which is often cited as a key benefit.
Looking at the broader review trends, G2 users frequently mention iDenfy’s responsive support team as a standout feature. I’ve read multiple reviews where users describe their experiences with the support team as fast, detailed, and helpful. Many reviewers appreciate that their queries are met with expert-level responses, which helps resolve issues without delays.
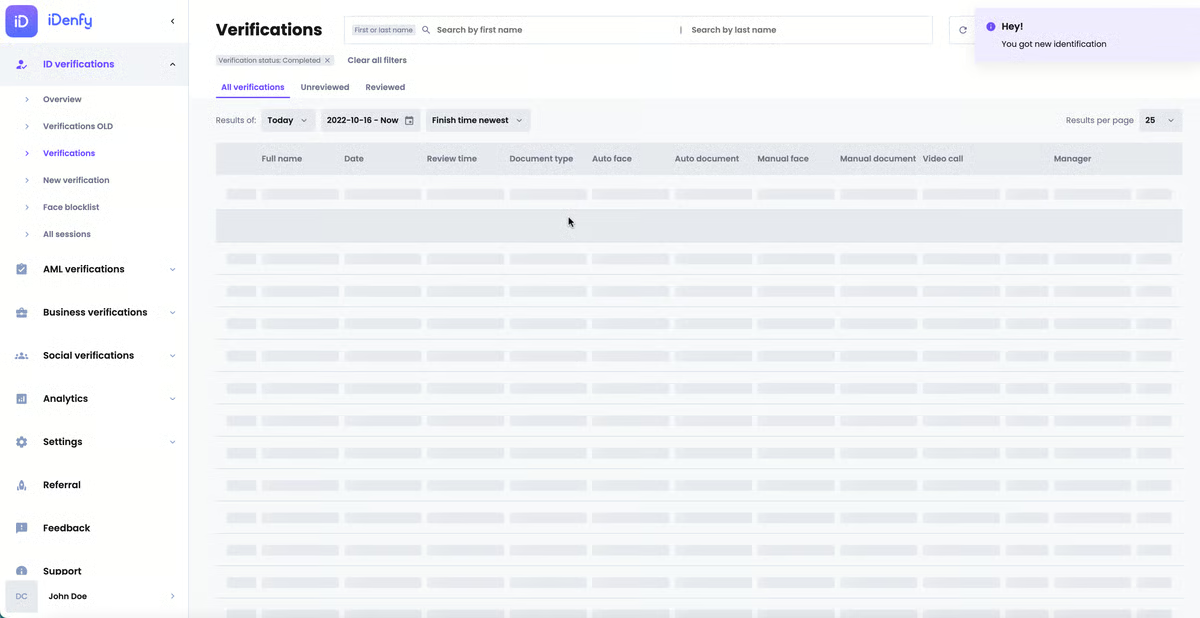
That said, I’ve come across some feedback pointing to areas where proactive notifications about platform updates or maintenance could be improved. While most users agree that iDenfy is generally reliable, there are mentions of occasional surprises regarding service interruptions or feature updates. G2 users suggest that a more advanced notice would help them better prepare and maintain operational continuity, further enhancing the user experience.
Another area where some reviewers note room for improvement is customization of the verification flow. While many find the existing setup works well for standard use cases, some users desire more granular control over the verification journey. This feedback seems to be common among teams needing highly tailored solutions that go beyond the platform’s standard configuration.
What I like about iDenfy:
- I’ve seen G2 users consistently praise iDenfy’s API documentation for being clear and well-structured, which helps development teams integrate the platform efficiently.
- I’ve read multiple reviews highlighting iDenfy’s pricing model, where users appreciate the flexibility of paying only for approved verifications, offering better budget control without sacrificing security.
What G2 users like about iDenfy:
"The sales manager demonstrated exceptional efficiency in responding to inquiries. The platform’s ease of use was impressive, with integration completed in just a few minutes, allowing us to start working seamlessly within 10 minutes. Their customer support team is highly responsive, addressing issues promptly. Moreover, the platform offers many features that align perfectly with our goals of streamlining onboarding and enhancing compliance processes."
- iDenfy Review, Benas L.
What I dislike about iDenfy:
- I’ve noticed some users mention a lack of proactive notifications about platform updates or maintenance, which can lead to unexpected service interruptions.
- I’ve received feedback where users desire more granular control over the verification flow, especially for teams with highly specific requirements.
What G2 users dislike about iDenfy:
"Additional language options for the verification flow interface would be appreciated. As a global company, we aim to serve our users in the languages they are most comfortable using."
- iDenfy Review, Guna K.
4. Mastercard Identity Review 360: Best for secure digital payments
From my review of G2 user feedback, global identity verification stands out as a key strength of Ekata by Mastercard Identity Review 360. Many G2 reviewers highlight how effectively the platform supports verification across various countries, a critical aspect for businesses that must confirm customers' identities in diverse regions.
Many have also mentioned that the system integrates smoothly into their operations, helping them confidently verify new accounts and transactions. Regarding ease of integration, the reviews clearly show that users appreciate how straightforward it is to incorporate Mastercard Identity Review 360 into their existing systems.
Several G2 reviewers mention how little time they needed to spend on setup and adjustments, thanks to the platform’s user-friendly interface. The seamless integration process has earned praise for simplifying the workflow and making the identity verification process more efficient for teams.
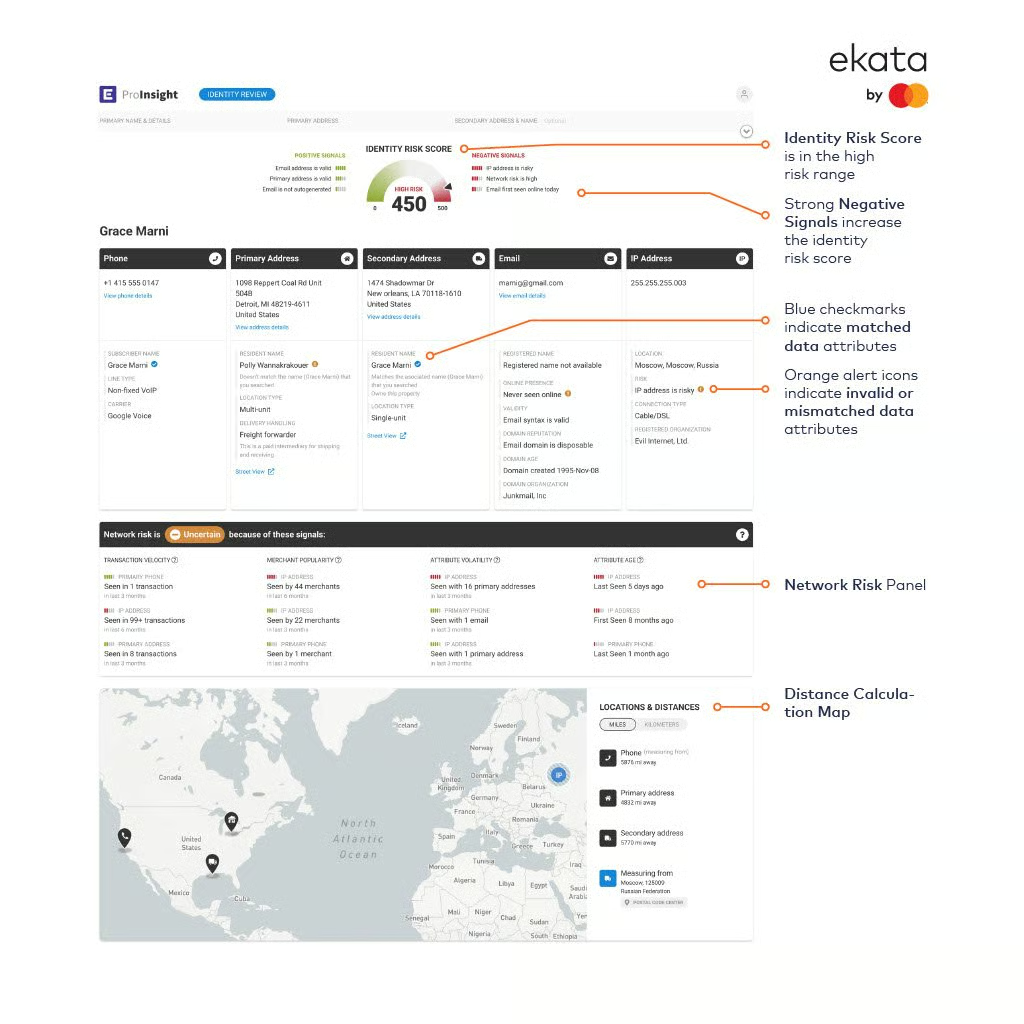
That said, looking at the broader review trends, I’ve come across feedback on some limitations with data accuracy. Some G2 users express frustration with instances where specific phone numbers didn’t return results, creating roadblocks during the verification process.
Additionally, I’ve seen users mention that the platform lacks detailed insights into relationships between individuals sharing an address, which could be helpful when investigating multiple connections at the exact location.
Another point that I’ve seen multiple G2 reviewers bring up is related to the risk score calculation. While many users appreciate the risk assessment feature, there are concerns about the accuracy and consistency of the risk scores. In particular, some characteristics appear to disproportionately impact the final score, leading to concerns that the risk evaluation is not fully representative of a customer’s actual risk.
Users suggest that a more nuanced approach to risk calculation, taking both primary and secondary factors into account, would improve the accuracy of the assessments and better reflect the real risk associated with a customer.
What I like about Mastercard Identity Review 360:
- I’ve seen G2 users consistently highlight Mastercard Identity Review 360’s global identity verification feature, praising its ability to verify identities across multiple countries, which enhances trust and the customer experience.
- I’ve encountered feedback from users who appreciate the seamless integration process. Reviewers mention how quickly they can set up and start using the platform due to its intuitive interface.
What G2 users like about Mastercard Identity Review 360:
"EKATA is a useful tool that provides insights into data that requires mitigation. By using phone numbers, email addresses, and physical addresses, you can determine if the phone, email, and address belong to the same person."
- Mastercard Identity Review 360 Review, Hyan Drix V.
What I dislike about Mastercard Identity Review 360:
- I’ve noticed some users express frustration with data accuracy issues, particularly when specific phone numbers don’t return results, causing delays in verification.
- I’ve read several reviews where users suggest that the risk score calculation could be more accurate, with concerns about some factors disproportionately affecting the final score.
What G2 users dislike about Mastercard Identity Review 360:
"It doesn't indicate how the other occupant at the same address is related to the primary individual. However, the overall experience of using the information available in EKATA is very helpful."
- Mastercard Identity Review 360 Review, Monaliza B.
5. Onfido: Best for remote document and biometric verification
From my review of G2 user feedback, many users consistently praise Onfido’s ease of use. G2 reviewers often highlight how intuitive the platform is, even for teams without extensive technical expertise.
I’ve seen multiple users mention how simple it is to navigate, which seems to significantly smooth the adoption process. For businesses looking for a tool that doesn’t require deep development knowledge, Onfido’s design appears to be a major benefit.
One feature that G2 reviewers seem to really appreciate is seamless integration. I’ve noticed users frequently point out that the platform integrates smoothly into existing systems without major overhauls. This is what makes it a highly rated identity verification app for desktops.
The API documentation is often highlighted as comprehensive and easy to follow, making the setup process straightforward. Many G2 users value the ability to adapt easily to different workflows, which helps them save time and reduce friction during implementation.
However, G2 reviews also highlight areas for improvement. For example, ID type support is a common concern. Many users note that while Onfido covers most common ID types, there are some cases where less typical IDs are not supported.
I’ve seen multiple reviewers mention this limitation, especially those serving diverse, international user bases. Broadening the range of supported IDs would likely enhance the tool’s versatility for these businesses.
Another recurring issue in G2 reviews is false positives. While users generally praise Onfido’s fraud detection capabilities, some have pointed out that legitimate transactions can sometimes be flagged as suspicious. I’ve encountered several reviews where users mentioned that this resulted in extra manual verification. Despite this, the strong fraud protection Onfido provides seems to make this inconvenience a minor issue for most, according to user feedback.
What I like about Onfido:
- I’ve noticed G2 users consistently praise Onfido for its ease of use. Many mention how intuitive the platform is, even for teams without technical expertise.
- I’ve seen frequent mentions of Onfido’s seamless integration, with reviewers highlighting how easily the platform adapts to existing systems and workflows.
What G2 users like about Onfido:
"The integration options provided make it easier for businesses to seamlessly incorporate identity verification into their existing workflows. Onfido is designed to meet regulatory compliance standards, which is essential for businesses in industries with strict identity verification requirements, such as finance and healthcare. It utilizes advanced technologies like facial recognition, document verification, and biometrics to ensure accurate and secure identity verification, helping businesses and organizations establish trust with their users."
- Onfido Review, Verified User in Financial Services
What I dislike about Onfido:
- I’ve encountered feedback in which users express concern about Onfido’s limited ID type support, especially for businesses with diverse, international user bases.
- I’ve read multiple reviews where users mention false positives, noting that legitimate transactions can sometimes be flagged as suspicious, leading to additional manual verification.
What G2 users dislike about Onfido:
"Analytics on the data we process through Onfido could be improved. Additionally, developer transparency regarding upgrades in operating system level dependencies has been unclear."
- Onfido Review, Scott C.
6. SheerID: Best for verifying targeted consumer groups
Based on my review of G2 user feedback, ease of use is one of the most frequently praised aspects of SheerID. Many users comment on the platform's intuitive and straightforward nature, making it easy to set up and manage even for non-technical business users. This simplicity seems to be a key factor that helps teams focus more on their core operations without worrying about the complexities of the verification process.
A consistent theme in G2 reviews is SheerID’s exceptional uptime and reliability. Users frequently highlight how dependable the platform is, especially when delivering gated discounts or other verification services. Many reviewers appreciate that they can rely on SheerID to ensure smooth verification without experiencing technical hitches, which is crucial for maintaining a seamless customer experience.
Another element that I see getting a lot of praise on G2 is customer support. Reviewers often mention how responsive and helpful the SheerID team is when assistance is needed. There’s a lot of love for their willingness to work with customers to address specific needs, and users frequently note how customer satisfaction seems to be a top priority for the company.
From what I’ve seen in G2 reviews, customization options are an area where users express some desire for improvement. While many acknowledge that the standard version works well out of the box, there are multiple mentions of how additional flexibility could enhance the user experience. G2 reviewers often suggest that more customization options would allow them to tailor the platform to their specific requirements.
I’ve also come across noticeable dissatisfaction around the limitation that emails cannot be used for verification. Several reviewers point out how this restriction can complicate the verification process. While users appreciate SheerID’s efforts to work with them and find alternative solutions, the lack of email verification is still a common drawback. Several users, like myself, would prefer this option for a simpler, more streamlined process.
What I like about SheerID:
- I’ve seen G2 reviewers consistently praise SheerID for its ease of use, with many highlighting how intuitive and straightforward the platform is for non-technical users.
- I’ve read frequent mentions of SheerID’s exceptional uptime and reliability. Users appreciate its consistent performance in delivering gated discounts and other verification services.
What G2 users like about SheerID:
"SheerID allows us to automatically verify military and student enrollments using information provided by our guests. This saves a significant amount of staff time and ensures that eligible guests receive the appropriate discounts. We can also add more code as needed and receive a warning when the remaining code bucket is low. Additionally, the support staff have always been very helpful whenever we reach out."
- SheerID Review, Larry E.
What I dislike about SheerID:
- I’ve received feedback where users desire more customization options to better tailor the platform to their specific needs.
- I’ve noticed noticeable dissatisfaction from users regarding the lack of email verification, with many feeling that this limitation complicates the verification process.
What G2 users dislike about SheerID:
"The only real downside for me is that emails can't be used for verification. I understand the reasoning, how easily emails can be manipulated, and I appreciate the role this plays in fraud prevention. That said, the team has worked closely with our organization to identify other acceptable documents for verification, which has been very helpful."
- SheerID Review, Jennifer H.
7. Ondato: Best for customizable, compliance-focused workflows
From my review of G2 user feedback, biometric authentication capabilities are frequently highlighted as a standout feature of Ondato.
Many users appreciate the platform’s facial recognition feature, noting how accurate and user-friendly it is. G2 reviewers emphasize that this functionality has helped them streamline the onboarding process, ensuring a secure, smooth experience for both teams and customers without adding unnecessary complexity.
A recurring positive theme in G2 reviews is Ondato’s speed and responsiveness. Users often comment on how efficient the platform is during operational use, particularly when handling verifications or processing customer data. There’s consistent praise for how the system maintains performance without feeling sluggish, which has been critical for maintaining workflow efficiency.
Additionally, users regularly highlight the platform’s built-in compliance features, which ensure adherence to regulatory standards without additional work and offer peace of mind to businesses concerned about legal complications. Notably, according to G2 Data, 96% of G2 users specifically praise its ability to generate standard compliance reports.
However, from what I’ve gathered in G2 feedback, some users have mentioned challenges with age verification for younger users. In particular, there are occasional reports of difficulty verifying the age of clients who appear younger than they actually are. While this doesn't seem to be a widespread issue, I’ve seen a few G2 reviewers express frustration, especially businesses working with younger demographics who need more accurate age verification.
Another area where I’ve noticed room for improvement is in customization options. While Ondato’s system is effective and fast, several reviewers mention that having more flexibility to tweak the verification flow would improve the platform’s appeal to businesses with unique needs. More customizable features could help businesses tailor the process to their specific requirements, making the tool even more versatile.
What I like about Ondato:
- I’ve noticed G2 users frequently highlight Ondato’s biometric authentication capabilities, particularly the facial recognition feature, for its accuracy and ease of use in streamlining onboarding.
- I’ve seen consistent praise for Ondato’s speed and responsiveness, with users appreciating the platform’s ability to handle verifications efficiently without slowing down operations.
What G2 users like about Ondato:
"Ondato’s transaction monitoring system is ideal for businesses focused on compliance with AML regulations. I find it to be an automated, real-time solution that tracks and analyzes financial behavior to ensure security. What I appreciate most is that every transaction is analyzed instantly, with data cross-checked against PEP profiles, global sanction lists, and more. This helps our system detect irregular patterns and alerts us to potential risks, giving us a clear and accurate view of our transactions."
- Ondato Review, Michael B.
What I dislike about Ondato:
- I’ve encountered feedback in which users mention challenges with age verification for younger clients, particularly when verifying individuals who appear younger than their actual age.
- Some reviews suggest that more customization options for the verification flow would enhance the platform’s flexibility, especially for businesses with unique needs.
What G2 users dislike about Ondato:
"Sometimes we get a few bugs that delay the response time. While this hasn’t significantly affected operations, it’s an area that could use improvement."
- Ondato Review, Michael R.

Identity verification software: Frequently asked questions (FAQs)
1. How accurate is identity verification software?
The accuracy varies depending on the tool and the technology used (e.g., facial recognition, document verification). However, many advanced systems are over 99% accurate. Liveness detection also helps eliminate spoofing attempts.
2. Does identity verification software offer multi-channel verification for mobile and web transactions?
Yes, identity verification software typically supports multi-channel verification, ensuring secure transactions whether customers shop via mobile apps or desktop websites. It provides a seamless experience across devices, offering businesses secure and convenient customer verification methods.
3. What is the best identity verification tool for mid-sized businesses?
Tools that offer scalable solutions at a reasonable cost, like Onfido, offer flexible pricing plans with robust identity verification features that cater to businesses of varying sizes. Many of these tools also provide free trials, so you can test their features before committing to a paid plan.
4. How can I automate my identity verification process for frequent use?
You can use tools that offer API integrations or batch verification options to automate frequent verifications. These allow you to automatically verify large numbers of users, reducing manual effort and ensuring faster processing. Many identity verification tools, such as Onfido, Incode, and iDenfy, support automated workflows and integrations with your existing systems to streamline the process.
5. Which is the most trusted identity verification service for app developers?
Onfido is a trusted pick for app developers thanks to mature iOS/Android/Web SDKs, clear API docs, and fast integration; choose Incode if top-tier biometrics are your priority.
6. Which is the best identity verification software for small businesses?
iDenfy is the best fit for small businesses with pay-per-approved pricing and quick setup, while Onfido is a close alternative with an easy trial and workflows.
7. Which are the top identity check apps for my software startup?
For startups, iDenfy and Onfido stand out. iDenfy offers budget control and speed, while Onfido offers broader ID/document support and scale.
8. Which is the best identity verification tool for online services?
Onfido is the best all-around tool for online services (document + biometric checks, simple APIs), while Sumsub excels when KYC/AML compliance is central.
9. Which is the most efficient ID verification software for e-commerce sites?
Mastercard Identity Review 360 is most efficient for e-commerce checkouts and payment risk, with Onfido pairing well for account creation and document checks.
10. What's the best software to check identities in tech companies?
Onfido is my top pick for tech companies due to flexible APIs, wide ID coverage, and strong developer experience; consider Incode when biometric security is paramount.
Less hassle, more security
After exploring the top identity verification software solutions, I’ve seen firsthand how the right tool can significantly boost security and simplify user authentication.
Whether you're aiming to prevent fraud, streamline user onboarding, or maintain compliance, these tools offer features to address a range of needs.
With so many options to choose from, there's always a solution that can protect your organization’s data while ensuring smooth, frictionless access for users. I hope my insights help you select the perfect identity verification software for your business, because let’s be honest, nobody enjoys dealing with constant security challenges!
Strengthen your security and simplify user access. Find the right identity and access management tool for your needs!
.png?width=400&height=150&name=Untitled%20design%20(56).png)









.png)

.png)


