March 25, 2025
 by Sagar Joshi / March 25, 2025
by Sagar Joshi / March 25, 2025

Your Wi-Fi’s acting up, and suddenly your laptop wants a “network security key.” What even is that and why now?
If your network isn’t locked down, it’s open season for anyone nearby. That’s where a network security key comes in: it’s your Wi-Fi’s line of defense, and it matters way more than most people realize.
A network security key is a password that secures access to a wireless network. It encrypts data between a device and a router to prevent unauthorized use. Most keys contain letters, numbers, and symbols. Users can find the key on a router label or within the device’s Wi-Fi settings.
User provisioning and governance tools are critical in safeguarding IT applications by implementing access controls. Similarly, using a network security key can also prevent unauthorized users from eavesdropping on sensitive information or accessing your devices
You can set a network security key using uppercase, lowercase, and special characters joined by a number. Make sure it doesn’t contain predictable elements like your name or the name of your loved one(s), a number related to your birthdate, or any combination that’s easy to guess.
Some of the common types of network security keys used for authorization in a wireless network are wired equivalent privacy and Wi-Fi protected access. Different types of network security keys have distinct security offerings, yet their primary function remains the same, i.e., network access control.
Wired equivalent privacy (WEP) is a security algorithm intended to provide data confidentiality the same as traditional wired networks. It encrypts data packets using a 40-bit key combined with a 24-bit initialization vector (IV) to make an RC4 key. The 40 bit and 24 bit IV combine to create a 64-bit WEP key.
WEP is a sequence of characters between numbers 0-9 and the letters A-F. So, your WEP key can be 1A648C9FE2.
Due to the U.S. restrictions on the export of several cryptographic technologies, early WEP versions were limited to 64-bit encryption devices. When the regulating body lifted these restrictions, 128-bit and 256-bit encryption also came into the picture. Out of these, 128-bit encryption was seen as the most common implementation in devices.
There are two methods of encryption that you can use with WEP:
The process looked secure, but in reality, anyone could decode the key by cracking the challenge-frames. To protect the network security key from potential exposure, Wi-Fi protected access superseded wired equivalent privacy and evolved as a more secure authentication method in wireless networks.
In the Wi-Fi protected access (WPA) security algorithm, the client requesting to connect to a network needs a security key to initiate communication. After verification of the key, data exchanges are carried out in an encrypted manner.
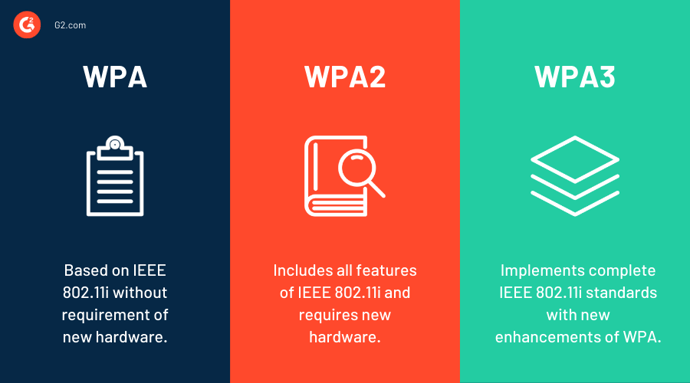
There are three versions of WPA:
Using the message integrity check, the wireless protected access security certification program protects data against modification risks. It supersedes the cyclic redundancy check for error detection and correction, earlier used in WEP.
It does have a message integrity check, which guards the data against viruses that can automatically modify and retransmit the packets. Thus, it replaces the cyclic redundancy check for error detection and the correction used by the WEP.
| Type | Encryption strength | Common use case | Still secure? |
| WEP | 64- or 128-bit RC4 | Legacy networks only | No |
| WPA | 128-bit TKIP | Older hardware | Limited |
| WPA2 | 128-bit AES (CCMP) | Home and enterprise Wi-Fi | Yes |
| WPA3 | 192-bit or AES-128 (CCM) | Public networks, modern Wi-Fi | Strongest |
You can find a network security key in different ways, depending on the type of device where you’re searching for.
A network security key is often labeled on the exterior of a router. You should look for a small sticker at the back or the bottom of the device. If it’s not available there, check its packaging box or the manual that came with it from the manufacturer.
You will usually have your key set printed on the bottom of the router your ISP provides when you take a broadband deal from them. The key can be changed, but make sure you don't lose it.
The network security key would be labeled as a security key, WPA key, or passphrase on a router. A default one would come with the new device, but you need to change it to avoid unauthorized access.
Nine steps to change your network security key (network password):
While easily accessible, it's crucial to remember that network security keys require proper management. Network security policy management software helps create strong passwords, enforce security protocols, and automate key rotation to minimize security risks.
When your Windows device is connected to the wireless network, you can access the saved login data to get the network security key.
For Windows 10 users, you can use the following steps to find the passphrase of your network:
If you’re using a Windows 7 operating system, you can access the network security key through the following path:
It’ll display the network security key you’re searching for. You can also use the same key to connect other devices to the network.
When it comes to Mac, the process of finding your network’s password is somewhat similar to Windows. You should know the Wi-Fi network's name, and you can instantly get the security key.
Follow these six steps to find your network security key:
Whether you have an Android or an iOS device, you can find the network security key stored on your phone in a few simple steps.
Android users with root access can use ES file explorer or Android terminal emulator, whereas users without root access can utilize Minimal ABD and Fastboot to get network security key.
Finding a network security key on your iPhone or iPad is much easier than on Android, as it doesn’t require root access. You can follow the steps mentioned below to access the network security key.
When you get a network security key mismatch error while trying to log into your wireless network, there is a high possibility that you're entering an incorrect password. But it's not the sole reason. There can be various other causes, like wrong security mode, antivirus software, or defective wireless drivers.
To fix the error, you can use some common methods mentioned below.
Yes. Your network security key is simply your Wi-Fi password. It’s the string of characters that allows your device to connect to a wireless network securely. Most routers use WPA2 or WPA3 security protocols that require this key to authenticate access.
You’ll usually find the default network security key on a sticker on the back or bottom of your router, labeled as “WPA Key,” “Wireless Password,” or “Security Key.” You can also access it by logging into your router’s admin page using the device’s IP address.
A mismatch error means the password entered doesn’t match what the router is expecting. First, double-check for typos or Caps Lock. If it persists, restart your device, update network drivers, or verify you’re using a compatible Wi-Fi protocol (WPA2 or WPA3). You can also reset the password from your router settings.
Yes. You can log into your router’s admin dashboard using the device’s IP address, navigate to wireless or security settings, and enter a new password. Be sure to reconnect all devices using the updated key.
WEP is outdated and insecure. WPA introduced stronger encryption, but WPA2 became the standard with AES-based encryption. WPA3 is the most secure and includes 192-bit encryption in enterprise settings and improved protection on public networks.
On Windows, you can find your saved Wi-Fi key through the Network and Sharing Center by checking the wireless network properties. On Mac, open Keychain Access, search for your network, and check “Show Password” (admin password required).
Although the WPA2 security algorithm offers advanced security, you must keep the network security key safe from malicious hackers. Make sure you manage passwords effectively and protect your devices from cyber attacks.
Learn more about how you can safeguard your cybersecurity and provide seamless access to digital assets with network monitoring software.
This article was originally published in 2021. It has been updated with new information.
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.
No matter how many times we type it in, sometimes we forget our password.
 by Mara Calvello
by Mara Calvello
Fast identity online (FIDO) standards are authentication protocols where security and user...
 by Sagar Joshi
by Sagar Joshi
When I was a kid, passwords were a fun little game. I’d come up with something silly, like my...
.png) by Devyani Mehta
by Devyani Mehta
No matter how many times we type it in, sometimes we forget our password.
 by Mara Calvello
by Mara Calvello
Fast identity online (FIDO) standards are authentication protocols where security and user...
 by Sagar Joshi
by Sagar Joshi


