October 16, 2025
 by Samudyata Bhat / October 16, 2025
by Samudyata Bhat / October 16, 2025

With rapidly advancing technology and increasingly high user expectations, companies must regularly upgrade outdated systems.
Companies understandably want to maintain a vital operational system for as long as possible. However, clinging to outdated technology can quickly transform what was once an asset into a liability. Old systems can soon become dangerous, costly, and time-consuming.
Companies often use archive storage solutions to store data after sunsetting legacy apps.
Technology has also revolutionized cloud environments and architectures over the past several years, allowing business processes to build, upgrade, update, and manage applications faster through cloud migration software.
A legacy application is outdated software that is still in use. These applications may lack modern security, compatibility, and integration features, but remain critical to business operations, making them difficult to replace or upgrade.
Companies continue to utilize legacy programs for a variety of reasons. The expense of updating a legacy application may be prohibitive in some instances.
In other circumstances, the legacy program may be so tightly connected with other systems that replacing it would be difficult or impossible. Finally, some businesses may be unwilling to adapt, even if there are compelling reasons to do so.
Not all legacy systems are ancient; some date back only five or ten years. What makes them "legacy" isn’t just age, but whether they’ve become an operational liability rather than an asset.
Here are the most common reasons applications, systems, or technologies end up labeled as legacy:
A legacy program is typically associated with a specific operating system (OS) or coding language. The problem is usually running the legacy application while converting it to newer, more efficient code that uses current technologies and programming languages.
Example: An application created to run on Windows 7 may be unable to operate on Windows 10. This is despite adding middleware or glue code or the OS being generally backward compatible.
The typical forms of legacy systems are as follows:
Legacy apps are designed with traditional development approaches based on monolithic architectural models. This indicates that the application's code, services, and other components are deeply interwoven, making scaling and adapting to changing contexts more difficult.
Businesses often continue to rely on legacy applications to meet crucial business demands. However, legacy applications are frequently inefficient, unreliable, and unsuited for achieving digital transformation objectives due to their interconnected designs.
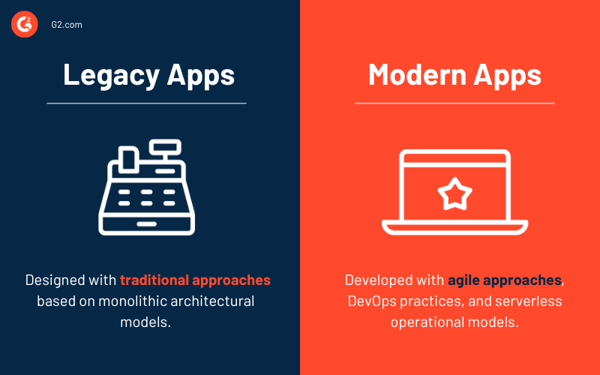
Modern apps are developed with agile approaches, DevOps practices, modular design, and serverless operational models. These are more flexible, scalable, portable, and resilient than older applications. They enable enterprises to develop custom application development solutions quickly while decreasing time to market and total cost of ownership.
Modern applications can handle millions of users on demand and run on multiple platforms, including on-premises and cloud-based environments. The contemporary application development approach eliminates much of the operational overhead associated with historical application development. Consequently, teams may concentrate on business logic while delivering higher-quality solutions.
Businesses stick with legacy applications for various reasons. Some of them are discussed below.
Many companies, such as banks and government agencies, rely on legacy systems. These companies depend on established, consistent, and reusable technologies that are typically complex to develop and expensive to replace. The following are some examples:
Legacy applications might seem “good enough,” but beneath the surface, they can quietly drain resources, introduce vulnerabilities, and hinder innovation. Here’s a breakdown of the most pressing risks companies face when sticking with legacy tech:
Legacy application modernization is the process of transforming programs developed with outdated software into new apps using cutting-edge technology. Legacy application modernization approaches like application programming interface (API) generation bridge the gap between legacy and modern systems and enhance the value of existing systems.
Other approaches, like cloud migration, enable apps to be modified or rebuilt to operate in current runtime environments.
Businesses strive to modernize legacy programs because they rely on obsolete technology, making it difficult to protect, enhance, and transmit critical application components. Replacing or updating old systems is necessary to manage critical business functions effectively.
Below are some strategies used in legacy application modernization.
| Strategy | What it does | Best for |
| Rehost | Moves app to new infrastructure without changing code | Fast migration to the cloud |
| Replatform | Makes small adjustments to suit new environments (e.g., containers) | Performance improvements without a full rewrite |
| Refactor | Updates code for better structure, integration, or scalability | Making apps cloud-ready and more maintainable |
| Rebuild | Redesigns and rebuilds the app from scratch | Future-proofing high-value legacy systems |
| Replace | Retires legacy app and adopts a new solution | Outdated tools with modern alternatives available |
Digital adoption, automation, and migrating old apps to the cloud aid in the monitoring and accounting of corporate operations and procedures. Legacy application data migration boosts performance and organizational competitiveness while assuring improved job execution. This is where cloud migration software comes into play.
G2 helps businesses find the best cloud migration tools for accelerating digital transformation, reducing infrastructure costs, and scaling applications securely in the cloud.
*Above are the five leading cloud migration software solutions from G2’s Fall 2025 Grid® Report.
Often, enterprises must preserve their legacy data to maintain compliance with internal corporate laws and policies and applicable legal regulations and policies. They will undoubtedly need to archive both new and old data, but it must be simple to access, manage, and control. This is where archive storage solutions come into play.
Data frequently preserved in archive storage systems aren't immediately relevant but still have value.
G2 helps businesses find the best archive storage software for preserving critical data, meeting compliance requirements, and optimizing long-term storage efficiency.
*Above are the five leading archive storage software solutions from G2’s Fall 2025 Grid® Report.

Got more questions? We have the answers.
Absolutely. Strategies like rehosting, replatforming, or refactoring allow businesses to modernize gradually, without rewriting the entire application from scratch.
The most cost-effective path depends on the app’s complexity and business role. Rehosting or replatforming are generally less expensive than rebuilding or replacing.
Industries like banking, healthcare, government, and manufacturing often depend on legacy systems due to complex regulations, high reliability needs, or long-standing custom software.
Key signs include a lack of vendor support, performance issues, rising maintenance costs, integration roadblocks, and an inability to meet security or compliance standards.
Legacy modernization focuses specifically on updating outdated systems, while digital transformation is a broader initiative that includes rethinking processes, tools, and culture to fully leverage modern technology across the organization.
In some cases, yes, through middleware, APIs, or integration platforms. However, integration is often limited, brittle, or costly, which is why many businesses opt for modernization to enable seamless, scalable connectivity.
Several obstacles must be overcome while working with legacy programs in today's ever-changing technological environment. An organization's capacity to innovate and respond to shifting market needs is often hampered by its aged systems' inflexibility, scalability, and inefficiency.
But since firms are often comfortable with their legacy system, is it time to upgrade, or should you stick with what has served you well for years?
Ready to modernize smarter? Discover how AI is transforming legacy system modernization from faster code refactoring to intelligent migration planning.
This article was originally published in 2023. It has been updated with new information.
Samudyata Bhat is a former Content Marketing Specialist at G2. With a Master's degree in digital marketing, she specializes her content around SaaS, hybrid cloud, network management, and IT infrastructure. She aspires to connect with present-day trends through data-driven analysis and experimentation and create effective and meaningful content. In her spare time, she can be found exploring unique cafes and trying different types of coffee.
Every click, swipe, or tap continues a data trail that adds to the vast mosaic of our online...
 by Samudyata Bhat
by Samudyata Bhat
Filing cabinets are obsolete. So are storage silos and reactive backup plans.
 by Samudyata Bhat
by Samudyata Bhat
Cloud storage has made it easier for us to store our data. Previously, you might have used...
 by Sagar Joshi
by Sagar Joshi
Every click, swipe, or tap continues a data trail that adds to the vast mosaic of our online...
 by Samudyata Bhat
by Samudyata Bhat
Filing cabinets are obsolete. So are storage silos and reactive backup plans.
 by Samudyata Bhat
by Samudyata Bhat