September 4, 2025
 by Soundarya Jayaraman / September 4, 2025
by Soundarya Jayaraman / September 4, 2025

In my years writing about cybersecurity, I’ve learned one universal truth: no one wakes up excited about identity and access management (IAM), but everyone regrets ignoring it.
Between employees reusing weak passwords, phishing attempts targeting credentials, and the growing web of SaaS applications, keeping accounts secure without frustrating users is easier said than done.
Throw in remote work, third-party integrations, and compliance audits into the mix, and it’s no surprise that IAM feels like an endless game of catch-up. The challenge isn’t just about security — it’s about finding the right IAM tool that actually works without adding complexity to daily operations.
If you’re a security leader, IT manager, or business decision-maker, finding the best identity and access management software for your organization can feel overwhelming. With so many options promising airtight security and seamless integration, how do you know which one truly delivers?
I’ve done all this research, so you don’t have to. I spoke with IAM experts, reviewed G2 reports, and gathered insights from my own IT and security team (who have seen enough bad IAM setups to last a lifetime). After comparing 15 leading IAM solutions, I’ve narrowed it down to the top five that actually stand out for security, scalability, and usability.
*These are the top-rated products in the IAM software category, according to G2's Winter 2025 Grid® Report. I have mentioned the starting price of their paid plans for easy comparison.
Whether you’re upgrading your IAM strategy or looking to choose the leading identity and access management platform for the first time, this guide will help you find the best fit for your organization.
Without IAM, managing user access is like handing out keys to an office and losing track of who has them or where they’re being used. It is what keeps that chaos in check.
IAM protects access, while operational risk management software helps address the risks tied to those identities across the business. It controls who gets access to what, when, and how securely, so IT teams can enforce security policies, prevent unauthorized access, and reduce risk without turning every login attempt into a support ticket.
I've researched my fair share of IAM software in all shapes and sizes, from cloud-focused ones to on-premises solutions and from highly customizable systems for large enterprises to simple options for growing teams.
From my research and conversations with IAM experts, I’ve realized that the best IAM software isn’t just about security. It's about the balance between secure user authentication, granular access controls for enforcing the least privilege, and smooth integration with existing systems.
And the stakes are only getting higher. The global IAM market is projected to reach $41.52 billion by 2030 from $15.93 billion in 2022.
Finding the best IAM software isn’t just about comparing feature lists or vendor promises — security leaders need solutions that actually work in the real world. I started by analyzing G2 Grid reports, which rank IAM tools based on real-world adoption, user satisfaction, and enterprise fit. This gave me a clear view of which platforms dominate the space and how they perform in areas like authentication, access control, and compliance.
To go beyond rankings, I used AI to analyze hundreds of user reviews of these products. This helped me identify recurring themes — whether it was frustration over clunky authentication flows, praise for adaptive access policies, or concerns about integration with existing security stacks.
Given I couldn’t sign up and access the tool myself, I also spoke with IAM experts, my own IT and security team members, and professionals who deal with identity security daily and use these tools and validated their comments with verified G2 reviews. Their feedback helped me cut through the noise and focus on solutions that deliver strong security without becoming a bottleneck for IT operations.
The screenshots featured in this article may be a mix of those captured during testing and ones obtained from the vendor’s G2 page.
Did you know? On average, businesses report ROI on IAM investments in 14 months, according to G2 Data.
Based on everything I’ve learned, here’s the checklist I used to evaluate the top IAM solution:
After checking each tool against this checklist and cross-referencing it with expert insights, real-world feedback, and AI-driven review analysis, I identified the top five IAM solutions.
Whether you're looking for the best identity management tool with multi-factor authentication, or the best IAM software for securing remote workforces, there's a tool below.
The list below contains genuine user reviews from the IAM software category. To be included in this category, a solution must:
*This data was pulled from G2 in 2025. Some reviews may have been edited for clarity.
From what I’ve seen in G2 reviews, Microsoft Entra ID (formerly Azure Active Directory) is often highlighted as one of the leading identity and access management platforms, largely due to its deep integration into the Microsoft ecosystem. Many users appreciate how seamlessly it works with other Microsoft services like Azure, Dynamics 365, Intune, and Power Platform.
I’ve noticed that G2 users frequently mention how Entra ID comes included at no additional cost if your company is already using Microsoft services. This built-in support for MFA, unlimited SSO across SaaS apps, basic reporting, and self-service password changes is a major advantage, particularly for businesses that are already integrated into the Microsoft environment.
From my research, I’ve found that Entra ID’s strong authentication and security controls stand out to many IT professionals. The ability to enforce flexible conditional access policies, especially when paired with Intune for endpoint management, is often praised as a comprehensive solution for unified access control.
I’ve seen multiple G2 users express their appreciation for conditional access, which allows IT teams to tailor security policies based on user behavior, location, and risk levels. This functionality is especially valued because it helps balance security with usability, prompting MFA for unrecognized devices while allowing trusted devices to access resources with minimal friction.
One feature that users frequently call out is Entra Connect, which allows seamless integration of on-premises Active Directory with Entra ID. I’ve read several reviews from organizations transitioning to the cloud who find this particularly beneficial for simplifying access management across both cloud and on-premises infrastructures.

That being said, setup and configuration are common pain points I noted among G2 reviewers, especially for businesses with mixed IT environments. Several reviewers note the time and complexity required to get everything running smoothly, particularly when migrating from non-Microsoft setups.
Licensing costs was another recurring theme in G2 feedback I saw. While Entra ID offers a free tier, users often mention that the more advanced security features, such as those under identity protection, governance, and privileged access management, are only available in higher-tier licenses like Entra ID P2.
From my analysis, small businesses often struggle with the cost of premium licensing despite needing advanced features. Many G2 users have shared that figuring out which Entra ID tier best fits their needs can be tricky when balancing security and compliance requirements.
Overall, despite the challenges, I’ve seen a general consensus that Microsoft Entra ID is a solid IAM solution. For large organizations deep in Microsoft, it’s often the answer to "which identity access app is best for enterprises?"
"Microsoft Entra is one of the best solutions Microsoft offers for verifying and identifying enterprise technology assets such as laptops and mobile phones. It ensures that only the right people have access to specific resources.
What I like the most are these three features: multi-factor authentication with the Microsoft Authenticator app, identity management for each device, and its integration with BitLocker, which provides full disk encryption for the asset. This way, data is securely stored and can be recovered with a BitLocker recovery key."
- Microsoft Entra ID Review, Erick Vincent Steve G.
"Users unfamiliar with Microsoft products will face difficulties in understanding the integration of this product, and the same goes for companies using non-Microsoft platforms. The cost of implementing Microsoft Entra ID could be a concern for low-budget companies along with this, the companies that pose challenges in environments with unstable internet access can face problems because Entra ID is cloud-based."
- Microsoft Entra ID Review, Sahil C.
On a budget? Explore the top free IAM software options.
From what I’ve seen in G2 reviews, JumpCloud is often praised for being a flexible, cloud-first IAM solution designed for organizations moving away from traditional on-prem identity management.
Many users appreciate its ability to manage identities across multiple platforms, including Windows, Android, iOS, macOS, and Linux, all from a single platform. This open directory approach allows it to integrate seamlessly not only with Azure or Active Directory but also with Google Workspace, AWS, and other third-party SaaS apps, making it an appealing choice for multi-cloud and hybrid setups.
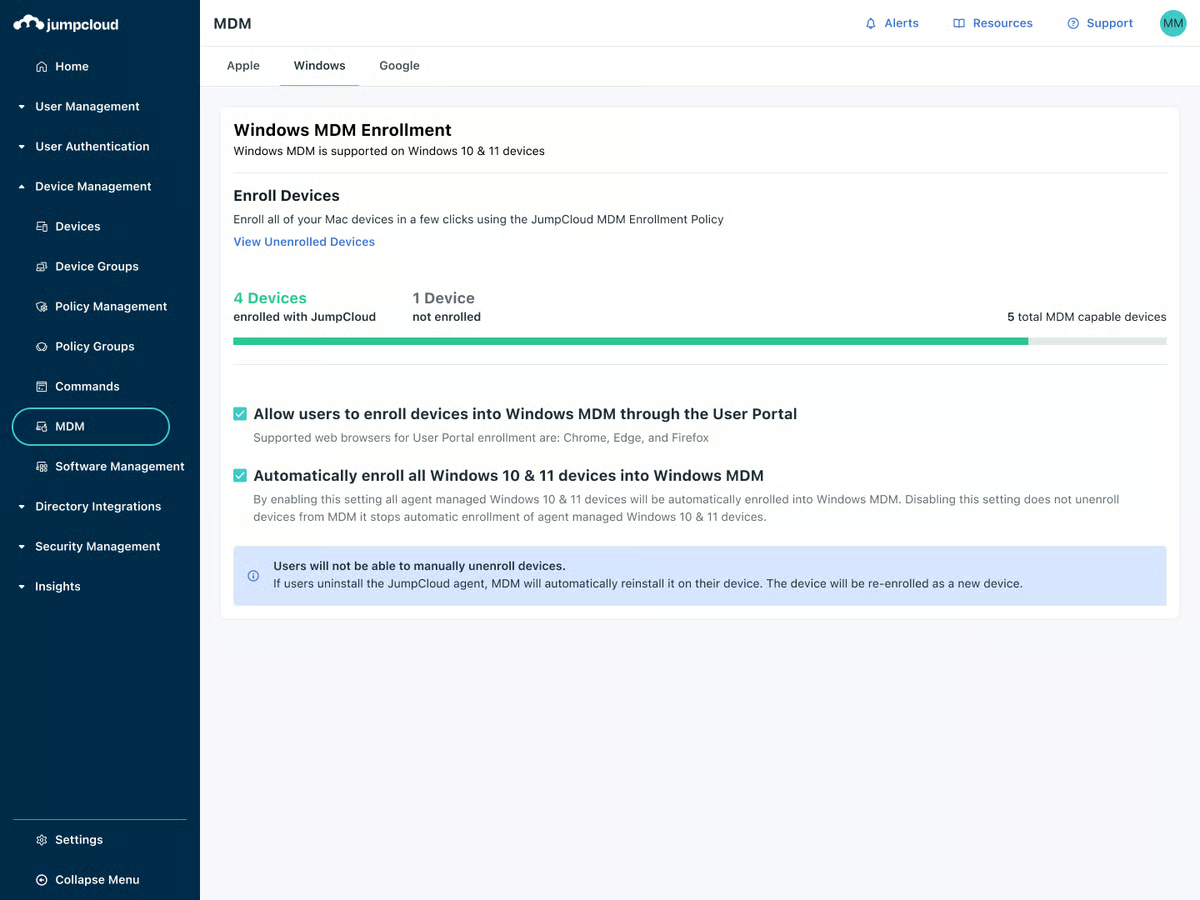
I’ve noticed that G2 users highlight JumpCloud’s all-in-one platform, which combines IAM, mobile device management (MDM), directory services, and endpoint security. This integration makes managing users, devices, and security policies from a single platform particularly attractive to IT teams juggling multiple operating systems. Many users report significant time savings and streamlined operations because of this unified approach.
From a usability standpoint, I’ve seen several reviews commending JumpCloud for its clean and user-friendly interface. Users find the onboarding process simple, and the ability to easily deploy SSO and MFA across the organization is highly valued.
One feature that’s frequently mentioned in G2 feedback is JumpCloud’s extensive knowledge base, which includes step-by-step tutorials and videos. Many users appreciate this resource for making setup and implementation easier. Additionally, JumpCloud’s customer support receives positive reviews for being reliable and responsive when issues arise.
However, some G2 users do point out certain missing features. For instance, the lack of self-service for account unlocks means that IT teams must manually assist users who are locked out, which can become cumbersome. Remote assist is another area where some users note issues, as it’s seen as somewhat clunky and in need of improvement.
I’ve also seen several G2 reviews mention that JumpCloud’s MDM capabilities, while useful, may not provide the same level of granular control and automation found in other MDM solutions, especially in Apple-heavy environments. Users managing large fleets of devices, particularly Apple devices, often feel that JumpCloud doesn’t quite match up to specialized MDM solutions like Jamf.
Despite these drawbacks, I believe JumpCloud’s main strength is its unified approach to IAM, directory services, and MDM.
It offers an all-in-one solution that works well for small and medium businesses, even though it might come at a higher price point than standalone enterprise-grade IAM or MDM solutions. That’s why I consider JumpCloud one of the best IAM solutions for mid-sized tech companies juggling multiple platforms. For organizations looking for an integrated platform, JumpCloud remains a solid option.
"JumpCloud is very easy to use and user-friendly. It helped us manage our employees' systems. We can now manage software application installations on these systems via a feature in JumpCloud, Software Management, which is quite helpful.
Also, it is very easy to apply any policies via JumpCloud to end-user systems, such as password policy, MFA for logging into the system, etc. Also, directory integration is very easy to set up, such as AD, Cloud, or HR directories. With this, we can also run commands on remote systems and take remote assistance/control of the system, which is very useful. And the customer support is always there for you, and they are quite fast in responding."
- Jumpcloud Review, Saurabh R.
"Jumpcloud has yet to develop advanced features like self-service for Account unlocks, User orchestration, and governance capabilities, which are necessary in this era of enterprise security management."
- Jumpcloud Review, Gangadhara S.
Controlling who accesses your systems is one part of the puzzle. Managing the devices they use is the next. Explore the best Mobile Device Management (MDM) solutions I trust to keep every endpoint secure, updated, and compliant.
Okta is one of the most flexible and scalable IAM solutions, especially for organizations requiring strong security and advanced authentication. Like JumpCloud, it’s vendor-neutral and works well in multi-cloud environments and with complex SaaS integrations.
I’ve noticed that Okta integrates seamlessly with tools like Microsoft, Google Workspace, and AWS, making SSO, adaptive authentication, and automated user provisioning effortless across a wide range of applications.
From a user experience standpoint, I’ve found Okta’s interface intuitive for both IT teams and end users. It’s frequently praised for offering one of the smoothest SSO experiences.
I also value that Okta supports third-party MFA and token providers and its own built-in MFA, giving companies the flexibility to integrate whatever works best for them. The customizable SSO portal is another feature that stands out for simplifying app management.
When it comes to handling scale, Okta is often seen as the top identity management service for startups aiming to grow fast without security bottlenecks.

However, from what I’ve read on G2, pricing can be a barrier for smaller businesses and startups, as Okta offers a la carte pricing, which can add up quickly when multiple services are needed.
I’ve come across reviews where users mentioned that setting up Okta can be challenging. Configuring policies, settings, and integrations takes time and effort, which was overwhelming for some G2 reviewers. While Okta provides good documentation and support, fine-tuning everything for optimal security and automation still requires a considerable investment of time.
"Over the years, I have worked with Okta across various companies, and I must say that it is honestly one of the best SSO solutions on the market. Not only is it user-friendly with a modern interface, but it also boasts high-security standards and supports working with thousands of users simultaneously."
- Okta Review, Paloma G.
"Okta is expensive and unsuitable for smaller businesses. Pricing plans are a la carte and confusing. Configuring directories and user synchronization will take a lot of effort and time."
- Okta Review, Qual A.
Related: Learn about how identity-as-a-service (IDaaS) is different from IAM.
Among CRM-heavy teams, Salesforce is a leading identity and access management platform with built-in SSO and MFA. G2 users often highlight as a strong IAM solution, especially for businesses already running on the Salesforce Platform. Single Sign-On (SSO) and Multi-Factor Authentication (MFA) are two key features frequently mentioned, with reviewers noting that these are essential components of the solution.
I’ve noticed that many G2 users appreciate Salesforce’s App Launcher. This enables users to access a range of business applications — Salesforce apps as well as third-party apps — without needing to log in separately. Even when using Active Directory for user management, users can rely on Identity Connect to manage Salesforce accounts, which is seen as a significant benefit for usability and security.
I’ve encountered noticeable satisfaction regarding Salesforce's level of control over data access. Multiple reviewers mention how connected apps and OAuth enable fine-grained access controls, allowing companies to restrict access to sensitive information. This is particularly beneficial for teams managing customer accounts and sensitive data.
From what I’ve read, many G2 users find the Customer Identity feature to be a strong addition, especially for large businesses that need to track customer activity across multiple channels. Reviewers note that the ability for customers to self-register, securely log in, and access apps with a single identity is a standout feature. The fact that it is fully customizable to fit company branding and workflows also helps businesses streamline their processes.

However, I’ve seen some users note the complexity of the setup process. G2 reviewers frequently mention that configuring Salesforce Identity can be time-consuming due to the large number of configurations, permissions, and integrations that need to be adjusted. This makes onboarding more complicated compared to dedicated IAM solutions like Okta or JumpCloud.
I’ve noticed that some G2 users report the platform can be slightly sluggish at times, especially when dealing with large datasets or complex workflows. While this isn’t seen as a dealbreaker, some reviewers have raised it, particularly regarding response times.
Finally, I’ve read multiple reviewers mention pricing as a consideration. While Salesforce Identity is often viewed as a good fit for larger enterprises already within the Salesforce ecosystem, G2 users point out that it may not be as budget-friendly for small to mid-sized companies.
Based on my analysis of G2 reviews, Salesforce Identity seems like a solid option for businesses already heavily invested in Salesforce, particularly those using its CRM software in Professional, Enterprise, Unlimited, or Performance Editions.
"Salesforce is cloud-based and offers enterprise-grade scalability. Whether you're connecting to external systems via APIs, using Salesforce Connect for external data sources, or leveraging pre-built connectors for popular tools.
What I like best about Salesforce is its flexibility and power in enabling businesses to build custom applications without requiring a lot of complex coding. Also, customer support is great and very helpful. I use Salesforce daily in my work. It is easy to use, integrate, and implement."
- Salesforce Platform Review, Rushabh U.
"As a user, what I don't like about Salesforce is that it is very expensive, especially for small businesses and startups. As a developer, when you are dealing with large amounts of data, the reports and dashboard can run slowly, and sometimes, the governor limit can restrict the complex operation."
- Salesforce Platform Review, Dhruv G.
IAM controls who gets access, while network monitoring tools help track what happens inside your systems. Here’s my evaluation of the best options.
I've noticed that G2 users often praise Cisco Duo for its straightforward approach to security. Many reviewers highlight its simplicity and effectiveness, especially regarding MFA, SSO, and adaptive authentication.
Unlike some IAM tools that feel overloaded with unnecessary features, Duo stands out for keeping things focused and easy to manage, which is a consistent theme in user feedback.
From what I’ve seen, negative feedback tends to focus on the learning curve of other IAM platforms. Several users have expressed that Duo is much easier to use than other IAM tools, which often have steep learning curves. Duo’s ease of use is frequently mentioned, with users appreciating its simple interface and its flexibility in terms of integration with various applications and platforms.
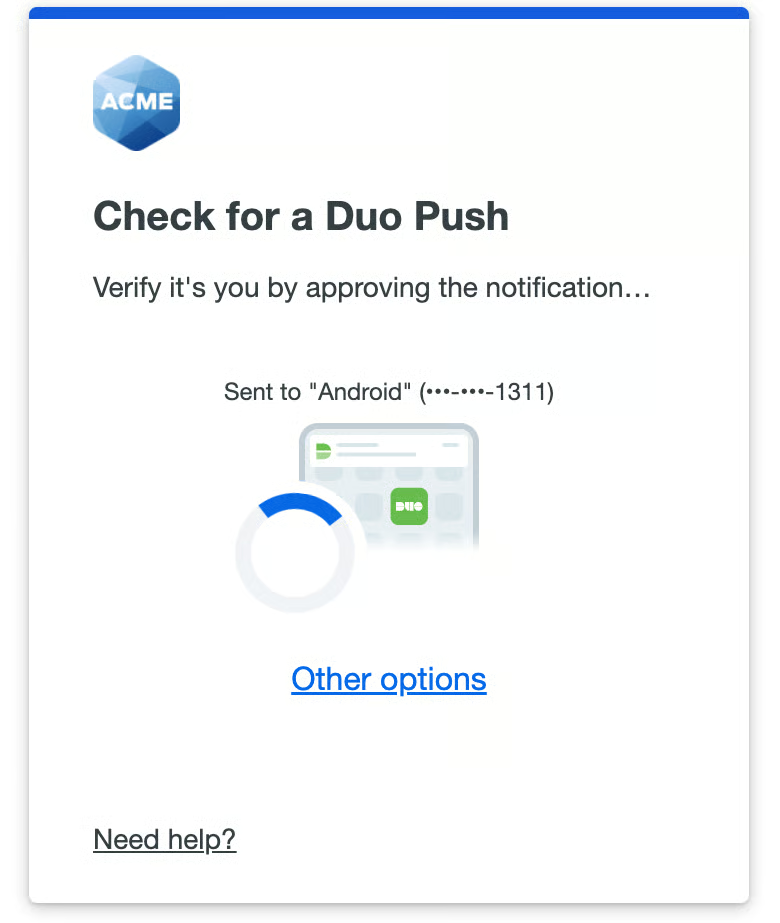
I’ve come across feedback on G2 around Duo's offline access. Many users have pointed out that its offline functionality is limited, which can be an inconvenience in certain scenarios. While Duo offers strong core features, some users feel this aspect could be improved for better flexibility in offline environments.
I’ve read multiple reviewers mention struggles with the user interface and design. While the system is functional, many G2 users believe the UI could be more intuitive and modern. This feedback suggests that while Duo is effective, its design could be a barrier for users who value a more streamlined, user-friendly experience.
Despite these challenges, many G2 users find Duo to be a solid choice for organizations seeking reliable MFA and SSO solutions.
For small IT teams, Duo often emerges as the best IAM software for small businesses thanks to its free tier and easy deployment. Users appreciate the opportunity to test Duo's features with up to 10 users at no cost, giving smaller teams or startups an affordable option to implement secure access controls.
"It was simple to set up, and authentication is virtually immediate when connecting to my company's VPN. I prefer the push notification approval approach, as it only requires me to tap a button on my phone. It combines with many other out-of-the-box solutions, and it offers cloud-based, AD-integrated SAML SSO and virtual appliance alternatives to protect even bespoke interfaces.
We utilized Duo to protect our VMware Horizon desktop environment; setup and deployment were simple, and I like how simple it is to connect with Active Directory. Even better, end user onboarding was simple, and end users found the system simple to use, which is the most important benefit."
- Cisco Duo Review, Connie B.
"The setup of online and offline can be confusing for end users. Also, if time desyncs, it becomes a huge problem."
- Cisco Duo Review, Jonathan M.
Explore the best password managers that are designed to securely store, generate, and autofill passwords while protecting user accounts.
Now, there are a few more options, as mentioned below, that didn't make it to this list but are still worth considering, in my opinion:
IAM enhances security, reduces the risk of data breaches, streamlines user access, and ensures compliance with industry regulations (e.g., GDPR, HIPAA, SOC 2). It also improves productivity by automating user provisioning and access management.
Key IAM features include:
IAM focuses on managing access for all users in an organization. PAM is specifically designed to secure access for privileged accounts with elevated permissions, such as system administrators.
IAM solutions can be:
Yes, IAM is a critical component of Zero Trust by enforcing identity verification, least privilege access, and continuous monitoring to prevent unauthorized access.
IAM pricing varies based on features, deployment type, and the number of users. Some vendors offer subscription-based models, while others provide enterprise licensing. Additional costs may include implementation, support, and compliance features.
Consider: Your organization's size and security need Integration capabilities with your existing tools, Compliance requirements, Scalability, ease of use, and Support for modern security practices (e.g., Zero Trust, MFA, adaptive authentication).
The best IAM tool depends on your organization's needs, budget, and existing infrastructure. Popular IAM solutions include Okta, Microsoft Entra ID (formerly Azure AD), JumpCloud, Cicso Duo, Ping Identity, IBM Security Verify, and ForgeRock. It's best to compare features, integrations, and security capabilities before choosing.
JumpCloud and Okta often stand out, offering flexibility across operating systems, SaaS integrations, and cloud environments without overwhelming IT teams.
Cisco Duo is one of the most reliable identity access apps for startups thanks to its ease of use and free plan. JumpCloud also works well for small businesses that need device management alongside IAM.
According to G2 reviews, Microsoft Entra ID and Okta consistently rank as the best-reviewed IAM platforms for corporate environments, balancing enterprise-grade security with scalability.
Cisco Duo often ranks as the most reliable identity access app for startups, thanks to its intuitive setup, strong MFA and SSO support, and a generous free tier for small teams.
Okta and Microsoft Entra ID both excel at role-based access control (RBAC), offering granular permission management, attribute-based rules, and just-in-time provisioning to help organizations enforce least-privilege access efficiently.
After digging into the best IAM software solutions, I’ve come to one conclusion: security should work with people, not against them. Even when organizations invest in IAM, adoption isn’t guaranteed. G2 data shows the average user adoption rate is just 71% — meaning nearly one in three employees still don’t fully use their IAM tools. That gap creates not only security risks but also productivity bottlenecks.
So the real challenge isn’t just buying IAM software — it’s finding a solution that actually works in practice for you, without adding complexity to daily operations.
The strongest authentication policies in the world won’t help if employees find ways around them out of frustration. At the same time, an easy login experience means nothing if the wrong person gains access. That’s the balancing act every IT and security team faces, and the right IAM tool makes all the difference.
If your company is deep in Microsoft’s ecosystem, Entra ID is a strong choice. JumpCloud and Okta give you flexibility across different platforms. Salesforce Identity makes sense if Salesforce runs your business, and Cisco Duo keeps things simple with strong MFA and integrations. Each tool has its place, but the best IAM solution is the one that fits how your organization actually operates.
At the end of the day, IAM isn’t just about securing logins — it’s about protecting your business from real threats while keeping access smooth for the right people. So, pick the right IAM, and you’re not just enforcing policies — you’re building a security culture that actually works.
Still on the hunt? Explore our categories of identity management systems to find the best fit for your security needs.
Soundarya Jayaraman is a Senior SEO Content Specialist at G2, bringing 4 years of B2B SaaS expertise to help buyers make informed software decisions. Specializing in AI technologies and enterprise software solutions, her work includes comprehensive product reviews, competitive analyses, and industry trends. Outside of work, you'll find her painting or reading.
Managing access across different apps can get complicated fast. Strong passwords help, but...
 by Washija Kazim
by Washija Kazim
In the pre-single sign-on (SSO) era, I never conveniently browsed an application as I got...
.png) by Shreya Mattoo
by Shreya Mattoo
My phone and I are inseparable.
 by Washija Kazim
by Washija Kazim
Managing access across different apps can get complicated fast. Strong passwords help, but...
 by Washija Kazim
by Washija Kazim
In the pre-single sign-on (SSO) era, I never conveniently browsed an application as I got...
.png) by Shreya Mattoo
by Shreya Mattoo


