June 11, 2024
 by Mara Calvello / June 11, 2024
by Mara Calvello / June 11, 2024

When you connect to your home wi-fi, you know that your identity and data will be protected from the outside world. How?
Because it has been assigned a secure IP address.
An IP address is a unique address given to your devices so that a web server recognizes them and builds a secure connection with them. Devices like laptops, mobile devices, tablets, smartwatches, and other internet devices all have a unique IP address assigned by a router to share information within the same network. IP address intelligence tools also enable you to browse resources online without registering on a particular domain.
Having a protected and approved IP address can protect your devices, reduce the scope of distributed denial of services (DDOS) attacks, and make it difficult for unethical hackers to trace your information via random websites and networks that you access.
An IP address is a unique identifier assigned to each device on a network. It acts like a digital mailing address, allowing devices to find and communicate with each other on the internet.
An Internet Protocol (IP) address is a technical address assigned to each device on a network. It acts like a digital mailing address, allowing devices to find and communicate with each other on the Internet. Different devices have different IP addresses that mask the user's identity and register their private or public devices on the network server for a smooth transition of data.
The actual IP address may look something like this: 192.168.0.1. It is a unique string of 0 to 255 characters assigned by your local internet service provider so that your devices can interact with each other or other network servers to access, retrieve, share, or manage data. You need to be wary of your network protection, keep your IP addresses protected from malicious use, and manage vulnerabilities with ease.
IP addresses can be fixed or dynamic. Your router can assign you different IP addresses and reassign your old IP address to other internet users. This is done to safeguard user privacy and follow the guidelines of internet service providers so that the scope of any IP address getting hacked or replicated is minimal.
IP addresses are critical for identifying devices and routing appropriate website traffic that won't hinder the security of a particular network infrastructure. With new web hosting tools and IP hosting tools, the internet can now accommodate a huge number of IP addresses.
Here are the different ways in which IP addresses work:
Each device on the server has a unique address that distinguishes it from other devices. That address allows devices to sync with a public or private network, access the web, or communicate with other devices across different network servers.
When data is sent to a network, it goes through your home or public router and some encryption and cryptography protocols are added to the data your device is trying to send. This is known as data packets. Each packet contains.
These packets are reassembled into the original data at the destination.
Registering on an IP admin allows your router to route specific traffic and data among different networks. For this, they use their own individual IP address granted by the Internet-assigned number authority (IANA) and multiple device IP addresses to connect with server systems. This process includes several steps.
Step-by-Step Routing Process:
Subnetting is a process of dividing the capacity of mainframe servers, WiFi servers, and company servers into smaller chunks that can register the IP address and allow smooth data transmission. Each subnet has its address range.
Tip: A subnet mask accompanies an IP address as a measure of security. This mask is used to define network and hosting providers and allow access to browsing data.
For example, in the IP address 192.168.1.10 with a subnet mask of 255.255.255.0:
NAT allows multiple devices on a private network to share a single public IP address. The devices also have individual private IP addresses and share the router's common public IP address. It is used for the following reasons.
DNS translates human-readable domain names (e.g., www.example.com) into IP addresses (e.g., 93.184.216.34). This allows users to connect to websites using easy-to-remember names instead of numerical IP addresses.
DNS Resolution Process:
Here is an example of IP address working methodology while sending an email from your private internet connection to the main email server.
To illustrate these concepts, consider sending an email from one user to another:
This detailed workflow explains how the network traffic flows smoothly from source to destination within a singular network or across multiple networks.
There are various versions of IP addresses that you would be granted based on your network provider. The functions of IP addresses differ based on home streaming networks and office networks. Here are a couple of IP addresses that your local ISPs can grant access to:
Think of your IP address as your home address. In the same way that your street address allows the mail carrier to find your home and deliver your mail, your IP address is how your server is able to find your device among the billions of others that are connected to it.
There are four easy methods of finding what your IP address is, so let’s get started with the first one.
Probably the easiest and simplest way to find your IP address is to Google it.
I know, you’re probably thinking how does Google know my IP address? Well, it’s as easy as searching “What is my IP address” in the Google search bar.
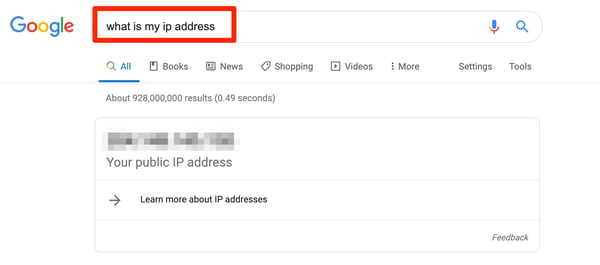 |
Voila! Whatever number pops up here is your IP address.
Not everyone is interested in the easiest way to do something, and that’s totally fine! Let’s explore how to find your IP address on your Mac.
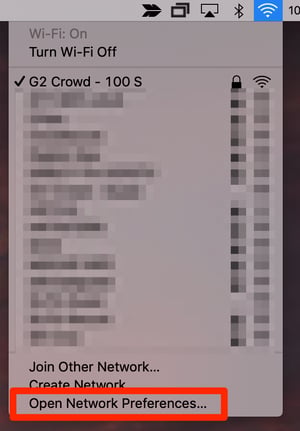
First, click at the top of your screen where your Wi-Fi bars are and click Open Network Preferences.

The next screen will show you which Wi-Fi network you’re connected to. Directly under Status will be your IP address.
On your iPhone and in need of your IP address? From Settings, select the Wi-Fi network you’re connected to.
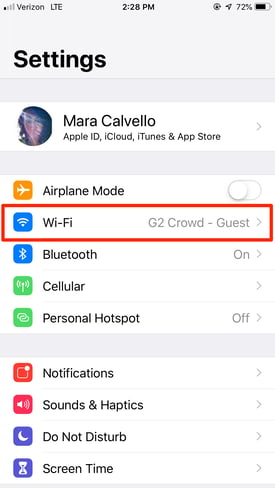
Next, tap the Wi-Fi network again to see more information.
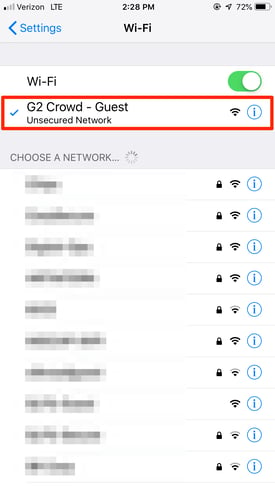
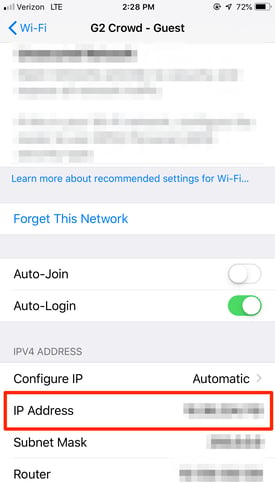
At the bottom of this next screen, you’ll find your IP address.
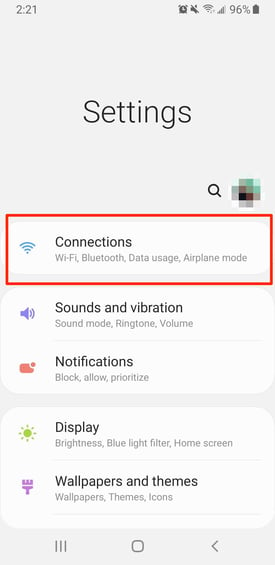
I know, I know… not everyone has an iPhone, which is why I have Samsung Galaxy users covered, too.
From the Setting screen, tap Connections.
Then, tap where your Wi-Fi network is listed.
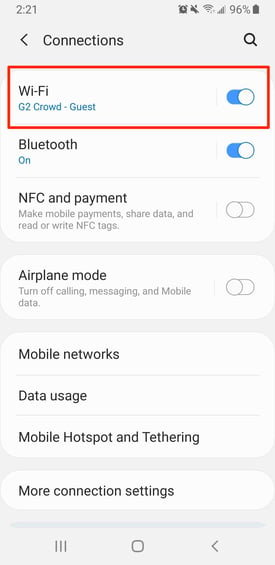
From the next screen, select your Current Network.
This next screen will show you more information about your Wi-Fi network, including your IP address.
Now that you know your IP address, have you ever thought why you should know what your IP address is? And why it’s important from a cyber security standpoint that you should keep it a secret (hence these blurred out screenshots)? Well, that’s simple, too.
If a hacker has access to your personal or company IP address, they can potentially damage the network.
For instance, once someone knows your IP address, they can replicate it and download illegal content that can cause issues with your internet provider or even something much larger, like instigating a DDoS attack to flood your server with fake traffic.
It’s also important to consider that if your IP address falls into the hands of a hacker who knows the inner workings of geolocation technology, they can track down the physical location of your company’s office, your home, and all of the connected devices.
Keeping your IP address secure is just one reason to invest in top-notch cyber security providers. If you’re unsure which one would be best for your company, check out our comprehensive list and everything you need to know about your options.
As much as IP addresses secure your internet connections, they pose a serious threat of unwanted attacks. Hackers can easily get your addresses from websites you visit. Websites store user data and browsing behavior in the form of cookies, making your IP address vulnerable to viruses.
With this information, hackers can know your location, cross-verify it with "IP location," and keep an eye on your activities. Although this might not be your fault, but it can bring you to the attention of law enforcement. Here are different ways in which an unprotected IP address can harm you:
Ensuring you follow the correct data security and data piracy practices with your IP hosting provider can keep these unwarranted attackers at bay. Always use a good firewall protection, antivirus system, or cybersecurity software to ensure safe browsing and a seamless data exchange experience.
Now that you know everything about an IP address, learn to double-pack your cybersecurity with the best-managed DNS provider software in 2024
Mara Calvello is a Content and Communications Manager at G2. She received her Bachelor of Arts degree from Elmhurst College (now Elmhurst University). Mara writes content highlighting G2 newsroom events and customer marketing case studies, while also focusing on social media and communications for G2. She previously wrote content to support our G2 Tea newsletter, as well as categories on artificial intelligence, natural language understanding (NLU), AI code generation, synthetic data, and more. In her spare time, she's out exploring with her rescue dog Zeke or enjoying a good book.
Internet of Things (IoT) solves pressing business problems but often poses concerning...
 by Sagar Joshi
by Sagar Joshi
Cybercriminals have a wide variety of tools available to them today. One of the most...
 by Yaniv Yagolnitzer
by Yaniv Yagolnitzer
IoT devices allow us to take internet connectivity wherever we go. There are thousands of...
 by Nahla Davies
by Nahla Davies
Internet of Things (IoT) solves pressing business problems but often poses concerning...
 by Sagar Joshi
by Sagar Joshi
Cybercriminals have a wide variety of tools available to them today. One of the most...
 by Yaniv Yagolnitzer
by Yaniv Yagolnitzer