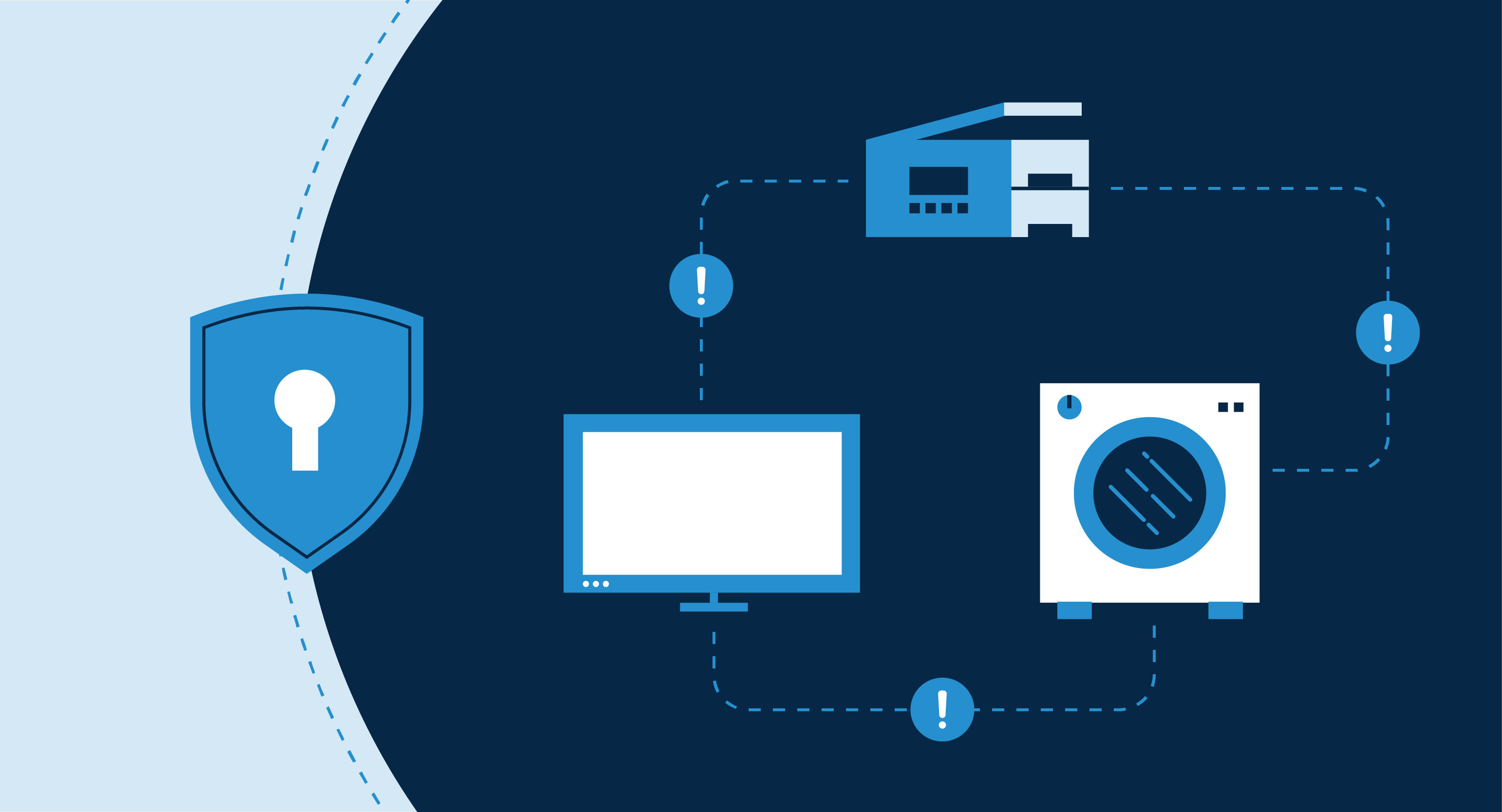
Internet of Things (IoT) solves pressing business problems but often poses concerning challenges.
IoT technology has offered several benefits to various businesses (healthcare, transportation, etc.), and at the same time, it has rolled out security concerns with its rising interconnectedness.
Entities in IoT aren’t necessarily the same type of devices, objects, or services. Every entity has a different purpose, interface, operating mechanism, and technology. Considering the diversity, applying security constructs that are the same as the constructs of other assets won’t yield expected outcomes while ensuring cybersecurity.
It makes IoT security one of the top priorities for organizations intending to safeguard their assets from malicious attacks.
Internet of Things (IoT) security is an approach to safeguard IoT devices connected across a network with protective measures while also preventing cyber attacks.
IoT devices serve as possible entry points for attackers to breach a company’s network, which is why robust security measures are needed to protect them.
Today, IoT’s scope has expanded to include traditional industrial machines and has equipped them with the ability to connect and communicate with a network. You can find IoT technologies being used for various purposes like medical devices, education, business development, communications, and so on.
Before we dive deeper into understanding IoT security, let’s shine some light on IoT devices.
What are IoT devices?
IoT devices are machines that are connected across a network or the Internet. These devices aren’t limited to a smart TV or a smartwatch but include a range of machines like printers, washing machines, air conditioners, and other industrial machines.
An IoT ecosystem is spread across organizations and enterprises, covering a wide range of devices. You can ensure IoT security by leveraging a combination of IoT security solutions, strategies, and techniques.
Identifying IoT security issues and threats is the first step toward addressing them. Your protective measures will be effective only when you identify these issues and structure your preventive strategies accordingly.
One can categorize IoT security issues into technological challenges and security challenges. IoT devices’ heterogeneous and ubiquitous nature contributes to technical challenges primarily related to scalability, wireless technology, distributed nature, and energy. On the contrary, security challenges include authentication, confidentiality, integrity, and end-to-end security.
Security goals of confidentiality, integrity, and availability (CIA) apply to IoT devices, and achieving these goals poses a challenge, considering restrictions and limitations in terms of computational and power resources.
IoT devices or objects should identify and authenticate one another. However, when so many entities (devices, people, services, processing units, etc.) are involved, authentication becomes challenging.
Moreover, authentication gets tricky when objects in IoT interact with each other for the first time. You’ll need a proper mechanism that authenticates entities in every interaction to address this IoT security challenge.
Designing and implementing protocols either for encryption or authentication poses a challenge considering IoT devices’ limited computational and power capabilities.
98%
of all IoT traffic is unencrypted, exposing personal and confidential information.
Source: IoT Business News
These algorithms need to be compatible with the device’s capability, and lightweight solutions should be introduced and implemented to ensure IoT security.
IoT devices have different capabilities, complexities, and vendors. There’s a high possibility that the release dates, technical interfaces, bitrates, and functionalities of IoT devices differ from one another.
Designing and implementing security protocols to encompass such diversity in IoT stages is a challenge for organizations. Moreover, IoT operates in a dynamic environment where the connectivity between devices can change. You need to consider these parameters while designing protective measures to ensure IoT security.
IoT needs policies and standards to ensure that data is stored, transmitted, and processed securely. Enforcing such policies and standards across all devices becomes tricky as you deal with diverse entities in the Internet of Things and their dynamic environment.
You need to have clear standards, and your security mechanism should enforce them across all IoT devices to achieve predefined service level agreements (SLAs).
IoT devices encounter several security challenges that pose a risk for organizations and enterprises using them.
Here are a few notable IoT security challenges:
IoT security challenges are spread across different layers of IoT architecture - perception layer, network layer, and application layer.
The purpose of the perception (or sensors) layer is to collect data from the environment with the help of actuators and sensors.
Here are a few security challenges in the perception layer:
These IoT security challenges can be addressed by adopting encryption, authentication, and access controls.
The network layer of IoT infrastructure enables data routing and transmission to various IoT hubs and devices connected to the Internet.
The security challenges associated with the network layers are as follows:
These security challenges in the network layer can be addressed by adopting protocols and IoT security software to enable an object in IoT to respond to abnormal behaviors and situations.
The application layer achieves the purpose of IoT by creating a smart environment. This layer guarantees the authenticity, integrity, and confidentiality of the data.
The IoT security challenges in the application layer are as follows:
You need proper tools to address security challenges in the application layer and control the amount of data safe to disclose, and how and when it’s being used, and by whom.
There are a few general protective measures that you can set to ensure IoT security. These include using authorized software in IoT devices. Also, when an IoT device is switched on, it should authenticate itself into the network before it collects or sends data.
It’s necessary to set up firewalls to filter packets sent to IoT endpoints, as they have limited computation capability and memory. You should also ensure that updates and patches are installed without consuming the additional bandwidth.
Apart from general security measures, you need to consider some unique security practices while planning the security of IoT devices. You need to ensure device security, network security, and make sure that the overall IoT infrastructure and system are secure from IoT vulnerabilities.
You can adopt the following security practices to secure IoT devices:
Internet of things software solutions protect intelligent devices and IoT hubs from unwanted or unauthorized access. These software solutions minimize risks associated with connecting, managing, and drawing data from IoT devices by providing a secured data pipeline and constantly updated threat awareness and protection.
To qualify for inclusion in the IoT security software solutions list, a product must:
*This list is based on G2 data collected on April 28, 2021. Some reviews may have been edited for clarity.
Google Cloud IoT Core is a fully managed service that enables users to securely connect, manage, and ingest data from millions of globally dispersed devices. It analyzes data both at the edge and in the cloud and is a complete set of tools that helps connect and store information.
“Google IoT Core provides the ease of registering devices and making IoT deployment faster. The option to have multiple data streams helps in data management. All payloads have the necessary information to identify and segregate the devices. Extending from Google PubSub to IoT Core was easy since Pubsub is used under the hood of IoT core for data streaming.”
- Google Cloud IoT Core Review, Arsh P.
“Google Cloud IoT is not that easy to use or understand, especially for non-IT staff. Some training is required prior to proper usage.”
- Google Cloud IoT Core Review, Isabella F.
Azure IoT Hub is a managed service that acts as a central message hub for bi-directional communication between IoT applications and the devices. Users can use Azure IoT Hub to build IoT solutions with reliable and secure communications between several IoT devices and a cloud-hosted solution backend.
“Azure IoT Hub gives our development teams power, flexibility, and versatility for our industrial remote monitoring of web applications. This particular cloud resource in the Azure family of services is a central piece of the foundation of our application architecture. IoT Hub gives us abilities that our team had dreamed about for many years before Microsoft released this particular cloud resource.
"Data harmonization is key to the success of any data-intensive web application. The needs become even more pronounced when consuming huge volumes of time-series sensor data values from hundreds of industrial assets. IoT Hub allows us to handle this type of data from diverse sources, machines, edge devices, and customers.”
- Azure IoT Hub Review, Jon F.
“We ran into some issues with the uploading and downloading of PDF files and their resulting resolution, but it has since been worked out.”
- Azure IoT Hub Review, Joy C.
Azure Sphere is a secured, high-level application platform with built-in communication and security features for internet-connected devices. It comprises a secured, connected, crossover microcontroller unit (MCU), a custom high-level Linux-based operating system (OS), and a cloud-based security service that provides continuous, renewable security.
“One of the things that stands out the most about this package that Microsoft offers is that it’s made up of three items (which cannot be obtained separately) that together make up a reliable solution to increase security in the management of companies' IoT. It also highlights that the OS was based on Linux Kernel while making it easily adaptable to devices and having extra layers of protection.
In general lines, the conjunction of both the Sphere operating system, the microprocessor, and the Sphere security system is outlined as a complete triangulation to provide a solid system that is secure and includes threats to devices in the IoT framework of companies.”
- Azure Sphere Review, Jonathan S.
“I find that the software interface is clustered and quite congested because of different features that are sometimes overwhelming. The security updates come quite frequently, and it’s hard to keep up with them. I’d appreciate it if the connection over the cellular network could be a part of the software and supports the Mac platform.”
- Azure Sphere Review, Jazlyn S.
AWS IoT Device Defender is a managed service that helps users secure IoT devices while continuously auditing IoT configurations to ensure proper alignment with the security best practices.
“AWS IoT Device Defender is a part of AWS IoT Service. Device defenders check the security policies associated with our IoT devices to confirm that the devices are not attacked or manipulated by hackers. If there is a security flaw, then the device defender will send an alert such that we can revoke or modify the security policy. It also becomes easy to authorize and authenticate the devices that are connected through AWS IoT.”
- AWS IoT Device Defender Review, Anu H.
“Its pricing is a little higher comparatively, and sometimes it takes time to detect a security attack.”
- AWS IoT Device Defender Review, Manish S.
Expanse brings a unique level of visibility to security through the continuous scanning of exposed assets. It provides an updated view of all internet-connected assets that belong to an organization.
“A very agile company with amazing customer service. They are very attentive to their customers’ needs and have turned around a feature request very quickly to meet the needs of our business.”
- Expanse Review, User in Information Technology and Services
“Some features in the portal such as reporting are still basic and need a few upgrades to be more useful.”
- Expanse Review, User in Hospitality
As new devices add up to your organization’s IoT, you need to ensure that proper IoT security measures are enforced and prove functional in safeguarding your distributed assets against cyber attacks.
Adopt the above-mentioned security practices equipped with IoT security software solutions to keep your globally dispersed internet-connected devices safe and secure.
Learn more about information security in detail to strengthen your security practices with the fundamentals of safeguarding information.
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.
Like many other high tech advancements, IoT is at the forefront of innovation.
 by Rebecca Reynoso
by Rebecca Reynoso
IoT devices allow us to take internet connectivity wherever we go. There are thousands of...
 by Nahla Davies
by Nahla Davies
Security is a significant cornerstone of any business.
 by Sagar Joshi
by Sagar Joshi
Like many other high tech advancements, IoT is at the forefront of innovation.
 by Rebecca Reynoso
by Rebecca Reynoso
IoT devices allow us to take internet connectivity wherever we go. There are thousands of...
 by Nahla Davies
by Nahla Davies