September 2, 2022
 by Elena Georgescu / September 2, 2022
by Elena Georgescu / September 2, 2022

After the year 2000, when technology use and development skyrocketed, the progression of cyber risk has been cumulative.
The cybersecurity sector concentrated on new security standards and compliance during this time, and then went beyond compliance to look at the core business risks posed by cyber threats.
In 2022 and beyond, the industry and society have matured, and we're now focusing on security suites and infrastructure unification, as well as managing cyber risks. The opportunities and driving factors of one decade do not take the place of those in the one before it.
Instead, they broaden the perspective and emphasize well-known ideas in new ways. One such example is DNS – although its roots can be traced back to 1966, DNS security must be a part of every robust cybersecurity strategy today.
Wondering what exactly DNS security is and why it matters for your business? Let us first have a look at DNS and how it all started.
The Domain Name System (DNS) is an internet protocol that provides human-readable names for a variety of web-based services, including e-mail. Acting as the phonebook of the internet, DNS converts human-readable names to IP addresses, then changes IP addresses back to names.
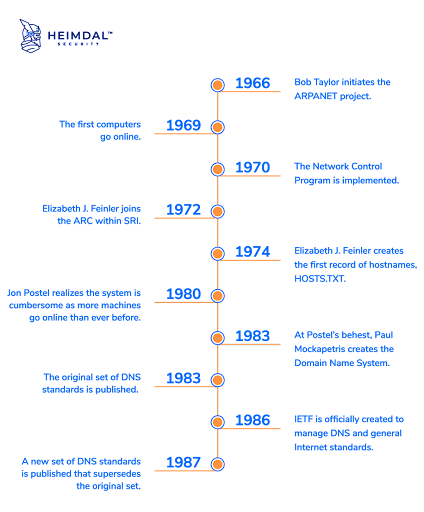
The project started by American Internet pioneer Bob Taylor in 1966 and known as Advanced Research Projects Agency Network (ARPANET) represents the beginning of DNS history. Names to address translations were formerly kept on the ARPANET in a single table contained within a file called HOSTS.TXT. This document was used to manually assign addresses.
However, maintaining the addresses manually had grown extensive and challenging. As a result, American computer scientist Paul Mockapetris proposed a new framework in 1983 that provided a dynamic and distributed system known as the Domain Name System.
With the help of Mockapetris, the DNS became able to look up IP address names rather than just hostnames, making it easier for regular users to access the web. Simply put, without it, there would be no internet as we know it today.
 Source: Heimdal Security
Source: Heimdal Security
Additionally, the Domain Name System Security Extensions (DNSSEC) protects DNS from threats like cache poisoning and guarantees the security and confidentiality of data. All server responses are digitally signed by DNSSEC servers. DNSSEC resolvers check a server's signature to see if the information it received matches the information on the authoritative DNS server. The request will not be granted if this is not the case.
DNS security refers to all the procedures created to keep the DNS infrastructure safe from cyber threats in order to maintain speed and dependability, and prevent the (sometimes) disastrous effects of cyberattacks.
DNS provided us with the internet as we know it today. How much do you think it would have developed if people had to remember long strings of numbers instead of domain names?
It's obvious that the majority of internet users use domain names to describe the websites they wish to access. However, computers employ IP addresses to distinguish between various internet-connected systems and to route traffic over the internet. By enabling the use of domain names, the Domain Name System serves as the internet's backbone and makes it functional.
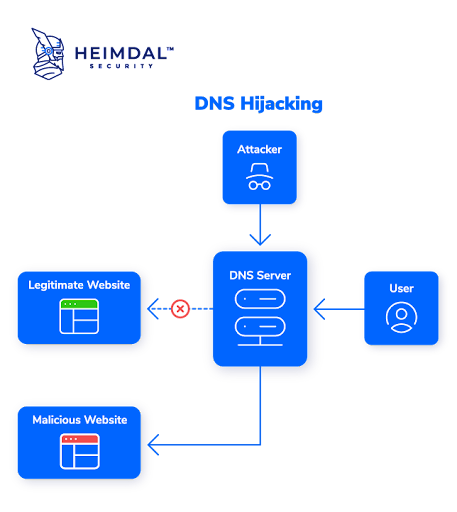
Although its importance is unquestionable, DNS was not necessarily designed with security in mind. Therefore, there are many cyberattacks that can affect it. The most common DNS risks include denial-of-service (DoS), distributed denial-of-service (DDoS), DNS hijacking, DNS spoofing, DNS tunneling, DNS amplification, and DNS typosquating.
And the impact of DNS-based attacks is real—cloud service downtime, a compromised website, damaged brand reputation, lost business opportunities, and the theft of intellectual property.
DNS attacks are among the most prevalent and effective web security threats. Let's discuss more about them.
Below are common DNS attack types.
 Source: Heimdal Security
Source: Heimdal Security
These are the most common DNS attack methods.
As can be seen in the IDC 2022 Global DNS Threat Report, although the DNS attack impact on in-house application downtime and cloud service downtime slightly decreased in 2022 compared to 2021, the percentage of loss of business and brand damage increased.
Users need DNS in order to access their apps and services, whether they are hosted locally or in the cloud. If DNS services are compromised, users cannot access their applications.
No DNS simply equals no business, so regardless of the size of the organization, DNS security is mandatory.
A cybersecurity strategy that uses a multi-faceted approach to safeguard an information technology (IT) infrastructure is known as a defense-in-depth strategy – and DNS security is and must be regarded as one of its key components.
A defense-in-depth strategy incorporates redundancy in case one system fails or becomes susceptible to attacks in order to protect against a variety of threats.
When it comes to DNS security, you must take into account both the endpoints and the network.
Learn more about endpoint DNS security, specifically DNS content filtering and threat hunting, below.
Look for a security solution that includes a threat-hunting component.
You can search for a security solution or suite with a threat-hunting component. In order to help you block malicious domains, communications to and from command-and-control (C&C), and malicious servers, it should proactively evaluate traffic and filter all network packages.
In terms of network DNS security, you must take into account the rise of BYOD and IoT and clearly establish how you determine who and what connects to your online network perimeter – especially in light of the shift toward remote or hybrid work that we've witnessed in the last couple of years.
Bring your own device (BYOD) policy refers to the practice whereby employees connect their personal devices to the networks of their employers and perform everyday tasks.
Some of the benefits of BYOD include reduced costs, increased employee productivity, and higher staff satisfaction, but the disadvantages are equally worth mentioning: high (or even higher) security risks, potential loss of privacy, a lack of devices, and the need for a more complex IT support system.
The most significant threats that a BYOD policy implies are cross-contamination of data, a lack of management and outsourced security, unsecured use and device infection, security breaches and GDPR concerns, obscure applications, hacking and targeted attacks, phishing, adware, spyware, activity recording software, inadequate policies, and last but not least, human error and mixing business with pleasure.
The physical items that are embedded with software, sensors, and other technologies that enable them to connect and exchange data with other devices and systems over the internet are referred to as internet of things (IoT) objects.
An impressive number of factors, such as simple connectivity and data transfer, access to inexpensive and low-power sensor technology, increased cloud platform availability, advancements in machine learning and analytics combined with the enormous amounts of data stored in the cloud, and the rise of conversational AI, have all contributed to the emergence of IoT.
The risks to IoT security systems are substantial. Threats to identity and access management, potential data breaches, the growing number of devices and the substantial attack surface, insecure user interfaces or the convenience of devices, poor software updates, and the ease with which someone with physical access to a product can extract the owner's password from the plaintext, private keys, and root passwords are just a few examples.
Look for a solution that can protect your company at the perimeter/network level.
By utilizing network prevention, detection, and response technology, strong network security solutions effectively eliminate threats. They can work in conjunction with firewalls to prevent malicious requests from reaching perimeter servers in the first place.
Although a high percentage of businesses acknowledge the importance of DNS security, the average time to mitigate attacks increased by 29 minutes, now taking 6 hours and 7 minutes, with 24% taking longer than 7 hours, according to the 2022 Global DNS Threat Report.
The amount of lost time translates into lost revenue, so it's important to be aware of alternative techniques for enhancing DNS security to ensure you don't end up being the next victim of malicious players. Here are some examples:
You might consider hosting your own specialized backup DNS server to improve DNS security. Although managed DNS service providers and Internet service providers can both be attacked, having a backup is crucial not just in the event of a planned attack on your vendor. Hardware or network failures are more frequently to blame for DNS performance problems or outages.
The use of response policy zones (RPZ) is an additional method for enhancing DNS security. A nameserver administrator can use RPZ to provide alternative responses to queries by superimposing custom data on top of the global DNS.
How can a response policy zone help? Well, with an RPZ, you can:
Internet protocol address management (IPAM) is a system that enables IP address management in a corporate setting. It does this by facilitating the organization, tracking, and modification of data pertaining to the IP addressing space.
The network services that assign IP addresses to machines in a TCP/IP model and resolve them are DNS and Dynamic Host Configuration Protocol (DHCP). These services will be connected by IPAM, enabling each to be informed of modifications in the other. For example, DNS will update itself in accordance with the IP address selected by a client via DHCP.
Automation is one of the key strategies for increasing DNS security and should be used whenever and wherever possible.
Automated solutions can help you respond to potential security threats with advanced threat intelligence, deal with security-related issues automatically in real time, and gather crucial security metrics, as well as streamline breach incident response. Moreover, it can minimize human input in time-consuming remediation tasks and increase employee productivity, but also speed up breach incident response and aid in making well-informed decisions.
Despite being the foundation of the internet as we know it, cybercriminals have often chosen DNS as a target in order to take advantage of vulnerabilities, access networks, and steal data.
What does this mean for businesses? Loss of money, time, brand damage, as well as potential fines and legal repercussions.
Every business must therefore be aware of the most significant security risks that DNS implies, including DoS, DDoS, DNS hijacking, DNS spoofing, DNS tunneling, DNS amplification, DNS typosquating.
Equally crucial is knowing what you can do to guarantee DNS security. Businesses can choose to use response policy zones, onsite DNS backups, IPAM, DNS content filtering, and IPAM. Most importantly, they should try to automate security tasks and find security solutions that rely on advanced threat hunting components.
When it comes to staying ahead of cyberthreats, prevention will always be the best course of action.
Ready to bump up your security? Find the best DNS security software to secure DNS servers and the websites they support.
Elena Georgescu is a cybersecurity specialist within Heimdal. Her main interests are mobile security, social engineering, and artificial intelligence. In her free time, she studies Psychology, Neuroscience, and Marketing.
When you connect to your home wi-fi, you know that your identity and data will be protected...
 by Mara Calvello
by Mara Calvello
If you’re reading this, there’s a good chance that your business has a website. To get to that...
 by Holly Landis
by Holly Landis
When you connect to your home wi-fi, you know that your identity and data will be protected...
 by Mara Calvello
by Mara Calvello



