December 4, 2025
 by Samudyata Bhat / December 4, 2025
by Samudyata Bhat / December 4, 2025
Given the rapid pace of technological development, attackers are constantly finding new ways to manipulate and hijack the internet. Domain name system (DNS) poisoning is one such attack, and a disguised one at that.
While DNS security solutions help provide computing power to customers and facilitate their web-based traffic, it’s crucial to understand the threats and risks that can affect them.
DNS poisoning, also known as DNS cache poisoning, is a cyberattack that corrupts DNS lookup data. Attackers insert false IP addresses into a DNS resolver's cache, redirecting users to malicious websites. This attack compromises user trust, enabling phishing, malware distribution, or data theft.
It’s a spoofing attack in which hackers assume the identity of another device, client, or user. This masquerade subsequently makes it simpler to intercept protected information or disrupt regular web traffic flow.
In a DNS cache poisoning attack, hackers alter the DNS records to a "spoofed" DNS so that when a legitimate user visits a website, they end up somewhere other than their intended destination. People often need to be made aware of this since the imitation sites are often designed to seem just like the actual ones.
It’s like if you told someone you live at a specific location and then altered all the street names and house numbers so they wind up at the wrong address or in an entirely different neighborhood.
Hackers often use one or more of the malicious methods discussed below.
To fully comprehend how DNS poisoning works, it’s essential to understand some key concepts and context regarding how the internet directs visitors to various domains.
Although the terms "DNS poisoning" and "DNS spoofing" are occasionally used interchangeably, a distinction exists between the two.
DNS poisoning is a technique attackers use to compromise DNS data and substitute it with a malicious redirection. The end result of DNS poisoning is DNS spoofing, where a poisoned cache directs users to a malicious website.
In summary, DNS poisoning is a precursor to DNS spoofing: hackers poison a DNS cache to redirect DNS queries.
Every device and server has a distinct internet protocol (IP) address, a string of digits that serves as communications identifiers. Users can obtain the IP address connected to a domain name through DNS resolvers. In other words, they convert human-readable website URLs (like https://www.g2.com/) into IP addresses that computers can understand. A DNS resolver receives a request from an operating system whenever a user tries to access a website. After the DNS resolver returns the IP address, the web browser uses it to start loading the requested page.
A DNS resolver keeps track of the answers to IP address requests for a specific period. By eliminating the need to interact with the several servers involved in the standard DNS resolution procedure, the resolver can reply to subsequent queries more rapidly. As long as the stated time to live (TTL) associated with that IP address permits it, DNS resolvers keep replies in their cache data.
Hackers specifically acquire access to a DNS server to change its directory to route the domain name users enter to a different, inaccurate IP address. A hacker could do this by:
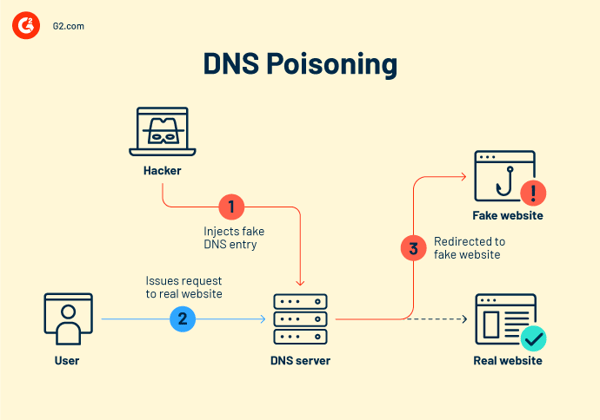
The most significant vulnerability that permits this sort of attack is that the whole system for routing web traffic was designed for scalability rather than security. The present approach is based on the user datagram protocol (UDP), which doesn’t need senders or recipients to authenticate who they are. This vulnerability allows hackers to impersonate users (requiring no extra authentication) and enter the system to redirect DNS servers.
DNS poisoning endangers both individuals and corporations. One of the most likely hazards of this cyber attack is that once a device has been compromised, it can be challenging to rectify the issue because the device defaults to returning to the illicit site.
Additionally, DNS spoofing attacks can be exceedingly difficult for consumers to identify, especially when hackers make false websites seem as realistic as the actual ones. In these circumstances, visitors are unlikely to realize the website is a forgery and will enter important information as usual, unaware that they’re exposing themselves and their businesses to considerable risk.
Some of the most severe risks of this attack are discussed below.
After consumers are steered to fake websites, hackers may obtain access to their devices and install a slew of viruses and malware. This can range from a virus designed to infect their device to malware that grants the hackers continual access to the device and its information.
DNS poisoning allows hackers to quickly obtain information such as logins for secure sites or personally identifiable information like social security numbers.
By rerouting traffic from security providers to prevent devices from getting critical security updates and patches, malicious actors employ DNS spoofing to do severe long-term damage. Over time, this method may render devices more susceptible to several other assaults, including malware and Trojans.
Governments have used DNS poisoning to interfere with web traffic from their countries to enforce internet censorship . By interfering in this way, these governments have been able to prevent citizens from visiting websites that contain information they don’t want them to view.
Address Resolution Protocol (ARP) poisoning and DNS poisoning are examples of machine-in-the-middle attacks. The primary distinction between these two is their addressing formats and the degree to which they occur.
-1.png?width=600&height=375&name=ARP%20Vs%20DNS%20(1)-1.png)
Although DNS poisoning spoofs the IP addresses of genuine sites and has the potential to spread across various networks and servers, ARP poisoning mimics physical addresses (MAC addresses) inside the same network segment.
By poisoning the ARP cache, an attacker can trick the network into thinking that their MAC address is linked to an IP address. This causes data sent to that IP address to be routed incorrectly to the attacker. In turn, the attacker can listen to all network communication between its targets.
High-profile DNS poisoning attacks have historically demonstrated the dangers of this technique. However, it’s important to note that large-scale, classic DNS cache poisoning attacks have become less common in recent years.
This decline is largely due to improved defenses, such as randomized source ports, enhanced resolver hardening, and the broader adoption of security controls like DNSSEC. That said, DNS remains a high-value target, and attackers continue to exploit DNS-level weaknesses through closely related techniques such as DNS hijacking, DNS record manipulation, and infrastructure-level compromise.
The following examples illustrate both the historical impact of DNS poisoning and how modern attacks still achieve similar outcomes.
DNS manipulation has not disappeared; it has evolved. Recent incidents show DNS being abused in more targeted and infrastructure-level ways:
DNS poisoning attacks are highly dangerous because they are difficult to detect and fix once established. Nonetheless, you can take several actions to better safeguard your business against the harm posed by DNS poisoning and phishing attacks.
Defend yourself against DNS poisoning assaults by introducing DNSSEC. Simply said, DNSSEC implements an additional step of verifying DNS data.
DNNSEC uses public key cryptography for this verification. In particular, it uses certificate-based authentication to confirm the root domain and legitimacy of any DNS replying to a request. Moreover, it assesses whether the response's content can be trusted and whether it was altered en route.
While DNSSEC does protect against DNS spoofs, it also has several downsides concerning data confidentiality, its complex deployment, and other vulnerabilities like zone enumeration. It’s essential to be aware of DNSSEC’s limitations before its implementation.
Another crucial step you can take is data encryption in DNS queries and responses. This adds security by prohibiting hackers who could intercept that data from doing anything with it. Even if a hacker manages to collect the data, if it's encrypted, they won't be able to read it to gain the information they need to reproduce it for use in future DNS queries.
While preventative techniques are crucial, you should also have a robust plan if a DNS poisoning assault occurs. This is when effective detection protocols are necessary. The most effective detection procedures include regular monitoring for specific warning indications.
Important warning indicators include:
Like most systems, your DNS is eligible for routine system changes. As these updates frequently contain new security protocols and patches for any discovered vulnerabilities, you must execute these updates consistently to ensure that you’re using the most recent version of your DNS.
A crucial detection strategy is end-user training to inform users of potential threats. Even well-trained users may find it challenging to recognize DNS poisoning attempts, although good training may undoubtedly stop the spread of some assaults.
Users should be trained to check that the website use a legitimate secure sockets layer (SSL) / transport layer security (TLS) certificate to avoid clicking links from unfamiliar sources. This will routinely clear their name server’s cache to guard against DNS cache poisoning and use security software to scan their devices for malware.
Modern DNS protection requires layered controls; no single defense is enough.
Even though general best practices provide some security for domain name systems, several managed DNS providers can detect and block risky traffic. With the filtering of malicious DNS information, media, and websites, organizations employ these service providers to protect the endpoints used by their employees and servers.
G2 helps businesses find the right DNS security solutions to protect web traffic, block malicious domains, and reduce risk across their networks.
*Above are the five leading DNS security software solutions from G2’s Winter 2026 Grid Report.
Got more questions? We have the answers.
Large-scale DNS cache poisoning is less common today due to stronger resolver protections, but DNS manipulation is still actively used in targeted attacks, ISP-level compromises, and malware campaigns.
Signs may include unexpected website redirects, invalid or missing SSL certificates, sudden spikes in DNS queries, or users being sent to unfamiliar login pages.
DNS poisoning involves injecting false DNS data into a resolver or cache, while DNS hijacking typically involves unauthorized changes to DNS records or infrastructure. Both result in traffic redirection.
DNSSEC helps prevent spoofed DNS responses by validating authenticity, but it does not encrypt DNS traffic or protect against all DNS-based attacks. It works best as part of a layered defense.
Yes. DNS poisoning can redirect traffic intended for cloud and SaaS applications to malicious destinations, potentially leading to credential theft, malware delivery, or service disruption, especially if DNS infrastructure or upstream providers are compromised.
A domain name server is essential to the operation of the modern internet. Still, it has also been a frequent target of hackers looking to exploit security flaws, gain unauthorized access to networks, or steal sensitive information. What exactly does this imply for corporations? They might risk monetary and time expenditure losses, damage to their brand reputation, and legal implications.
Apart from being aware of the risks of a domain name system, it’s also crucial that businesses pick and find solutions that guarantee DNS security.
Learn more about DNS security for a robust cybersecurity strategy!
This article was originally published in 2023. It has been updated with new information.
Samudyata Bhat is a former Content Marketing Specialist at G2. With a Master's degree in digital marketing, she specializes her content around SaaS, hybrid cloud, network management, and IT infrastructure. She aspires to connect with present-day trends through data-driven analysis and experimentation and create effective and meaningful content. In her spare time, she can be found exploring unique cafes and trying different types of coffee.
If you’re reading this, there’s a good chance that your business has a website. To get to that...
 by Holly Landis
by Holly Landis
A smooth and secure network operation maintains productivity and operational efficiency, no...
 by Sudipto Paul
by Sudipto Paul
After the year 2000, when technology use and development skyrocketed, the progression of cyber...
 by Elena Georgescu
by Elena Georgescu
If you’re reading this, there’s a good chance that your business has a website. To get to that...
 by Holly Landis
by Holly Landis
A smooth and secure network operation maintains productivity and operational efficiency, no...
 by Sudipto Paul
by Sudipto Paul


