August 21, 2023
 by Soundarya Jayaraman / August 21, 2023
by Soundarya Jayaraman / August 21, 2023
You probably know blockchain is the technology behind Bitcoin, Ethereum, and other cryptocurrencies. But ever thought about what’s the technology behind blockchain? It’s called distributed ledger technology (DLT).
Distributed ledger technology, or DLT, is a decentralized digital system that uses an independent network of computers called nodes. It simultaneously proposes, records, validates, synchronizes, and shares transaction details or data in a shared ledger distributed across multiple places.
Unlike a traditional database, in DLT, data is distributed across multiple nodes or computers rather than stored in a central database. Each node records and verifies every transaction, whether static data like a registry or dynamic data like financial transactions.
As a result, DLT doesn’t have a single point of control or a single point of failure. This decentralized nature enables secure, transparent, and tamper-proof record keeping.
Today, DLT is rewriting the conventional notion of any business transactions and finds use in banking, finance, supply chain management, and healthcare industries. It is the building block for futuristic innovations like decentralized identity solutions and blockchain platforms.
People often consider the launch of Bitcoin in 2009 to be the starting point of DLT. However, the idea and technologies that support DLT existed much before Bitcoin’s introduction.
Since ancient times, ledgers have been at the heart of commerce. People kept notes of their money and assets, from clay tablets and papyrus to vellum and paper. Computerization moved this record-keeping process from paper to bits and bytes as digital ledgers.
Fast forward, advancements in database management systems and distributed computing offered convenience and speed. It allowed databases to be shared across geographies.
Ledgers require a central authority to validate the authenticity of every data it records, whether digital or paper. For example, banks verify and validate all transactions between related entities. Companies often have system administrators to manage their databases.
Such centralized databases, even when distributed across different locations, are susceptible to single points of failure, data breaches, and potential manipulation by the central authority. It introduced inefficiencies and added costs to transactions. The concept of DLT emerged as a solution to these problems.
From the 1970s, several technological breakthroughs in the field of cryptography and computing made DLT a possibility.
In 1976, Whitfield Diffie and Martin Hellman laid the foundation for public key cryptography–the basic tech behind data encryption and decryption used in DLT today.
In 1982, scholars Leslie Lamport, Robert Shostak, and Marshall Pease wrote a groundbreaking paper called The Byzantine Generals Problem that provided the conceptual base for DLT. Lamport et al. illustrated the challenges of achieving consensus in a distributed system when some participants may be malicious or unreliable. They detailed simple algorithms to overcome malfunctioning components in a computer network; faulty devices could send conflicting information to different parts of the system.
Subsequently, a number of scholars proposed different solutions to the problem of how computer systems must handle conflicting information in an adversarial environment. This resulted in the development of different consensus mechanisms that are now used for distributed ledger systems without a central authority.
Another major boost to DLT happened in 1991. Stuart Haber and W. Scott Stornetta proposed a system to timestamp digital documents with a cryptographically secured chain of blocks. Their solution served as a precursor to the blockchain concept.
However, these concepts and algorithms gained little attention before the launch of Bitcoin and its underlying blockchain technology. The practical demonstration of how DLT can be used via Bitcoin brought the technology to the forefront. It attracted significant investment, resulting in the rapid evolution of DLT system types and applications.
Today, the applications of DLT have expanded far beyond cryptocurrencies, from supply chain management, healthcare, and digital identity to decentralized finance (DeFi) and non-fungible tokens (NFT).
DLTs are based on three well-known technologies:
As mentioned earlier, DLT works through a network of computers called nodes. These nodes, located in multiple locations, collectively maintain a shared and synchronized digital database of transactions or data.
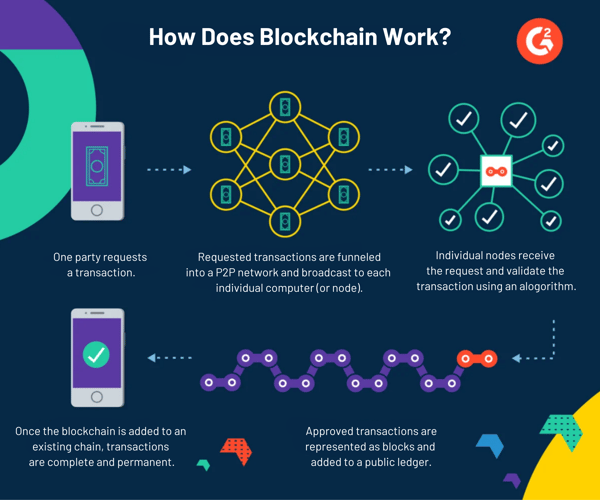
The data structure to store these transactions is typically organized into blocks (in the case of blockchain) or some other suitable format. Here’s a general overview of how DLT works.
A participating node creates a new transaction to be added to the ledger. The new transaction details are secured using public key encryption to create the transaction’s unique digital cryptographic signature. This digital signature includes a public key (shared with other nodes to verify the data) and a private key. As the new transaction is created, a request is sent to other nodes in the distributed P2P network to verify it.
Once the nodes get the request, each node works independently to check the validity of a transaction. They use the public key shared by the transaction initiator to decrypt the digital signature of the transaction and verify it against their predefined rules.
Once verified, the nodes work together to achieve consensus on the validity of the transaction. They employ the consensus algorithm they have agreed upon. This ensures that all copies of the transaction on the ledger are identical.
For instance, take Bitcoin mining. Nodes employ the PoW mechanism, popularly referred to as mining, which includes solving complex mathematical puzzles to validate and add new Bitcoin blocks to the Bitcoin blockchain ledger.
Once the transaction is validated, it is appended to the ledger and distributed across all nodes, updating the ledger's state. The nodes in the distributed ledger network cannot alter or update the transaction details without following the same consensus mechanism again. This ensures the immutability and integrity of the ledger.
Here’s a visual representation of how a blockchain ledger works.
There are different types of DLTs based on the underlying technologies used and the access provided to a distributed ledger. Each offers distinct advantages and caters to specific use cases. Let’s see in detail about these DLT types.
The three types of DLTs based on who can participate in a distributed ledger network are:
A permissioned ledger requires participants to be approved before joining the network. Authorized nodes maintain the ledger. Permissioned platforms enable faster validation of transactions and offer improved privacy.
For example, Facebook’s Diem stable coin project (formerly known as Libra) was a permissioned DLT. Only the members of the Diem Association were granted the validation authority. Another example would be the hyperledger fabric, an open-source blockchain by the Linux Foundation designed for enterprise use.
In a permissionless distributed ledger, anyone can join the network without approval, i.e., it is public. The ledger is maintained by collaborative action among nodes in the public network and is accessible to everyone. Bitcoin, Ethereum, and Litecoin blockchains are examples of public DLTs.
This type of DLT combines the privacy benefits of a permissioned distributed ledger system with the transparency of a permissionless distributed ledger system. Hybrid DLT provides businesses significant flexibility to choose what data they want to make public and what data they want to keep private.
The six types of DLT, depending on the type of consensus mechanisms and data structure used, are:
Blockchain is the most well-known DLT type. The data in this type of DLT is structured as a list of blocks. Each block represents a collection of data. It relies on miners to select and aggregate the data into a sequential chain of blocks.
All blocks are cryptographically linked to the previous one, forming an immutable and transparent ledger. Blockchains can be public or private, depending on the network's design. Blockchain applications range from cryptocurrency and decentralized identity to smart contracts.
Unlike the sequential list structure followed by blockchain, DAG adds transactions as a directed graph or a tree-like structure. Each transaction confirms multiple previous transactions, creating a web of interconnected transactions without forming a strict chain. As multiple transactions get processed simultaneously, DAG provides higher transaction throughput and faster confirmation time than blockchain. This enables a more scalable and efficient decentralized network.
Tangle is an open-source DAG-based DLT designed for the Internet of Things (IOT) by the Internet of Things Applications (IOTA) organization. A node issuing any new addition to the ledger must approve two previously submitted transactions, making the data addition and validation easier than blockchain.
This also removes the need for miners or the mining process to approve transactions on the ledger, unlike Blockchain. This process makes Tangle low-energy-consuming tech.
Sidechain is a secondary distributed ledger system connected to a main system through a two-way peg. The two-way peg enables the bidirectional transfer of transaction data. Sidechains may have their own consensus mechanism, separate from the main chain. It is primarily used in blockchain to scale the main ledger.
Holochain is a unique DLT designed to facilitate decentralized applications. It uses an agent-centric approach inspired by GitHub and BitTorrent. There is no global consensus. Instead, each node in the network is considered an autonomous agent responsible for its data and interactions, providing strong control over its data.
Hashgraph is another DAG-based DLT. It uses a virtual voting algorithm and gossip protocol as part of its consensus mechanism. With the gossip protocol, the nodes continuously communicate all transaction data to other nodes randomly, allowing the transaction information to proliferate rapidly throughout the network.
Proponents of DLT highlight several potential advantages over traditional centralized ledgers and other types of shared ledgers. That said, the technology is still evolving and may pose new risks and challenges. Let's look at the advantages and disadvantages of DLT to get a sense of its potential and limitations.
Below are the most important advantages of DLT, though generalizations are difficult because of the development of different types of DLT.
Since DLT is still evolving, many regulatory and legal issues are yet to be resolved. Here are the most common technological, legal, and regulatory challenges related to DLT:
As mentioned earlier, DLT has a wide range of potential applications across various industries. Let’s dive deep into some of the use cases of DLT across different industries.
DLT, particularly blockchain, is an integral part of the fintech revolution. DLT’s applications are found from banking and payments to insurance and compliance.
The potential applications of DLT include smart contracts, digital currencies, cross-border payments, trading and settlement of securities, asset registrations, etc. Many banks and financial institutions are running proofs-of-concept to explore the feasibility and gauge the impact of different DLT technology for these use cases.
US banks, for instance, are running a pilot project for a digital asset settlement project using a distributed ledger. Central banks of many countries are also exploring central bank digital currencies (CBDCs) based on blockchain technology.
One of the most promising use cases of DLT is supply chain management. Early initiatives have shown how DLT makes products more traceable, streamlines invoicing, enables faster and cost-efficient delivery, and improves coordination among suppliers, buyers, and financing institutions.
Walmart Canada, for example, employed blockchain technology and created an automated system for managing invoices from and payments to its 70 third-party freight carriers. This system reduced disputes related to invoice discrepancies from over 70% to less than 1%.
Keeping health records secure is one of the most popular applications of DLT in the healthcare sector, given the industry reported 707 data breaches in 2022 alone. DLT makes it easier to store and share electronic health records safely with its encryption techniques. Tracing their supply chain helps track and verify the medicines and pharmaceuticals devices. DLT supports recording data from clinical trials too.
For example, Mayo Clinic is experimenting with a blockchain platform to record and manage data from its clinical trial for hypertension.
The potential applications of DLT in real estate range from easing property searches and streamlining property title management to ownership transfers. This reduces paperwork and administrative costs while providing data protection and an immutable record of property ownership.
Another use case being explored simultaneously by the finance and real estate sector is how real-world assets can be converted into digital tokens for trading. Such tokenization promotes asset liquidity, fractional ownership and lowers transaction costs.
DLT has the opportunity to deliver government services better and faster. It finds use in securely maintaining various government databases, providing digital government certificates, and easing asset registrations.
Estonia, for instance, uses blockchain to maintain its healthcare, property, and business registry. It also provides digital IDs for its citizens, who can use them to avail government services.
There have been years of hype-cycle around DLT, blockchain, and its capabilities. But the hype is giving way to practical use cases.
As organizations graduate from pilots and proofs-of-concept to more practical, real-world initiatives, DLT adoption is set to accelerate. Moreover, as the technology matures, scalable solutions will emerge, addressing the limitations that hinder widespread adoption. So, embrace the distributed future with unlimited possibilities.
Explore more about the proof of stake consensus mechanism that is set to play a pivotal role in the future of decentralized technologies.
Soundarya Jayaraman is a Senior SEO Content Specialist at G2, bringing 4 years of B2B SaaS expertise to help buyers make informed software decisions. Specializing in AI technologies and enterprise software solutions, her work includes comprehensive product reviews, competitive analyses, and industry trends. Outside of work, you'll find her painting or reading.
When you hear “blockchain,” you might instantly think of Bitcoin or other cryptocurrencies....
 by Washija Kazim
by Washija Kazim
Tired of handing over your data to every platform you use?
 by Soundarya Jayaraman
by Soundarya Jayaraman
In today’s remote-first world, businesses face challenges like securing desktop access,...
 by Sagar Joshi
by Sagar Joshi
When you hear “blockchain,” you might instantly think of Bitcoin or other cryptocurrencies....
 by Washija Kazim
by Washija Kazim
Tired of handing over your data to every platform you use?
 by Soundarya Jayaraman
by Soundarya Jayaraman


