Mine or stake? It’s time to make a choice.
Consensus mechanisms like proof of work (PoW) and proof of stake (PoS) are the core components that link blockchain technology together. They address the challenges of trust and security in decentralized environments and create a way for users to reach an agreement on conduct.
Both PoW and PoS help to judiciously decide the state of the network, avoid double spending, and maintain the integrity of blockchain transactions.
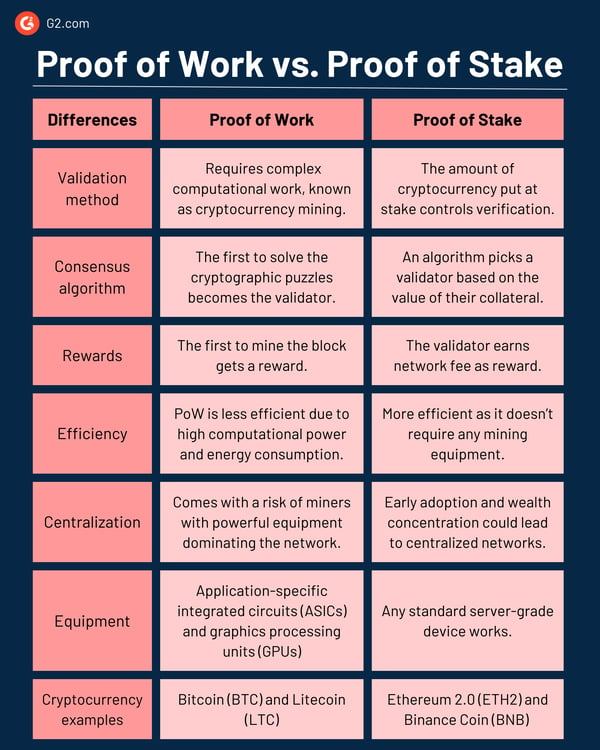
Proof of Work (PoW) and Proof of Stake (PoS) are methods used to secure and validate blockchains. The choice between PoW and PoS depends on specific needs. PoW relies on miners competing to solve puzzles, while PoS selects validators based on staked cryptocurrency. PoW offers strong security but is energy-intensive. PoS is faster and more efficient, but security depends on stake distribution.
Think of PoW as a race where participants compete against each other to win. PoS, on the other hand, is more like a voting system where individuals with the highest stake have a better chance of winning.
Regardless of the method, network participants must use cryptocurrency wallets to manage and secure their block rewards and validation incentives.
Both PoW and PoS have a dedicated space in the world of cryptocurrencies and blockchains. The final choice of consensus mechanism depends entirely on the goals of each blockchain network and its community’s preferences.
As the original consensus mechanism, PoW is often favored for its security and proven reliability. PoS is chosen for its scalability benefits and reduced environmental impact. Some blockchain networks go for hybrid models.
This detailed overview gives you more information for further consideration.
But how do blockchain users choose what aligns best with their priorities? Let’s find out.
The Bitcoin network first implemented proof of work in 2009, paving the way for other cryptocurrencies. The decentralized nature of PoW allows anyone with the necessary equipment to participate in mining. PoW became the first widely used consensus mechanism to validate cryptocurrency transactions without relying on a third party.
Under PoW, all the computers or nodes in a network compete with each other to solve complex cryptographic puzzles, a process we call cryptocurrency mining. The fastest miner adds new blocks to the blockchain and receives the newly minted digital currency and transaction fees as incentives.
Several blockchain networks and cryptocurrencies use proof of work, including:
PoW offers a robust approach to securing decentralized systems like blockchains. Its dependence on computational work and incentives promises a high level of trust in the world of cryptocurrencies. The benefits below also make PoW a go-to choice among miners.
As the PoW network continues to grow and the time involved in solving puzzles increases, users are bound to face slower transaction processing times. It also comes with other challenges, such as:
Considering the inefficiencies PoW came with, establishing a sustainable consensus mechanism was the need of the hour. As a result, a new energy-efficient method called proof of stake was introduced in 2011.
Unlike PoW, which had a competitive validation process, PoS chose validators based on the amount of cryptocurrency they held and their willingness to "stake" as collateral. The higher the stake, the higher the chances of being selected to add the new block of transactions to the ledger. Simply put, a cryptocurrency owner needs to own the most native crypto coins on a blockchain to be selected as a validator.
Since PoS doesn’t require high computational power or energy consumption, many cryptocurrencies prefer it over PoW. A few examples include:
PoS has become a widely used consensus mechanism compared to its energy-intensive alternative, PoW. It offers many other benefits, like:
Despite stopping endlessly consuming computations, PoS comes with inevitable trade-offs and potential challenges, like:
Did you know? A PoS network consumes less than 0.001% energy than a PoW network.
PoS and PoW serve the same purpose for blockchain consensus, but their functionality differentiates them.
While PoS doesn't require the computational power required in PoW, it has its own technical complexities essential for network integrity and security. PoS follows a set of consensus algorithms that define validator selection, staking mechanisms, and reward distribution.
The selection algorithm under PoS takes into account the amount of staked cryptocurrency and, to maintain fairness, a randomization element. Some additional criteria, like the age of coins and transaction history, are also considered. To stay transparent, PoS uses smart contracts to enforce the crypto staking rules, including penalties for bad actors.
All of these elements, along with many others, maintain the security, fairness, and reliability of PoS networks.
When it comes to PoW, the choice of mining hardware plays a substantial role. The two common types are application-specific integrated circuits (ASICs) and graphics processing units (GPUs).
ASICs are custom-built specialized devices that mine cryptocurrency using the hashing algorithm of the PoW network. They’re energy-efficient, optimized for speed, and made to outperform general-purpose hardware like GPUs. However, ASICs create the problem of centralization because participants need financial resources to purchase and operate them.
On the other hand, GPUs can be used for various computing tasks in addition to crypto mining. Less specialized than ASICs, but they offer higher flexibility due to a broad set of applications. GPU mining is suitable for cryptocurrencies resistant to ASIC mining. There’s also CPU mining that’s relevant for such applications.
Still debating? Find more answers to your queries below:
Both proof of work and proof of stake have different benefits and challenges. PoW offers strong security, but it's not easily scalable and consumes high energy. PoS is faster and consumes less energy, but the security depends on the stake distribution between participants.
If a small group of stakeholders holds a majority of the staked coins, the PoS network is vulnerable to attacks. PoS is a relatively new technology. While it shows promise, its long-term security needs more time to match the track record established by proof of work.
The choice between PoW and PoS depends on the specific needs and priorities of the project. Carefully weigh the trade-offs between security, scalability, energy efficiency, and decentralization to make the best decision for your project within a blockchain network.
There’s no perfect system. The debate on proof of work vs. proof of stake is ongoing and essential to the blockchain and cryptocurrency community. Many multi-chain blockchain solutions meet different communities' needs by offering the best of both worlds.
Ultimately, scalability requirements, energy considerations, and specific use cases direct the course. One thing that’s for sure is that both PoW and PoS are shaping the future of decentralized finance and digital assets.
Regardless of what you choose, always invest wisely. Check out the latest cryptocurrency statistics to stay updated on market trends.
This article was originally published in 2023. It has been updated with new information.
Washija Kazim is a Sr. Content Marketing Specialist at G2 focused on creating actionable SaaS content for IT management and infrastructure needs. With a professional degree in business administration, she specializes in subjects like business logic, impact analysis, data lifecycle management, and cryptocurrency. In her spare time, she can be found buried nose-deep in a book, lost in her favorite cinematic world, or planning her next trip to the mountains.
In the world of crypto, coins speak louder than words.
 by Washija Kazim
by Washija Kazim
Watch any old science fiction movie and you’ll come away with at least two conclusions: no one...
 by Krystall Fierens Lee
by Krystall Fierens Lee
In the world of crypto, coins speak louder than words.
 by Washija Kazim
by Washija Kazim
Watch any old science fiction movie and you’ll come away with at least two conclusions: no one...
 by Krystall Fierens Lee
by Krystall Fierens Lee



