October 28, 2020
 by Yaniv Yagolnitzer / October 28, 2020
by Yaniv Yagolnitzer / October 28, 2020

Cybercriminals have a wide variety of tools available to them today. One of the most fundamental and most dangerous tools is the botnet.
Almost all cyberattacks today use botnets in one form or another. Even attacks waged directly by a human hacker, such as manual penetration attempts, are usually preceded by botnets probing the targeted network and performing vulnerability scans. Therefore, it’s vital for executives to understand how botnets work, and how to defend their networks against them.
As the name implies, a botnet is a network of bots.
“Bot” is an abbreviation for web robot, also known as an “internet bot” or “www robot”. A bot is a software application that automatically performs activities that a human might otherwise do. Bots are widely used today, because a bot can perform many activities faster, and at a larger scale, than a human.
Not all bots are bad. In fact, there are different types of bots, including many good bots that are welcome on most sites. Search engine spiders and web shopping engines are probably the most common examples of good bots.
However, botnets are comprised of hostile bots; malicious software programs that are running on a large network of compromised devices. Each bot communicates periodically with a central C&C (Command and Control) server; this is how the hacker controls the botnet and issues instructions to the bots, commanding them to wage various attacks. The owners of the compromised devices where the bots are running are usually not aware that any of this is occurring.
Botnets can be categorized by the types of devices that they run on. The most powerful botnets tend to be large networks of personal computers. Hackers build these networks by installing malicious software on the machines; one common way is to send out spam email that contains a Trojan attachment, or perhaps a hostile link that will, when clicked, lead to the installation of the bot program. However it is built, a botnet running on infected PCs is a highly coveted tool for hackers, since the underlying PCs have a wide variety of capabilities.
At the other end of the spectrum are botnets made up of Internet of Things (IoT) devices. Over the last few years, many Internet-connected “smart” devices have come on the market: everything from thermostats to doorbells to security cameras. Unfortunately, many of these devices do not have robust security, and hackers have been able to compromise countless numbers of them, enslaving and incorporating them into massive botnets.
Because IoT devices are much simpler and much more limited in their capabilities than PCs, IoT botnets are capable of less complex attacks than PC-based botnets. For example, most IoT devices do not have email software, while most PCs do; thus, PC botnets can be used in huge spam email campaigns, while IoT botnets cannot.
However, whatever is lacking in quality can be compensated for with quantity; some IoT botnets are massive, containing hundreds of thousands of enslaved devices. These networks tend to be used for simpler volumetric attacks like DDoS, where the quantity of traffic generated is the primary feature of the attack.
Botnets are used for many different kinds of attacks today. Here are some of the most common.
In a DDoS attack, a botnet will generate large amounts of traffic, all aimed at one target. The hacker’s goal is to send to the targeted site or web application an overwhelming volume of incoming HTTP requests, to make it unavailable to the intended users. The ideal outcome (from the hacker’s perspective) is to crash the target completely and take it offline.
However, even a severely degraded performance would be considered a success. Modern DDoS attacks can reach staggering volumes; as this article is being written, the current record is a 2.3 Tbps attack that was aimed at an organization using Amazon Web Services. No doubt, this record will be broken soon by an even larger attack.
In the early days of the internet, email spammers would use a small number of computers to send massive quantities of messages. Security firms adapted, and began publishing the IP addresses of these computers, making it easy for security software to block them.
Today, spammers avoid this by using large botnets to accomplish their goals instead. Each enslaved device sends out relatively few messages, which makes it much harder for security organizations to identify the sources of a spam campaign. However, the size of the botnet means that the spammer can still send out thousands or even millions of messages in a short time. Also, some botnets can do this not only with email, but also can generate SMS spam.
Botnets conduct vulnerability scans; they systematically probe networks across the Internet, looking for systems with known vulnerabilities that have not yet been patched. When exploitable systems are found, hackers follow up with direct breach attempts and other attacks.
Sometimes a vulnerability scan will not be followed by human intervention. For some types of vulnerabilities, when a large number of potential victims are found, a botnet will be used to visit the vulnerable systems and infect them with malware. Popular choices here include ransomware, or for individual machines, sometimes the bot software is installed, which will absorb each new machine into the botnet.
Sites and web applications which accept user-generated content (such as product reviews, comments, and so on) are often plagued by botnets. The bots create fake accounts and then attempt to add spurious “content”, such as small chunks of text containing backlinks to a particular site. The hacker’s primary goal is to boost the linked site’s visibility in the search engines, and perhaps even to get a few visitors who arrive directly by following these links from the victimized web application.
When hackers breach large websites, they often harvest thousands of credential sets such as username and password combinations. They know that unfortunately, many people still use the same credentials across many different websites. Therefore, once hackers obtain a list of account credentials from one site, they will attempt to log into many other sites with the stolen credentials.
This credential stuffing is very common; a botnet will visit a high-profile site where hackers want to takeover accounts, and systematically “stuff” stolen credentials into the site’s login form. Usually, at least some of those login attempts will succeed, which means the attacker can then take control of those accounts on the new site. The botnet is a vital part of this process, since it usually involves many thousands or even millions of systematic login attempts, which would be beyond the capacity of a human attacker.
Threat actors use botnets to validate stolen payment cards. Bots stuff the card numbers into web applications to see if they are accepted or rejected. A similar technique is used to discover new cards; bots cycle through potential numbers and enter them into web applications. This is a crude, but effective, way to steal additional cards that were previously unknown to the attacker.
Hackers use botnets to scrape sites and web applications, copying data for various illicit purposes. In some industries (e.g., e-commerce, insurance, and several others), pricing data is valuable information; in fact, shady businesses sometimes hire threat actors to scrape competitors' sites to obtain it. In other industries, such as data aggregation, businesses are selling access to content, and botnet scraping is a direct threat to the business model.
Threat actors often use botnets for highly specialized purposes, customized to the organization that is being targeted. One common example is inventory denial, where a botnet is used to access a commercial website or mobile application, and begin a purchase process, without ever completing the transaction. This can remove items from inventory for a specified time, which denies actual customers the ability to purchase them. Along with the lost revenue from the sales that were prevented, this can cause additional problems for the victim.
It is common for botnets to attack travel sites and applications; the bots query flight schedules and begin to make reservations – which removes the seats from inventory for a set time, usually 10 or 15 minutes – but never purchase tickets. Not only does this remove many seats from available inventory at any given time, it can also incur large data-lookup fees for the travel site.
Many travel sites rely on external data feeds for flight schedule information, and pay for it on a per-query basis; thus, the bot activity inflicts direct financial damage on the target.
Anyone involved in cybersecurity knows that a robust defense against hostile bots is essential today. The botnet attacks described above occur very frequently.
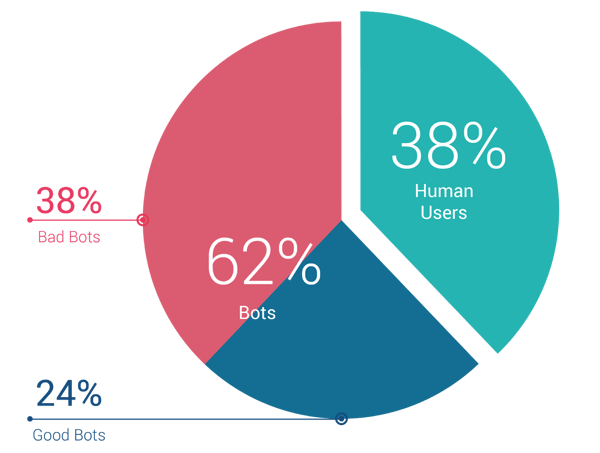
Bots comprise almost two-thirds of web traffic today. Some are good bots, such as search engine spiders. The remainder – more than half of all bots – are hostile. Source: Traffic processed by Reblaze (over eight billion HTTP/S requests per day)
There are many reasons for this. Botnets are common, and new ones are always being built. Cybercriminals use botnets because they are necessary. Most of the attacks described earlier would not be possible without them.
Today’s threat actors include everything from organized-crime rings in Russia to state-sponsored hackers in China. Most hackers are sophisticated and highly-skilled; many are also well-financed. They will use whatever tools are necessary to accomplish their goals. Therefore, bigger and better botnets are always being constructed.
A threat actor who controls a robust botnet has many opportunities for profit. Here are a few.
Hackers will launch a massive DDoS against a site, then send a ransom demand to the site’s owner. They threaten to maintain the attack until the ransom is paid. A successful DDoS can prevent customers from accessing a site or application, so site owners will often pay the ransom, instead of sustaining the continual loss of revenue from the attack.
As mentioned earlier, botnets can be used to steal many types of valuable information. Some types of data, such as payment card numbers, can be used directly by hackers and/or be resold on the dark web, where there are large, mature marketplaces for this purpose. Valid account credentials are also quite valuable.
Years ago, most spammers were sending mass emails to sell shady products or perpetrate other scams. Today, phishing campaigns and other illicit activities are rampant. Furthermore, botnet owners can profit not only by sending out their own messages, but also by offering spam-as-a-service to other criminals.
Botnets are often rented out to so-called “SEO services” who perform link-drop campaigns across the web.
Along with spam and SEO, hackers can rent out botnet resources for a wide variety of purposes: advertising fraud, application abuse, scraping, and more. There is now an active market for this, as we’ll discuss next.
The dark web is perhaps best known for file-sharing and sales of illegal drugs. But it is also the home of many forums and underground marketplaces for cybercrime.
Hackers with various specializations and skill sets offer their services for hire. Attack tools and other software are sold in online markets where buyers can rate the products and leave reviews. And botnets can be rented by the hour, day, or week.
Years ago, a threat actor who wanted a botnet had to construct one from scratch, which is a difficult and expensive task. Today, a generic DDoS botnet can be rented for as little as $50 per day. When attack resources are so abundant, and are available so inexpensively, it is unsurprising that botnet attacks are so common.
Because botnet attacks come in different forms, a proper defense against them must be mounted on several different fronts. Best practices can be categorized as specific measures against DDoS, specific measures against other volumetric attacks, and general principles that apply against all bot attacks.
Of all botnet attacks, DDoS attacks are the most dramatic type. The sheer size and scale of a modern DDoS assault can be staggering, and a web application with insufficient resources can be quickly overwhelmed.
Fortunately, it is straightforward for a site to have the bandwidth and other resources to withstand a DDoS today. Modern cloud platforms make it simple to set up auto-scaling for web applications, so that additional resources come online quickly and automatically when demand escalates.
If your site doesn't have this in place already, you should add it soon. Also, if you aren’t currently running your web security solution to the cloud, consider migrating it there. Then it too will be able to autoscale dynamically in response to changing threat conditions. The protected web applications will rarely have to autoscale because DDoS traffic will never reach them.
While you’re considering your DDoS defenses, make sure that you’re aware of all the options available to you today. DDoS protection services are becoming widely available; for example, the top-tier cloud platforms now include built-in mitigation for volumetric DDoS on the network and transport layers. You should take advantage of whatever services are available to you.
Other tips include using a CDN to serve static content; this can reduce the impact of volumetric attacks. Traditionally, this was done mostly for individual files (images, media, scripts, and so on), but today there is a larger trend towards making entire pages static whenever possible. This can reduce the site’s attack surface for non-volumetric threats, and as a bonus, will also improve the system’s perceived responsiveness to your users.
Some forms of bot attack still require the botnet to send large volumes of traffic, but its goal is not to overwhelm the target. A common example is credential stuffing: a botnet might try to access one login form many thousands of times. Thus, the attack is volumetric (it includes a large volume of requests being sent to the target), but are not intended to inflict a DDoS.
Defeating these attacks can be challenging, because it requires the targeted web application to recognize that a large-scale attack is occurring, so it can deny the requests. However, a sophisticated botnet will rotate its requests rapidly through its enslaved devices. The target might only receive one request from any given IP address. Because traditional rate-limiting algorithms count the requests coming from each traffic source, these algorithms cannot defend against these types of attacks.
Therefore, a robust defense today must include solid bot management and human verification capabilities. The web security solution must be able to detect automated traffic, regardless of how many (or how few) requests were sent by that specific traffic source to the protected application.
Older security solutions relied on blacklisting, signatures, browser verification, and a handful of other techniques to detect hostile bots. These techniques are not adequate anymore. To reliably detect the latest-generation bots and application-level attacks such as inventory denial, modern security solutions include features such as behavioral profiling. They learn and understand the characteristics and behavioral patterns of legitimate users for the applications that they are protecting. This enables them to identify malicious traffic sources and block them.
Finally, we should mention a few best practices that might seem obvious, but are often overlooked anyway. First, your web applications should enforce strict security policies, e.g. when a site experiences several failed login attempts for a given account, that account should be temporarily banned/disabled to prevent ATO (account takeover) attacks.
Second, your network must be as opaque as possible. When error conditions occur, it should respond appropriately, with minimal information. This will prevent hackers from learning backend implementation details, which will make it more difficult for them to discover vulnerabilities.
Speaking of vulnerabilities, we’ll conclude this section with advice that will seem very obvious, but must be said nevertheless: your network must be kept up-to-date! Your organization needs strict internal policies to ensure that security patches and upgrades are installed as soon as they are issued, because botnets are always searching for systems with unpatched vulnerabilities.
You’ve probably heard this advice countless times before. Yes, and so has everyone else. Nevertheless, it is still often ignored by large organizations which certainly should know better.
The most notorious recent example is the Equifax breach, which compromised private financial information for 147 million consumers. The company was penetrated through a flaw in Apache Struts, for which a patch was released (but not applied by Equifax) several months before the breach occurred.
Don’t be like Equifax. Remember: if you leave a security hole in your network, the bots will find it – guaranteed.
Botnets are an ubiquitous part of the modern threat environment. Failure to maintain adequate defenses against them will make your organization vulnerable to a variety of attacks, including DDoS, spam, vulnerability scans – followed by penetration testing attempts and system breaches, account takeover attacks, scraping and data theft, application abuse, and more.
Fortunately, following best practices can exclude hostile bots from your network. This task isn’t necessarily easy; among other things, it requires a modern web security solution that is equipped to detect the latest generations of malicious bots. But it is possible, and it’s never been more important for your organization to ensure it has adequate protection.
Yaniv Yagolnitzer is the COO of Reblaze and manages its global network of operations, which includes 24/7 international support. His extensive experience includes work for companies such as Bezeq International and Anyoption. Yaniv’s qualifications include Oracle DBA, RedHat Certified Engineer, and others.
Not all history is written by humans. Some is logged by malware.
 by Washija Kazim
by Washija Kazim
There’s no “I” in “technology.”
 by G2 Staff
by G2 Staff
Ask any programmer and they’ll tell you what they think about JavaScript.
 by Serge Bezborodov
by Serge Bezborodov
Not all history is written by humans. Some is logged by malware.
 by Washija Kazim
by Washija Kazim
There’s no “I” in “technology.”
 by G2 Staff
by G2 Staff


