Not a day goes by that we don’t access the internet in some form or fashion.
Whether it’s shopping online, accessing our favorite streaming service, or posting on social media, it’s become an integral part of our daily lives.
Because of this heavy internet usage and dependency, we are very vulnerable to cyber-attacks. Luckily, browsing the internet is made smarter and safer with a virtual private network (VPN).
What is a VPN?
A virtual private network or VPN creates a secure connection to another network over the internet. This allows secure sending and receiving of data over shared or public networks on various devices, giving users enhanced privacy and anonymity when browsing the internet.
According to IBM, the average cost of a data breach in the US is as much as $9.44 million.
Due to the rise in cybercrime, it’s never been more important to ensure that our data is kept private. Using a VPN provides peace of mind when you need to access your company’s network remotely, block your internet protocol (IP) address, or simply make sure your online presence is kept non-public. Let's take a deeper dive into what is a VPN and what does it do?
What is a VPN used for?
There are many instances in which a VPN can be useful. For example, a business protects all of its data by storing it within a private network.
This is typically done on a server, an actual computer, or a cloud-hosted service. Because company data must be secured, the network that is being used should be private.
If a business has a team of remote workers or employees that travel often, a VPN extends that private network, making it virtual and giving it the ability to be accessed anywhere.
This allows these employees the ability to securely join the network by using VPN connections. Using a VPN means that this can all be done safely by continuing to keep all company data private.
To fully understand a VPN, just break down its name.
- Virtual: When using a VPN, a user will have a private connection directly to any website, or another computer or device connected to it.
- Private: All website visits or any other online activity, like streaming entertainment, is strictly between the user and the website being visited.
- Network: A VPN user has access to a specific network within the VPN server, which encompasses a specific location.
Want to learn more about Business VPN Software? Explore Business VPN products.
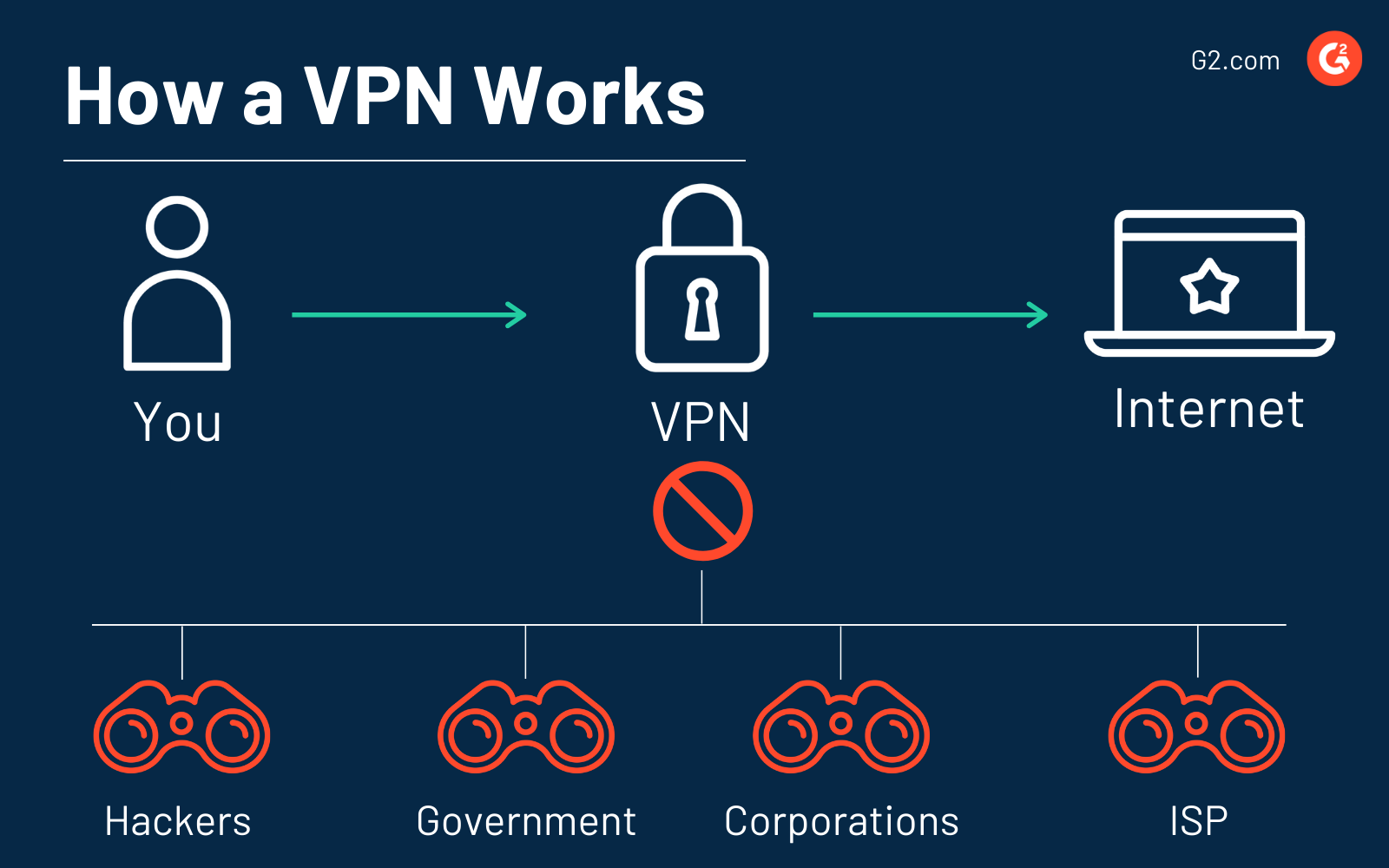
How does a VPN work?
When you aren’t using a VPN and you access a website on the internet, your internet service provider (ISP) redirects you to the website that you want to visit. All your internet traffic passes through your ISP’s servers, which means they can see and log everything you do online.
When you use a VPN, it redirects your internet traffic through a configured remote server. Then, the VPN hides your IP address and encrypts all the data that you send or receive.
The VPN acts as an intermediary as you connect to the internet — it hides your IP address and protects your personal information. If someone were to try and intercept the data, like a hacker or someone trying to steal your identity, the data wouldn’t be readable, essentially looking like gibberish.
This is done by creating a secure tunnel that protects your device’s connection to the internet. The tunnel is cited by first authenticating the device with a VPN server.
Then, the server applies an added level of protection, called the encryption protocol, to all of the data going back and forth between the device and the destination.
Before your data reaches its destination, all of your sensitive information is split into packets. For added protection, the VPN takes each data packet and encloses it into an outer packet, which is then encrypted through a process called encapsulation.
This extra packet keeps all sensitive data secure as it makes the transfer from the device to the destination within the tunnel.
Once the data has arrived safely at its destination, the decryption process can begin.
It’s important to remember that when the packet of data reaches the destination, it will arrive with a new IP address supplied by the VPN. Because of this, if you connect to a server in another country, it will appear that you’re browsing from that country.
How VPN encryption works
The encryption hides information that cannot be read without a specific password, which is known as a key. This key is used to break the complicated code that personal data is turned into.
The only possessors of this key are your device and the VPN server. The process for decoding this data, known as decryption, is how the information is made readable again through the application of the key.
The process of VPN encryption is done in three steps:
- Once a connection is made within the VPN, your data is encoded within a secure tunnel, making it unreadable as it travels from your device and the VPN server.
- Your device is now seen as being on the same network as the VPN, so the IP address being used is one of the VPN provider’s servers.
- You can browse the internet however you please, accessing a variety of websites and software solutions, as the VPN protects your personal information.
Encryption is used in more than just VPNs. For example, think of all of the times you enter your credit card number when shopping on a secure website. Your credit card number and all of your other private information is encrypted, making it unreadable until it reaches its end destination. In this case, the end destination would be the website you’re buying from.
Thanks to the process of encryption, a VPN can successfully hide things like:
- Your browsing history and web activity
- Your IP address
- Your location
- Your data on a device
Why use a VPN?
At this point, you may be asking if a VPN is worth using and what the benefits of using a VPN are in the first place. There are many benefits and reasons why people are consistently turning to VPNs. Let’s break them down.
To change an IP address
Your IP address works like your phone number or home address in the sense that it tells websites where you are and how to connect to your device. When you use a VPN, it provides you with a new IP address, so all of your traffic will look like it’s coming from somewhere else.
To stay safe when using public WiFi
It’s not uncommon to travel to the nearest library or coffee shop with your device and join the public WiFi. We do it all the time -- but so do hackers.
All they need is some simple equipment and they can have access to your usernames and passwords when they pass through a shared WiFi point. Using a VPN encrypts this information, making it unreadable to a hacker.
To block online tracking
How many times have you searched for a new pair of shoes online only to see an ad for those same shoes on a different website five minutes later? Or maybe you’ve shopped online for onesies for your best friend's newborn, only to be shown ads for baby clothes for the next six months.
It’s happened to all of us, but when you use a VPN, you can stop advertisers from invading your online privacy by targeting your IP address for ads. Encrypting your traffic and replacing your IP address, stops you from leaving an online footprint that an ISP or third-party agency can track.
To travel safely
Whether you’re traveling for work or want to check in on things when vacationing, you may find that you don't trust the WiFi at your hotel.
Thanks to VPN encryption, you can safely check your email, book a new flight home, or transfer money to your bank account. This means you can access both your company’s network to access work documents and your home network, no matter how far away you are.
To download files
Whether you want to admit it or not, a VPN will come in handy when downloading files using BitTorrent, which is a communication protocol for peer-to-peer file sharing to distribute data and files over the internet.
Peer-to-peer is one of the fastest and most effective methods for sharing large sets of data over a network. Regardless, many ISPs discourage internet users from this kind of file sharing.
If your ISP is making something like BitTorrent extremely slow, you can choose to use it through a VPN, allowing access to faster speeds and easy sharing.
To avoid internet censorship
If you find yourself traveling to a foreign country, a VPN can help you bypass internet censorship and access services that may be blocked. For instance, China blocks some social media platforms, like Facebook. If you find yourself vacationing there, you could also lose access to certain websites.
Since a VPN can change your IP address to make it look like you’re located elsewhere, you can connect to a VPN server in your home country, allowing you to access all of your favorite websites.
Tip: Find out if using a VPN is legal in the country you live in or the country you’ll be traveling to.
Types of VPN
There are essentially two types of VPNs that you can use. Which one you choose is going to depend on what you’re using the VPN for.
1. Remote access VPN
A remote access VPN allows a user to connect to a private network and access all of its services and resources while being completely remote.
The connection created between the user and the private network happens through the internet, allowing the connection to be completely private and secure. This type of VPN is typically useful for both home users and business users alike.
For instance, a home user typically uses a VPN to bypass any regional restrictions on the internet and access blocked websites. An employee of a company who is currently working remotely can use a VPN to connect to their company’s network, allowing them to access files and resources on a private network.
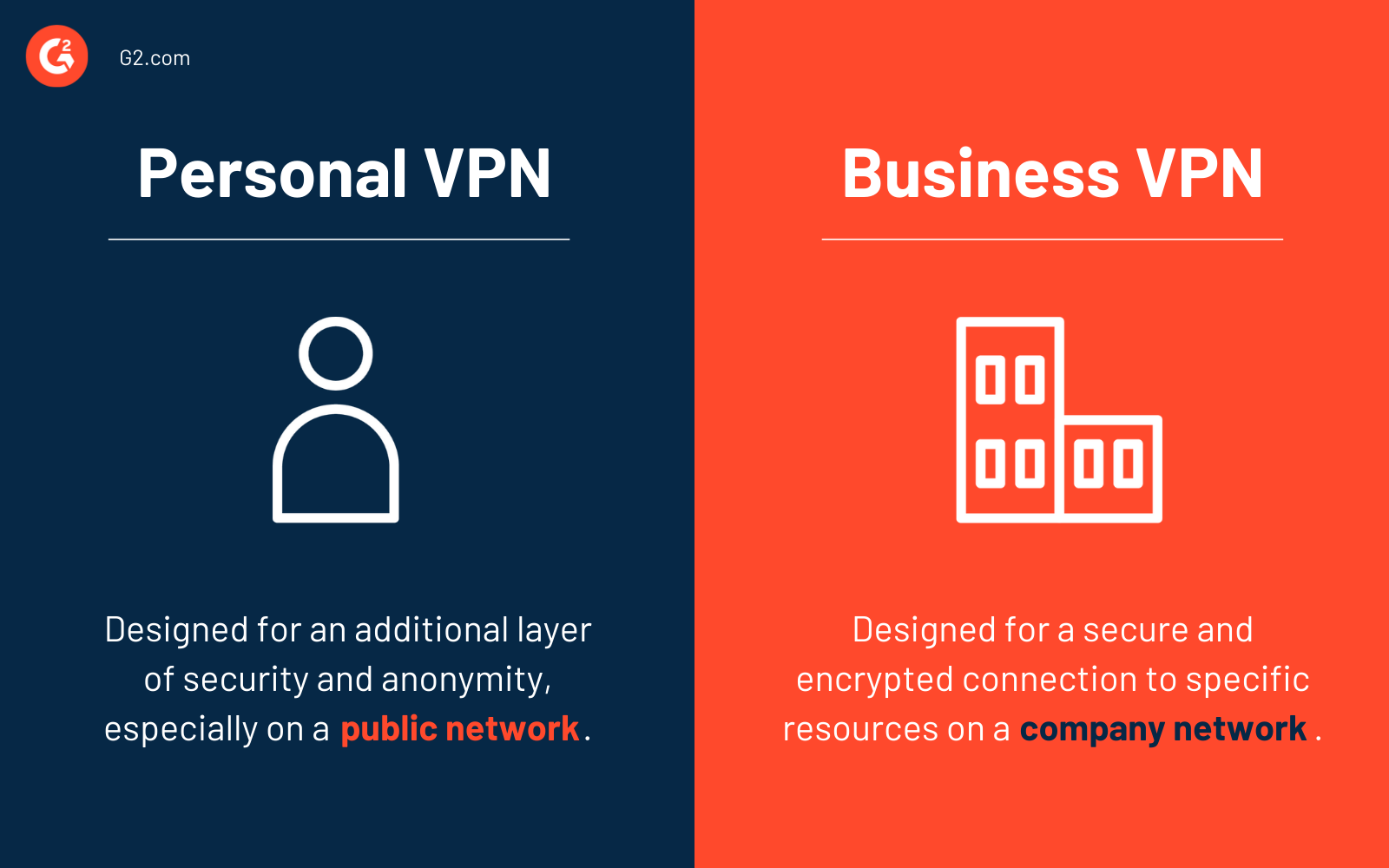
Personal VPN vs. business VPN
It’s important to note that there are some key differences between a personal VPN and a business VPN.
As the name would imply, a personal VPN is one that you would use at home or when conducting personal matters. For instance, you would use a personal VPN when you’re using a public WiFi network. The same can be said if you’re trying to access a geo-restricted YouTube video.
A business VPN, sometimes also called a corporate VPN, provides the opportunity for employees of a specific organization to utilize a secure end-to-end encrypted connection to cloud resources on a company network.
2. Site-to-site VPN
A site-to-site VPN also referred to as router-to-router VPN is used mostly by large companies or organizations that have offices in different locations. This allows these companies to connect the network of one office location to the network of another office location.
Think of this as an imaginary bridge between the two networks that connect them to the internet while remaining a secure and private connection.
Within site-to-site VPNs, there are two ways to go about this:
- Intranet-based VPN: When several offices of the same company are connected using a site-to-site VPN.
- Extranet-based VPN: When companies use site-to-site VPNs to connect to the office of another company.
When a site-to-site VPN is used, one router acts as the VPN client, and another router is used as a VPN server since this type is based on router-to-router communication. When authentication is complete between the two routers, communication can begin.
How to choose the right VPN
There’s no denying that the VPN market is crowded with options, so when choosing a VPN software, ask yourself these questions:
- Why do you need a VPN? Are you looking to secure your home or workplace? What sort of online activities will you be doing that require a VPN? Streaming movies? Working online while traveling?
- What qualities am I looking for in a VPN? Will the VPN need to support more than one connection? Do you want speed? Anonymity? Better encryption?
- Which VPN tools have those items on my wishlist? Weed out the options that can’t provide you with what you need. Take special note of the VPN protocol – it will determine the levels of encryption and security.
- What’s your budget? See what you can afford. The more capabilities a VPN has, the more expensive it will typically be.
VPN protocols
The two VPN types are based on six different VPN security protocols. Each VPN protocol provides users with different features and levels of security depending on their needs.
- Internet Protocol Security: Otherwise known as IPSec, this protocol is used to secure all internet communication across an IP network. This is done by authenticating the session and encrypting each data packet during the connection. This protocol can be used in conjunction with others to increase security.
- Layer 2 Tunneling Protocol: L2TP is a tunneling protocol that is usually combined with IPSec to create an extremely secure VPN connection. This is done by building a tunnel between two L2TP points of connection and the IPSec protocol to encrypt the data and safeguard the communication between the tunnel.
- Point-to-Point Tunneling Protocol: PPTP is one of the most commonly used VPN protocols. It builds a tunnel and encloses the data packet. It uses a point-to-point protocol (PPP) to encrypt the data between the connection.
- Secure Socket Layer and Transport Layer Security: SSL and TLS create a specific VPN connection where the web browser acts as the client, and the user access is restricted to certain applications instead of the entire network. This protocol is mainly used by online shopping websites and service providers.
- OpenVPN: OpenVPN uses a custom security protocol based on SSL and TLS protocols. It’s an open-source VPN that is useful for creating point-to-point and site-to-site connections.
- Secure Shell: SSH creates a VPN tunnel where the data transfer happens, ensuring that the tunnel is encrypted correctly. This protocol transfers data from a local port on a remote server through the encrypted tunnel.
Best VPN software
While different online service like Proxy enables you to hide your IP address and reroute internet traffic, VPNs come with the whole package to ensure extra security and privacy.
Whether you are using the internet for online shopping or accessing your company resources as a remote worker, let a VPN take care of mitigating any risk of a data breach or possible lawsuit that may follow.
To be included in our VPN software category, a product must:
- Use encryption and security systems to connect devices to private networks.
- Restrict access to private networks and sensitive data exclusively for authorized personnel.
- Identify network traffic at the packet level to encode sensitive data.
- Use tunneling protocols to route connections to safe networks.
* Below are the 10 leading VPN software from G2’s Winter 2023 Grid® Report. Some reviews may be edited for clarity.
1. NordVPN
NordVPN helps companies keep their network and internet connections safe by adding an extra layer of protection to secure all communication. Thanks to strong encryption that’s applied to all incoming and outgoing traffic, no third parties can access confidential information.
What users like:
“Providing the best secure gateway, NordVPN has come a long way to enable us to feel free in this age of trust issues. It not only provides a no-log policy, but it also gives total protection while surfing the internet. One account can be used for many devices for shield purposes. With a very reasonable package, it gives access to every different version of geo-block content and widens the views.”
- NordVPN review, Jeremy P., April 07, 2020
What users dislike:
“Occasionally I have observed some connectivity issues with specific servers. Also, NordVPN's pricing plans may be more expensive than other VPN providers, so that seems to be a little bit problematic to me."
- NordVPN review, Abhijeet S., March 22, 2023
2. Absolute Secure Access
Absolute Secure Access is an enterprise VPN that lets users safely access crucial resources in a public cloud and secure confidential information. The software suite has three products, Absolute VPN for securing data in motion, Absolute ZTNA for keeping away unauthorized users, and Absolute Insights for monitoring and improving the remote work experience.
What users like:
“Absolute Secure Access really makes it easy for our users to access business resources out in the field. Most of our users continually monitor business systems and need constant communication with those systems. Absolute Secure Access makes this process seamless and frustration-free.”
- Absolute Secure Access review, Micheal W., Feb 09, 2023
What users dislike:
“The initial learning curve is a bit overwhelming, but I suggest taking their outstanding certificate class which will have you creating policies in no time!”
- Absolute Secure Access review, Mike S., February 10, 2023
3. pfSense
pfSense is an open-source firewall and routing software. Based on the FreeBSD operating system, this network security solution is ideal for personal and professional use. It has a web-based user interface and several features like network address translation (NAT), anti-spoofing, application blocking, SSL encryption, multi-language support, and more, which gives it an advantage over other commercial solutions.
What users like:
“The amount of power and flexibility pfSense brings to your network is outstanding. The integrated VPN ability means connecting to my network from the outside is easy and doesn't require additional hardware. The complete control over how packets flow to and from the internet, and even across LANs; means I have a control that lets me keep my network running efficiently and securely. If you're used to dealing with just the hardware your provider gives you, pfSense is a significant step up.”
- pfSense review, Jay M., February 26, 2023
What users dislike:
“The main downside for me is that it does take a little bit of time to become familiar and comfortable with the tool, but even this is a minor quibble since this is true of any technology. Since documentation is robust and freely available, the only cost is the time it takes to read and understand it.”
- pfSense review, Dorian D., March 20, 2023
4. ExpressVPN
ExpressVPN provides users with an easy-to-use and high-speed VPN that is ultra-secure. Plus, with instant setup and unlimited bandwidth on up to five devices, you can be sure that you’re protected from attackers.
What users like:
“It is easy to log on to it and it runs in the background, causing no slow down to internet speed. It turns on by itself so you don't even need to think about it after you install it."
- ExpressVPN review, Angeline H., May 20, 2022
What users dislike:
“Occasionally there are connection issues with the laptop version. This happens when the laptop "falls asleep". The VPN then has difficulty reconnecting and sometimes has to be "repaired" using the Add/Delete Apps function in Windows.”
- ExpressVPN review, John S., July 5, 2022
5. Perimeter 81
Perimeter 81 is a cloud-native security service that lets organizations safely access resources, manage networks and reduce the risk of data breaches. The software hosts a range of features like multi-factor authentication, web filtering, automatic Wi-Fi protection, and identity management for a cyber-safe experience.
What users like:
“Simple and intuitive interface which is straightforward to use. Even a novice user and someone not well versed in cloud security can easily manage their account.”
- Perimeter 81 review, Himanshu D., November 14, 2022
What users dislike:
“Sometimes I try to connect to an external network and it does not allow me, I have to restart the machine and then I can connect to external networks through Perimeter 81.”
- Perimeter 81 review, Ronald B., May 24, 2022
6. ProtonVPN
ProtonVPN is designed with security as its main focus. It sends internet traffic through an encrypted tunnel, so passwords and confidential data stay safe even when used over a public or untrusted internet connection.
What users like:
“Easy to use, secure VPN tunneling from a reputable privacy-first company with an understandable business model that aligns to its users. Still offers a free option to protect all and also to demonstrate how the product works.”
- ProtonVPN review, Richard P. June 10, 2022
What users dislike:
“There are not many downsides to ProtonVPN; however, the paid plans are a little expensive in the current market. The prominent missing feature is split tunneling, where we can't select which apps to use VPN and which not to.”
- ProtonVPN review, Srivatsa V., March 06, 2023
7. OpenVPN Access Server
OpenVPN provides users with flexible VPN solutions to secure their data communications, whether it be for internet privacy, remote access for employees, securing IoT, or networking cloud data centers.
What users like:
“I like that it has frequent updates. The installation and setup is straightforward and fairly intuitive. There is plenty of documentation available to help along the way as well. It comes with a couple of free licenses for personal use so it satisfies my needs. It has a very easy client-side installer built into the server.”
- OpenVPN review, Rajat H., March 07, 2023
What users dislike:
“Sometimes client/employee profiles expire or stop working for no reason. It is very easy to fix but it still causes a minor annoyance from time to time. Other than that nothing stands out.”
- OpenVPN review, Wyatt H., May 13, 2022
8. NordLayer
NordLayer formerly known as NordVPN teams is a cloud-based network access security solution. It provides enterprises with several features like two-factor authentication (2FA), single sign-on (SSO), auto-connect, and jailbroken device detection to keep business activities out of prying eyes. The application is available to download for Windows, Mac, Android, iOS, and Linux.
What users like:
“NordLayer was easy to set up and manage for my team. We needed both the security of a VPN and a static IP for the whole team and NordLayer gives us both at a price that is in line with the competition.”
- NordLayer review, Steve K., Feb 23, 2023
What users dislike:
“On occasion, some of the servers you connect to will be slow, possibly they have many users connected or a lot of data passing through that server, but a quick reconnect fixes it right up.”
- NordLayer review, Michael M., Feb 23, 2023
9. Check Point IPsec VPN
Check Point IPsec VPN provides 60+ innovative security services to prevent multi-vector mega cyber attacks. They have a range of options for small, mid, and different-sized enterprises.
What users like:
“Check Point is a solid VPN platform with hardware and software optimization and outstanding administration capabilities. With cross features like hardware acceleration and ASIC, it makes this solution perfect for enterprise bank-level high security.”
- Check Point IPsec VPN review, Jose A., May 27, 2022
What users dislike:
“Need to use lots of debugging commands to fully troubleshoot some problems.”
- Check Point IPsec VPN review, Ozan D., July 20, 2022
10. Twingate
Twingate is a secure remote access solution, based on the modern zero-trust networking model. It uses four components namely the controller, clients, connectors, and relays to ensure only authorized users have access to the resources.
What users like:
“Twingate follows a zero-trust security model in which implementations are carried on with the least access privileges for our customer platform. It doesn't allow one single resource to take overall traffic control management independently for preventing network breaches and operates with node distribution strategies. We can regulate the user access authorization by implementing approval stages for sensitive decision-making and visibility enhancements.”
- Twingate review, Rithika G., March 16, 2022
What users dislike:
“There were some steps that we were not aware of in the beginning and navigating the documentation wasn't always intuitive. Specifically, the setup of non-FQDN hostnames/addresses and on-domain (AD) over Twingate was something to learn and didn't have an easy way to setup. Also, the client updates with non-admin users are rather clunky. I usually end up downloading the installation file again instead of using the built-in update functionality.”
- Twingate review, Bryan V., June 07, 2022
Every move you make, they’ll be watching you
There’s never been a better time to protect your right to online privacy, and using a VPN is a great place to start. No matter where you’re accessing the internet, and what you feel like doing, a VPN can ensure that no one is watching and that your data is kept away from prying eyes.
Take the next step and learn how to set up a VPN so your identity and data remain secure.
This article was originally published in 2019. The content has been updated with new information.

Mara Calvello
Mara Calvello is a Content and Communications Manager at G2. She received her Bachelor of Arts degree from Elmhurst College (now Elmhurst University). Mara writes customer marketing content, while also focusing on social media and communications for G2. She previously wrote content to support our G2 Tea newsletter, as well as categories on artificial intelligence, natural language understanding (NLU), AI code generation, synthetic data, and more. In her spare time, she's out exploring with her rescue dog Zeke or enjoying a good book.
