Hackers are evolving continuously, and so are their methods.
With the changing cybersecurity landscape, hackers have nudged their creativity to develop new strategies for cyber attacks. Security breaches are more frequent and technologically equipped now than they were a decade ago.
The growing popularity of modern hacking tools is fueling such incidents. So when attackers adopt cutting-edge technology to hamper your organization's reputation, you need to respond and act accordingly. The penetration testing process helps you discover blind spots that hackers can use to breach your cybersecurity framework.
What is penetration testing?
Penetration testing (or pen testing) is a method to delve into your IT environment and identify how a hacker can exploit the exposed vulnerabilities. It's commonly called ethical hacking, as it involves your pen testers mimicking the hacker's act but with permission.
But for it to be effective, you need to be proactive and consistent. Using technology like penetration testing tools and vulnerability scanner software will help you manage the vulnerabilities you’ll encounter.
The first step is to scan your IT infrastructure for security vulnerabilities. Once the vulnerability assessment is completed, you can leverage pen testing to identify ways a hacker can exploit your environment's weaknesses and build a robust vulnerability management program.
Not only does it help you improve your security posture, but it also allows you to prioritize vulnerabilities based on the possible risks associated with them. Furthermore, it ensures that your testing framework meets the requirements of different compliances.
Why do you need penetration testing?
Pen testing involves examining all your possible attack surfaces before a real cyberattack. It's imperative to have it in continuous cycles as it shields your security framework from becoming a costly liability. You might have come across a popular saying: the best defense is a good offense; pen testing complements it in the cybersecurity landscape.
Enables you to unveil critical security flaws
The best way to protect your IT environment from attackers is to detect your weaknesses before they can. Penetration testing does that by identifying the vulnerabilities first and then finding ways to exploit them just as a hacker would. This enables you to shield your IT assets from possible attacks.
As it involves scanning your network, systems, operating system (Mac OS, Microsoft Windows, Linux, etc.), and applications, it uncovers the critical vulnerabilities that could compromise your security. Not only does it empower you to detect security weaknesses better, but it also unveils the hidden ones, like those in people by social engineering techniques.
You can predict the extent to which your organization's vulnerabilities can be exploited and can take measures accordingly.
Allows you to prioritize remediation of severe vulnerabilities
As penetration testing examines the extent of a possible attack, it helps you prioritize remediation and enables you to devise short-term and long-term plans. After a well-conducted penetration test, you won't be blind-sighted to the impact and ease of exploiting your organization's security weaknesses. This would enable you to remediate the most severe vulnerabilities strategically and guide your team, empowering you to be a better leader in your organization.
Assists you in developing robust security measures
While testing your network, system, and applications, security researchers come across many gaps in your security measures and protocols. A summary of these helps you bridge these gaps proactively and contribute to building cyber resilience.
Penetration testing experts will also provide you with actionable insights and recommendations on eliminating such security weaknesses, enabling you to revamp your existing security protocols and processes.
Helps you comply with security regulations
With data security being a prevalent concern, you must adhere to security standards such as PCI, HIPAA, GDPR, ISO 27001, and others while serving end-users in their scope. The governing authorities expect you to conduct audits regularly to ensure compliance, and in case of non-compliance, you would be liable to pay hefty fines.
Penetration testing helps you comply with these regulations by evaluating your IT asset management practices and safeguarding the integrity of the stored data. It would debar hackers from scavenging the stored data and create an unbreachable security framework that adheres to compliance standards.
Want to learn more about Penetration Testing Tools? Explore Penetration Testing products.
Major approaches to penetration testing
There are three major approaches to conducting penetration testing. These are as follows:
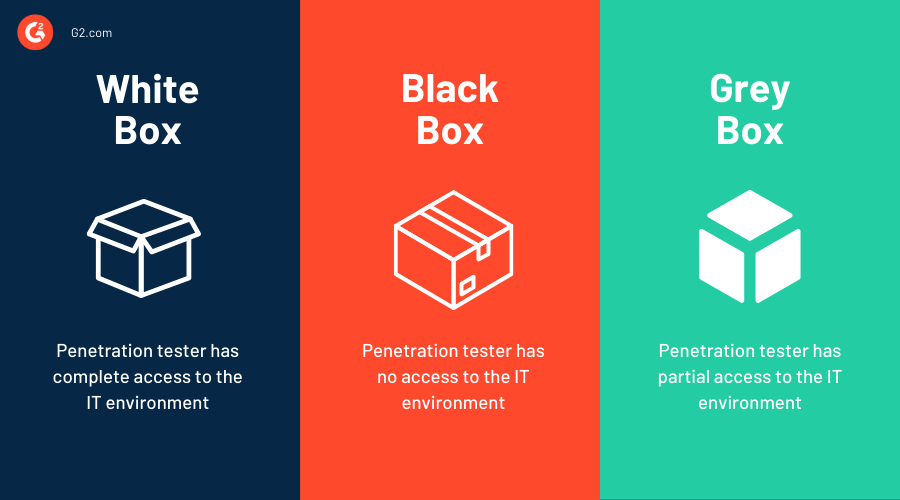
White box penetration testing
White box tests are those where the organizations share the information of an application or system and ask security researchers to identify exploitable vulnerabilities. Here, the penetration tester has complete access to source code and the environment, which helps them conduct an in-depth analysis and produce detailed results.
These tests usually take around two to three weeks, based on the width of your organization's IT infrastructure. Even though it produces detailed analysis, it sometimes gets complicated to identify the focus area, taking into account the given level of access.
Black box penetration testing
In black box tests, organizations do not share their security information with security researchers and allow them to dig into their network and identify vulnerabilities independently. The main objective of this approach is to mimic a real-world cyber attack, where the ethical hacker assumes the role of an anonymous hacker.
Black box penetration testing demands a high technical expertise level and can normally take up to six weeks to complete. They are generally costly, as the security professional has to plan, execute, and report the test result with no starting point.
Grey box penetration testing
In grey box pen tests, the security professional has partial access to the network or web application. The primary benefit of conducting a grey box pen test is the focus and efficiency you get in the security assessments. It's targeted and more effective in filling the security gaps and prioritizing the imminent security remediation.
6 types of penetration tests
There are six types of penetration tests that would collaboratively provide 360-degree security to your organization's IT infrastructure. Let's dive deeper into understanding each one of them in detail.
1. Network services penetration test
Network services penetration tests involve examining your network devices, such as LANs, switches, and routers. It's possibly the most common penetration test in the industry. Experts recommend conducting both internal and external network tests at least once annually.
2. Web application penetration test
The web application penetration test scrutinizes web-based applications for exposed weaknesses that can put your cybersecurity at risk. In addition to testing applications, the test also finds vulnerabilities in databases, browsers, and their components, such as plugins, java scriptlets, and more. These tests are targeted and detailed and are carried out by identifying every touchpoint of the application with the user and examining it for flaws.
3. Client-side penetration test
You can conduct these tests to identify possible attacks on client-side applications or programs such as web browsers, email clients, multimedia flash players, and others. These detect attack vectors such as cross-site scripting, HTML injection, open redirections, and others.
4. Social engineering penetration test
You can conduct a social engineering penetration test by copying a hacker's act in retrieving sensitive information from internal users through phishing, tailgating, or others. These tests allow you to train your internal team better and always keep an eye out for malware and any fraudulent activity.
5. Wireless penetration test
These tests involve examining your IT assets connected with one another and the internet. The scope of these tests includes investigating your laptop, PCs, and other IoT-enabled devices in your IT infrastructure. You should perform these tests in the office so that you can have access to the WiFi network.
6. Physical penetration test
In such tests, the security professional attempts to overcome physical barriers to reach your organization's IT assets and employees. These tests expose flaws in the physical barriers (such as locks, sensors, etc.) and recommend proper measures to strengthen your business's security posture.
How to do penetration testing?
Performing a penetration test in an organization is a six-step process. You can execute these steps to build a scalable and repeatable penetration testing process in your company.
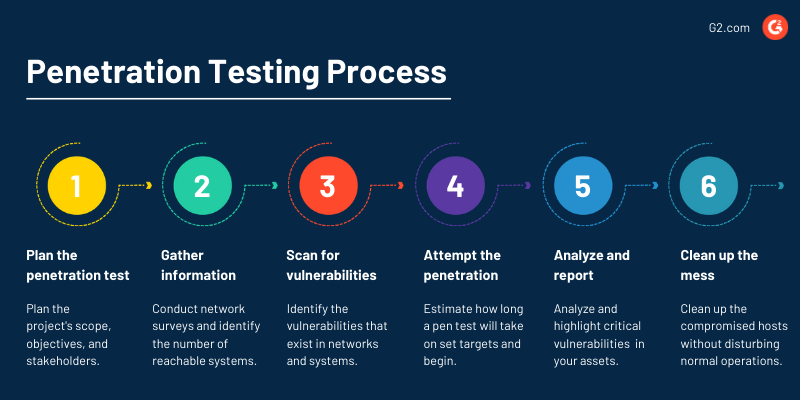
Plan the penetration test
Conducting a penetration test requires a great deal of preparation. It's advisable to call a kickoff meeting with the security professionals to decide the project's scope, objectives, and stakeholders. It would also help if you fixed a timeline for these tests, as you don't want to disturb the company's everyday operations amid the testing.
During the tests, there is a possibility that some systems may crash due to inflated network traffic. You can exclude those systems from the scope to prevent such incidents. In the planning phase, it is vital to decide whether the staff needs to be informed.
Complete penetration testing involves breaching a network/system illegally. You must ensure that you have obtained legal clearance from the company before conducting the test, as it protects the company's interest and prevents the tester from legal action.
Gather information
After planning the penetration test, the next step is to gather information. You can conduct network surveys and identify the number of reachable systems. Here, you can expect the domain names, database server names, ISPs, host IP addresses, and a network map as a result of the survey.
Once you have completed the network survey, you can move on to port scanning. Now you have to detect the open and closed ports in the network. This is also the place where you exclude those ports which the organization doesn't want to test.
Scan for vulnerabilities
Now that you have gathered sufficient information about the systems, the next step is to identify the vulnerabilities that exist in those systems. You can use vulnerability scanning tools to automate this process and prepare a list of vulnerabilities to target closely.
Vulnerability scanners prepare the list of vulnerabilities automatically and prioritize them based on the risk score. This enables you to target those that can have a higher impact on your cybersecurity or those that are easier to exploit.
Attempt the penetration
Once you have identified the vulnerabilities, the next step is to attempt the penetration test. Now before moving ahead with it, you must estimate how long a particular pen test will take and what the targets will be.
Even if vulnerabilities exist, it does not imply that they can be exploited easily. It might take a lot of effort and time to yield benefits for the attacker. So you can manage them in the long-term plan, whereas vulnerabilities that are easy to exploit and pose a considerable risk should be taken up as a priority.
These days password cracking is normal practice in penetration tests. You have services like telnet and file transfer protocol (FTP) running on systems, making it a good place to start and use a password cracker. You can use a dictionary attack (using a word list of dictionary files), hybrid crack (using a variation of words in a dictionary file), or brute force (testing passwords made up of characters going through all the combinations possible).
It doesn’t end here. You have two more areas with which you can penetrate the company's security. You can do it by social engineering or by bypassing physical security. You have to check these as well to conduct a comprehensive penetration test.
Analyze and report
Once you have completed all the steps mentioned above, the subsequent step is reporting. Your report starts with an overview of penetration testing. Moving forward, you can highlight the most critical vulnerabilities that could substantially impact the company. Then, you state the less critical ones.
The sole reason for separating the vulnerabilities into critical and less critical is to help organizations make decisions. Altogether, your report should cover a summary of the process, a comprehensive list of information gathered, a list of vulnerabilities, their description and suggestions, and recommendations for the remediation process.
Clean up
The last step of the penetration testing process is cleaning up. You have to clear the mess that might have come up during the pen test. Then, you should execute the cleaning up of compromised hosts securely so that you don't affect the organization's normal operations. It's the penetration tester's responsibility to inform the organization about the changes that were created during the penetration test and revise them back to normal.
Tip: For effective penetration testing, consider having someone with no prior knowledge of your system conduct the test. This approach can help uncover blind spots that developers may have overlooked. That's why ethical hackers are hired to intentionally breach the system—with permission—aiming to enhance overall security.
What happens after a penetration test?
After completing a pen test, the ethical hacker will share their findings with the target company’s security team. This information can then be used to implement security upgrades to address any vulnerabilities discovered during the test.
For web applications, these upgrades can include rate limiting to control the flow of requests, new Web Application Firewall (WAF) rules to filter out malicious traffic, and DDoS mitigation strategies to protect against denial-of-service attacks. Additionally, tighter form validations and data sanitization practices can help prevent injection attacks and ensure that user input is safe.
For internal networks, upgrades may involve deploying a secure web gateway to monitor and control internet traffic or transitioning to a zero-trust security model, which assumes that threats could be internal as well as external and requires strict identity verification for every person and device trying to access resources.
If the ethical hacker used social engineering tactics to breach the system, the company may need to enhance employee training programs to better educate staff on recognizing phishing attempts and other deceptive practices. Furthermore, reviewing and upgrading access control systems can prevent lateral movement within the network, ensuring that even if one account is compromised, it cannot easily be exploited to access other critical systems.
Incorporating solutions from providers like Cloudflare can further strengthen defenses. Cloudflare secures companies' applications, networks, and personnel through a combination of web application security solutions and a Zero Trust security platform, providing robust protection against evolving cyber threats. By leveraging these strategies and tools, organizations can enhance their overall security posture and minimize the risk of future breaches.
Types of penetration testing tools
Penetration testing tools are technological interventions that security professionals need to perform different types of penetration testing. Whether open-source or licensed, you can use these pentest tools according to the type of test you are conducting.
Let's look into the types of penetration testing tools available.
Port scanners
Port scanners are security tools that are designed and equipped for probing a server or host for open ports. These can be used by administrators to identify and verify the network security policies. Besides, attackers can also use it to detect the type of network services running on the target and plan their attacks accordingly.
Port scanners typically gather information and data about the host in the network environment remotely. This tool can detect both TCP (Transmission control protocol) and UDP (user datagram protocol) ports.
It also gives you the freedom to conduct probing activities like the SYN, SYN-ACK, ACK sequence (three-way handshake in TCP ports), half scans, and more.
Port scanning techniques
- Ping scan: This is the simplest of all port scanning techniques. It includes an automated blast of pings (ICMP - Internet Control Message Protocol) at different ports to identify those that respond. Admins usually disable ping on the firewall or the router, but then it makes it difficult to troubleshoot network problems.
- TCP half-open scan: This technique is sometimes referred to as a SYN scan. Here the scan sends a SYN message and expects a SYN-ACK response from the open ports. But the scanner doesn't complete the connection once it gets the response. This method is widely used by attackers to identify the targets.
- TCP connect: This technique is similar to half-open, but the connection is completed once the scan gets a response from the open port. Since the connection is completed, you would be increasing the network's noise and may trip an alarm, unlike a half-open scan.
- Stealth scan: This technique is even quieter than others. The scan sends data packets to ports with a FIN flag and expects a no-response (open port. If you get a RST, the port may be closed. Firewalls are looking for SYN packets, so FIN often goes undetected.
Vulnerability scanners
Vulnerability scanning tools detect and identify the known vulnerabilities present in your IT environment. They identify the CVEs (Common vulnerabilities and exposures) and cross-check with one or more vulnerability databases like the NVD (National Vulnerability Database) and so on.
Vulnerability scanning tools help you detect vulnerabilities with their risk measure quantified by the common vulnerability scoring system (CVSS), enabling you to prioritize remediation efficiently. The scan helps you ensure that your IT assets adhere to the compliances and the organization's latest security policies while helping you mitigate cyber attacks.
Application scanners
Application scanners evaluate security vulnerabilities across web applications. They help you identify cookie manipulation, cross-site scripting, SQL injections, and other backdoors and threats that an attacker can use to exploit your application vulnerability.
Web application assessment proxies
You can place this tool in between the penetration tester's browser and the target web server to closely see and evaluate the exchange of information going on in real-time. With this, you can manipulate the hidden HTML fields to gain access to the system.
Altogether, the tool allows you to keep and maintain the focus on information and data flow at a much closer level.
Best penetration testing tools
Penetration testing tools help you mimic a cyberattack by exploiting vulnerabilities and security gaps in your IT infrastructure. They allow you to explore different ways a hacker can take advantage of flaws in your network or system and empower you to fix them before they can be of illicit use.
The list below contains real user reviews from the best penetration testing tools on the market. To be included in this list, a product must:
- Simulate cyberattacks on computer systems or applications
- Gather intelligence on potential known vulnerabilities
- Analyze exploits and report on test outcomes
* Below are the five leading penetration testing tools from G2's Fall 2024 Grid® Report. Some reviews may be edited for clarity.
1. vPenTest
vPenTest is an automated network penetration testing platform that allows you to see the vulnerabilities in your network before the hackers. It makes it easy for organizations to continuously monitor and evaluate their cybersecurity risks in real time.
What users like best:
"Vonhai vPEN has provided me with a multi-tenant leading class enterprise solution for a simple platform that tests both internal and external ports that clients have never been aware of and networking changes that have been made without our knowledge! The amount of time that I am able to get this scheduled, receive my results, and present our findings to clients. It creates a phenomenal process that allows for quick and efficient information gathering and reporting.
With this solution, you are also allowed to test and calculate a total IP count prior to any true scans to know how many IPs you would be testing to best prepare for spending your usable IP count. I would consider vPen as a leader in this service and definitely look forward to seeing what new tools they have for the future!
- vPenTest Review, John H.
What users dislike:
"The biggest item is dislike about vPenTest is the manual setup for agents. The documentation is very clear on how to set up agents internally, but with how simple the overall tool is, it is a bit surprising they do not make it a more simple process."
- vPenTest Review, Nick M.
2. Pentera
Pentera is an automated security validation platform that allows every organization to test the integrity of all cybersecurity layers easily, unfolding true, current security exposures at any moment, at any scale. Thousands of security professionals and service providers around the world use Pentera to guide remediation and close security gaps before they are exploited. Its customers include Casey's General Stores, Emeria, LuLu International Exchange, and IP Telecom.
What users like best:
"Easy to use and configure. The UI is great, and the Dashboard gives you all the necessary information in one place. You can dig deep into the scans and are provided with not only the details but links to the CVE. You can schedule scans as you wish, and the service also automatically scans new zero-day vulnerabilities. It automatically generates reports that are emailed to you. These reports can be used to prove that you are actively monitoring for external threats and misconfigurations that can leave you vulnerable. Works on Cloud, Hybrid, and Stand-a-Lone Hardware Networks. We use this every day!"
- Pentera Review, Jerry H.
What users dislike:
It still doesn’t complete all the black box phases, as it is designed with safety in mind and currently lacks techniques that could create significant impacts, such as buffer overflow attacks and other similar methods a true black hat would employ."
- Pentera Review, Felipe E.
3. Bugcrowd
Bugcrowd is more than just a crowdsourced security company, they are a community of cybersecurity enthusiasts united by a common purpose: safeguarding organizations from attackers. By connecting customers with the right trusted hackers through an AI-powered platform, they empower them to take back control and stay ahead of even the most vulnerable threats.
What users like best:
"Their account team has been instrumental in developing our disclosure program over time, with the goal of evolving it into a comprehensive bug bounty program. They effectively identify and engage the right researchers to handle disclosures while minimizing duplicate submissions through their triage team. The account team is also flexible and generous in their pricing, fostering a strong partnership and ensuring they remain our vendor of choice for the long term."
- Bugcrowd Review, Jack E.
What users dislike:
"One area for improvement for Bugcrowd is enhancing the communication and feedback loop between researchers and program owners. Occasionally, response times and the clarity of feedback can be inconsistent, which may frustrate researchers seeking timely and detailed guidance on their submissions."
- Bugcrowd Review, Jitmanyu S.
4. The NetSPI Platform - Penetration Testing as a Service (PTaaS)
NetSPI's PTaaS (Penetration Testing as a Service) is a comprehensive solution that combines expert personnel, proven processes, and advanced technology to provide real-time, contextualized security assessments. It allows organizations to access over 250 in-house security experts and utilize The NetSPI Platform for a full year, offering a variety of pen-testing services.
What users like best:
"What we appreciated most was the extensive guidance and support from the staff and leadership at NetSPI. We had numerous discussions about the scope of our initiatives, receiving valuable insights from Richard Booth and his team. The Resolve platform and dashboard are set to revolutionize the industry; it’s user-friendly and provides all the necessary information for effective management. The dashboard even includes a chat feature that connects directly with testers for immediate support. Overall, it’s a fantastic platform backed by a great company."
- NetSPI PTaaS Review, Timothy L
What users dislike:
"While the integrations are essential, they lack some functionality, particularly in terms of export options."
- NetSPI PTaaS Review, Zane G.
5. Cobalt
Cobalt offers a modern pentest as a service (PtaaS) platform that can be used in both standalone and complex environments. With its exclusive community of testers, Cobalt provides real-time insights to mitigate risk. It's a data-driven vulnerability management engine that allows companies to pinpoint, track, and remedy software vulnerabilities.
What users like best:
"Cobalt was able to turn around a pen test report for us very quickly as we required testing on very short notice. We found them to be very thorough, the testing was high quality, and the responsiveness was excellent in understanding our unique situation."
- Cobalt Review, Taylor J.
What users dislike:
"I wish there were easier ways to implement APIs for all our scheduling/management applications here at ISS. Also, ways to automatically create a slack channel with the submit pentest review button would be delightful to get members prepared before the test goes live."
- Cobalt Review, Sean T.
Get to the root of the problem
Penetration tests emulate a 'real-work' cyber attack, thus revealing the extent to which a hacker could exploit vulnerabilities. They would also make you aware of the security gaps that need to be bridged to shield your cybersecurity, provided that you are regular and proactive about it.
Hackers need only one gap to fulfill their shallow motives; make sure you don't leave them uncovered. You should take action to address those vulnerabilities and manage your security posture effectively.
Learn about static application security testing (SAST) and how it can help you improve the security of your applications.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.